Contents
Docs
General
- Introduction
- What is Android Enterprise?
- Considerations when migrating from device administrator to Android Enterprise
- Android Enterprise feature requests
- What is Android Enterprise Recommended?
- Android Enterprise FAQ
- Android Enterprise device testing
- What is Android One?
- Android Enterprise vs Device Admin: Why DA is no longer suitable
- Considerations for choosing Android in the Enterprise
- Feature spotlight: Android Smartlock
- Android glossary
- Android version evolution graphics
- Infobyte: Device Admin deprecation
- How to submit a device for Android Enterprise Recommended validation
- How to capture a bug report and device logs
- How to view software version information
- Gartner comparison of security controls for mobile devices 2019
Provisioning
- How to become a zero-touch enrolment reseller
- What is Android zero-touch enrolment?
- Android Enterprise zero-touch console administration guide
- Android Enterprise DPC identifier collection
- Android Enterprise provisioning guides
- Android Enterprise zero-touch DPC extras collection
- Infobyte: Android Enterprise deployment scenarios
- Infobyte: Android Enterprise fully managed provisioning methods
- Manual Android Enterprise work-managed QR code generation for MobileIron
Work profile
Fully managed
App management
- Set up Hypergate's Kerberos Authentication on MobileIron Core for Android Enterprise
- Managed Google Play, allowlist or blocklist?
- Considerations when deploying MTD with Android Enterprise
- Why you shouldn't install apps from unknown sources
- What is OEMConfig?
- Create and manage private apps for Android Enterprise
- Create and manage web apps for Android Enterprise
- How to locate a private Android app assigned to an organisation ID
- How to host enterprise apps outside of Google Play
- The Google Play iFrame app approval flow is deprecated
- Android 14 blocks apps targeting old Android versions
- Android 13 adds notifications access as a runtime permission
- How to resolve common Android app install failures (with errors)
FAQ
- Is Android Enterprise supported on uncertified (non-GMS) devices?
- Does Samsung support Android Enterprise?
- What versions of Android support Android Enterprise?
- Why has USB data access been disabled suddenly?
- How to check if an Android device is GMS/Play Protect certified?
- To use Android Enterprise do I need to buy Google Workspace (G Suite) and register my domain?
- What devices should I buy for my organisation?
- If Android Enterprise is supported from Lollipop, why is Marshmallow often mentioned instead?
- What’s the difference between Device Admin and Android Enterprise?
- What is the Android Enterprise bind?
- Can I change the account I used to bind Android Enterprise?
- Is it possible to bind Android Enterprise with multiple EMMs using one account?
- How do I remove the Android Enterprise bind from my current EMM?
- What is Android Enterprise Recommended?
- My AER device doesn’t work properly with Android Enterprise, what should I do?
- Is Android One better than AER? (Or the other way around?)
- How do I configure Google Workspace domains for provisioning?
- What’s the best provisioning method?
- What’s the difference between allow adding accounts vs allow configure credentials?
- Is it possible to utilise multiple VPN connections within a profile?
- Does Android support Kerberos natively?
- What’s the difference between device based accounts and user based accounts?
- How do I manage the new notifications runtime permission in Android 13?
- Can organisations see applications outside of the work profile?
- Can organisations deploy applications to the parent profile in a work profile deployment?
- Is it possible to migrate from DA to AE work profile without a re-enrol?
- What is a work challenge?
- Enrolment failed but the work profile was created. How do I remove it?
- How can I provision a fully managed device?
- Is it possible to “retire” (or enterprise wipe) a fully managed device?
- Devices factory reset as soon as they’re enrolled, why?
- Is Factory Reset Protection enabled on fully managed devices?
- Is it possible to migrate fully managed devices between EMM solutions?
- How has COPE changed in Android 11?
- Does Intune support COPE?
- Can organisations see applications outside of the work profile on a COPE device?
- Can organisations deploy applications to the parent profile in a COPE deployment?
- Is it possible to migrate from fully managed to work profiles on fully managed devices?
- How should system applications be handled on a COPE device?
- What OEMs currently support zero-touch?
- Where are zero-touch resellers located?
- Does zero-touch cost anything?
- Is an EMM still required with zero-touch?
- What happens if a fully set up device is added to the zero-touch console?
- What happens if a user starts setting up a device before the zero-touch config is applied?
- What happens if a zero-touch config is removed from an enrolled device?
- What happens if a new config for a different EMM or server is applied to an enrolled device?
- What happens if a zero-touch assigned device is reset?
- What happens if a device is unregistered from the zero-touch console?
- Can a device be OTA managed from the zero-touch console?
- Does enrolling via zero-touch slow down or cause any delay to the setup process while it’s retrieving the zero-touch config?
- What deployment scenario will a zero-touch device enrol under?
- Why does zero-touch require so much touching?
- Can anyone add a device to the zero-touch console?
- Is it possible for an organisation to add previously-purchased devices to zero-touch?
- Can a MADA device be converted to EDLA?
- Can anyone remove a device from the zero-touch console?
- Does Samsung support zero-touch?
- Is it possible to set a zero-touch default configuration?
- Is it possible to bulk update zero-touch devices?
- Is it possible to change zero-touch resellers?
- Are all zero-touch devices Android Enterprise Recommended?
- What are DPC extras?
- What should I put in DPC extras?
- What happens if a device is uploaded to zero-touch with the wrong manufacturer?
- The device registered with zero-touch, but doesn’t launch during setup, why?
- Does Android Go support zero-touch?
- Are employee-owned devices eligible for zero-touch?
- What’s the recommended way of managing in-house (private) applications?
- Is it possible to deploy app shortcuts to the homescreen of an Android Enterprise device?
- The Google Play iFrame is missing a feature in my UEM. How do I enable it?
- How do I configure allowlist/blocklist domains for Google Chrome?
- How to configure Chrome managed bookmarks
Support this site
Feature spotlight: Android Smartlock
Contents
A very common question I am asked, almost on every Android deployment I undertake in fact, is “what is Smartlock?”.
It is a commonly overlooked configuration within EMMs, due either to the fact organisations don’t know what it is, or that “smart” in the name gives the wrong impression and is therefore deemed safe.
A quick overview
#Smartlock is a convenience feature in Android that aims to reduce how often a device with a passcode enabled needs to be unlocked in situations where it could be deemed low risk. Some of these situations include:
- Trusted places
- Trusted accessories
- On-body detection
Used correctly it can indeed offer a balance between security and convenience in genuinely trusted environments, however although it can be controlled granularly via some UEM solutions in terms of the types of Smartlock available, it is still frequently subject to overuse or abuse.
Trusted places
#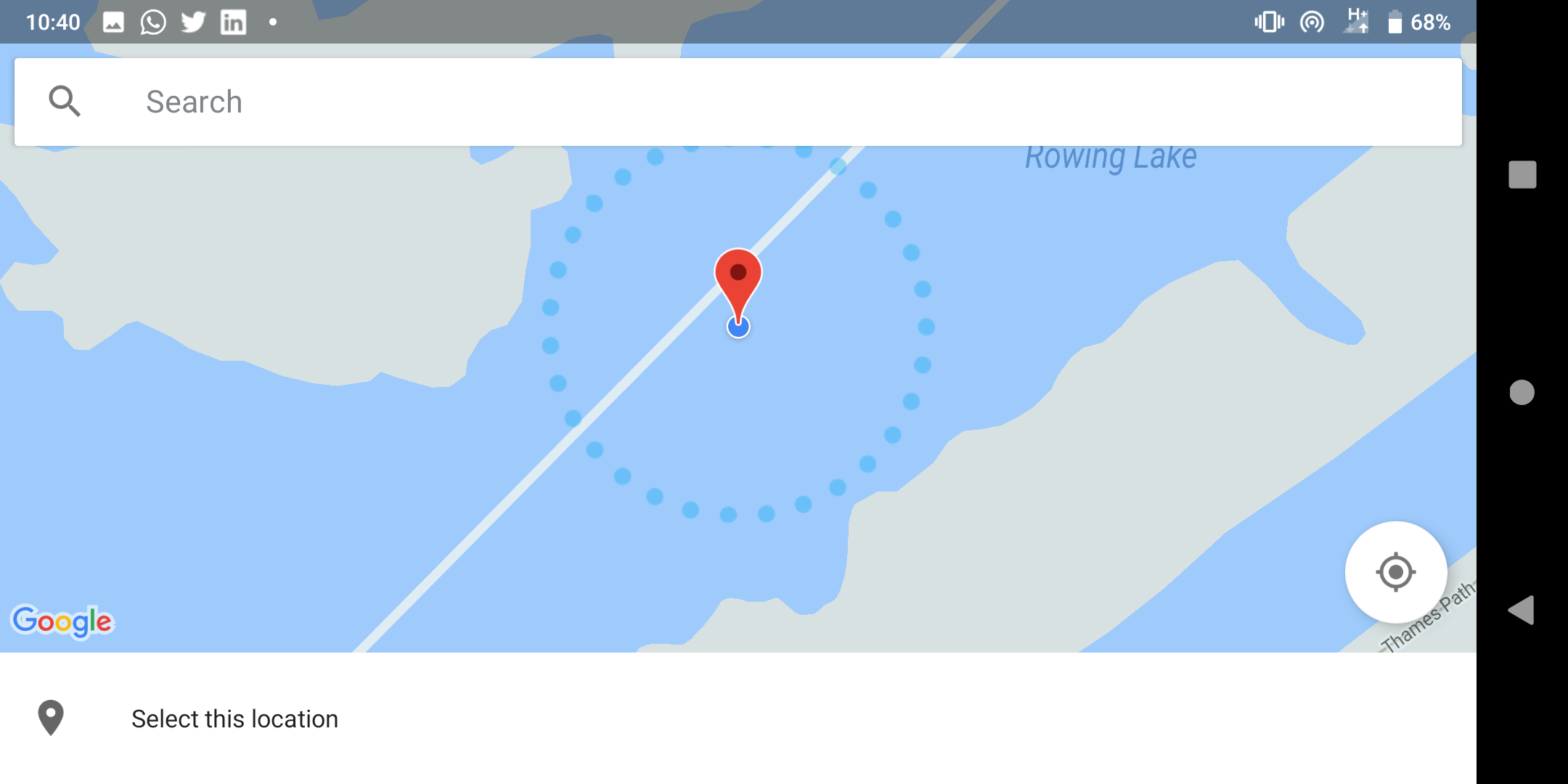 Selecting a trusted location on a map
Selecting a trusted location on a map
If you’re at home, at your parents or a close friend’s home, you’re in a location you trust. It’s unlikely (though not impossible) an unknown bad actor is going to walk into the living room and steal your phone.
It’s fair to assume with the environment considered safe, trusted, you might not need to make use of authentication to gain access to your device.
Herein lies the problem. End-users may select the coffee shop, the local library or the pub as locations where they frequent and don’t want to have their devices lock up.
It is up to the end-user to deem what scenarios are safe; any location in the world, plus a fixed radius around it, can be set as trusted. Not good.
When a device is not locked, it can be stolen and very easily accessed if it’s in a trusted location and this is therefore not a great idea for corporate devices.
Trusted accessories
#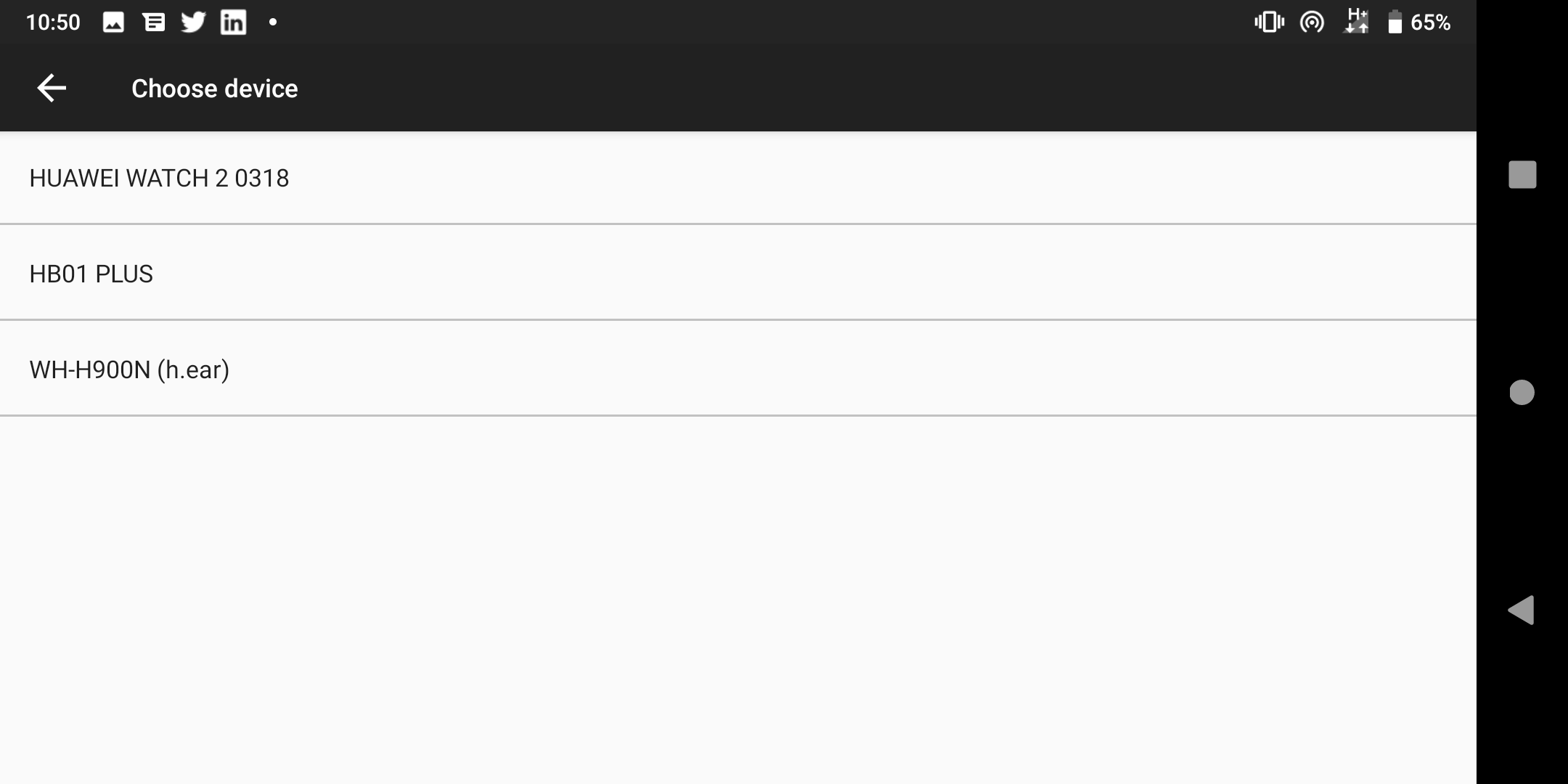 Selecting a trusted device from paired Bluetooth devices
Selecting a trusted device from paired Bluetooth devices
When entering a car, your device might automatically connect up to your Bluetooth system. When out for and about perhaps you have wireless headphones or at home connect up a keyboard and mouse wirelessly for typing up reports.
Trusted accessories allows you to reduce the frequency of inputting the passcode when a device is paired to particular Bluetooth devices.
Once again, since any Bluetooth accessory can be deemed trusted under any circumstance, if the device is stolen and unlocked within range of the Bluetooth accessory, the attacker will have full access to the device; in the case of an item such as a WearOS watch, it could remain unlocked for extended periods of time.
On-body detection
#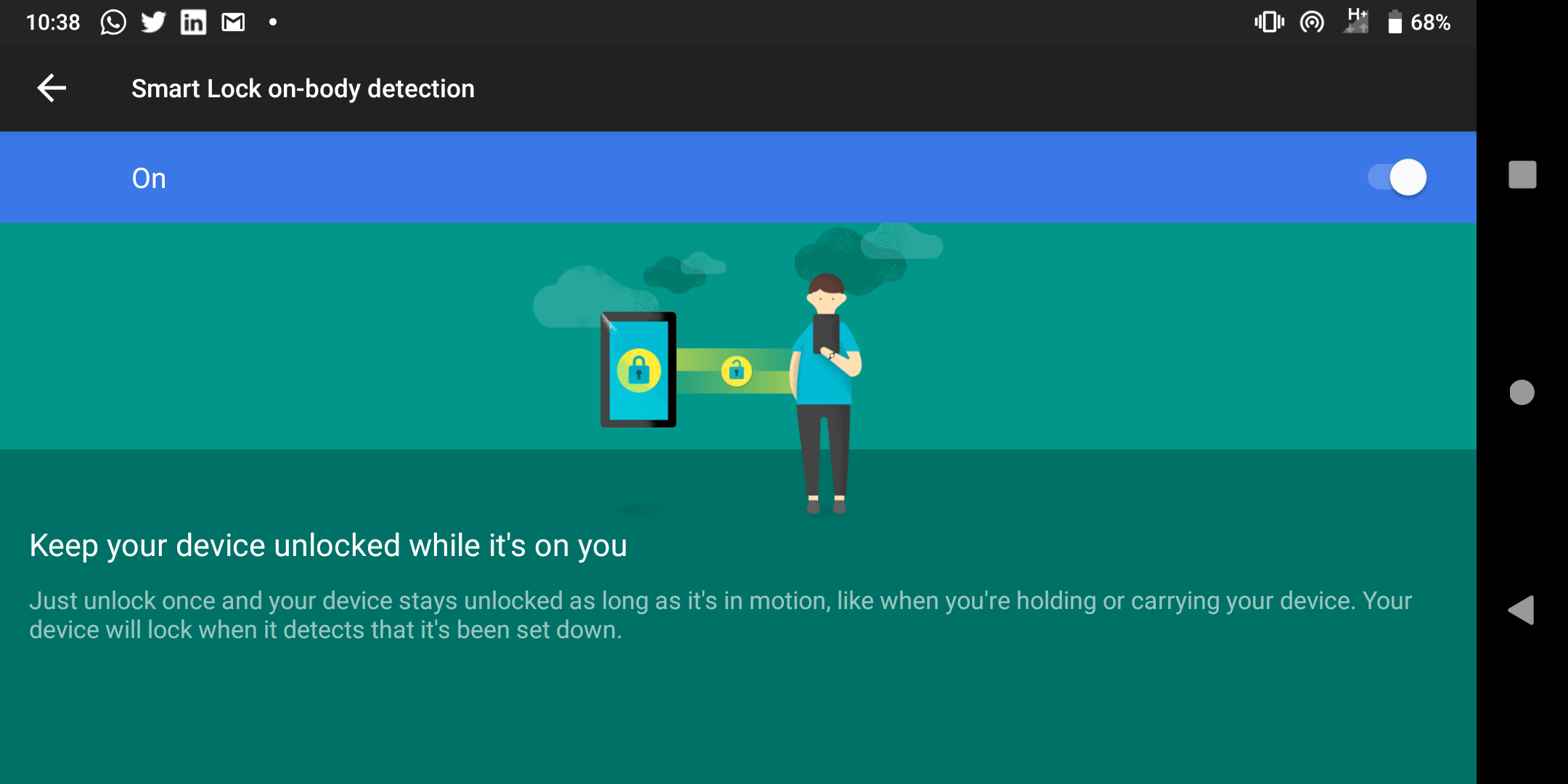 Enabling on-body detection
Enabling on-body detection
An Android device is exceptionally smart. It knows when it’s static, when it’s picked up and even when it’s in motion. Using the latter, if your device detects you moving, it can make the assumption it is on your person and therefore safe.
With on-body detection, as long as the device feels a movement that isn’t dissimilar to the typical bumps, jumps and shakes any device would feel in someone’s pocket or bag, it can remain unlocked.
The very obvious drawback is simply if a device is snatched out of a hand or bag while the end-user is in motion. Whilst the attacker remains in motion, the device remains unlocked, easily accessed for a decent amount of time after the fact.
Why Smartlock is not a great idea
#With the above situations, it is clear Smartlock can be easily taken advantage of by an attacker. For a business device, this risk is absolutely not worth taking for any devices, not least those known to hold sensitive data.
It is with that in mind that Smartlock should therefore be disabled as a matter of course for managed devices. The convenience does not outweigh the very real security risk of leaving it enabled.
Smartlock can be disabled across all modern UEM solutions either in part (on an individual basis) or entirely:
Disabling Smartlock for Workspace One UEM
#Referred to as Keyguard Trust Agent State
Disabling Smartlock for MobileIron Core
#
Disabling Smartlock for Maas360
#Again referred to as Allow Trust agents. Do take note of where this setting is as by default the policy opens within Android Settings and not Android Enterprise Settings.
Conclusion
#If your organisation allows the use of Smartlock today, consider turning it off sooner rather than later. It is a common feature popular among Android users so do expect to justify its disablement, however hopefully the above will provide the necessary information for organisations to do just that.
Docs
General
- Introduction
- What is Android Enterprise?
- Considerations when migrating from device administrator to Android Enterprise
- Android Enterprise feature requests
- What is Android Enterprise Recommended?
- Android Enterprise FAQ
- Android Enterprise device testing
- What is Android One?
- Android Enterprise vs Device Admin: Why DA is no longer suitable
- Considerations for choosing Android in the Enterprise
- Feature spotlight: Android Smartlock
- Android glossary
- Android version evolution graphics
- Infobyte: Device Admin deprecation
- How to submit a device for Android Enterprise Recommended validation
- How to capture a bug report and device logs
- How to view software version information
- Gartner comparison of security controls for mobile devices 2019
Provisioning
- How to become a zero-touch enrolment reseller
- What is Android zero-touch enrolment?
- Android Enterprise zero-touch console administration guide
- Android Enterprise DPC identifier collection
- Android Enterprise provisioning guides
- Android Enterprise zero-touch DPC extras collection
- Infobyte: Android Enterprise deployment scenarios
- Infobyte: Android Enterprise fully managed provisioning methods
- Manual Android Enterprise work-managed QR code generation for MobileIron
Work profile
Fully managed
App management
- Set up Hypergate's Kerberos Authentication on MobileIron Core for Android Enterprise
- Managed Google Play, allowlist or blocklist?
- Considerations when deploying MTD with Android Enterprise
- Why you shouldn't install apps from unknown sources
- What is OEMConfig?
- Create and manage private apps for Android Enterprise
- Create and manage web apps for Android Enterprise
- How to locate a private Android app assigned to an organisation ID
- How to host enterprise apps outside of Google Play
- The Google Play iFrame app approval flow is deprecated
- Android 14 blocks apps targeting old Android versions
- Android 13 adds notifications access as a runtime permission
- How to resolve common Android app install failures (with errors)
FAQ
- Is Android Enterprise supported on uncertified (non-GMS) devices?
- Does Samsung support Android Enterprise?
- What versions of Android support Android Enterprise?
- Why has USB data access been disabled suddenly?
- How to check if an Android device is GMS/Play Protect certified?
- To use Android Enterprise do I need to buy Google Workspace (G Suite) and register my domain?
- What devices should I buy for my organisation?
- If Android Enterprise is supported from Lollipop, why is Marshmallow often mentioned instead?
- What’s the difference between Device Admin and Android Enterprise?
- What is the Android Enterprise bind?
- Can I change the account I used to bind Android Enterprise?
- Is it possible to bind Android Enterprise with multiple EMMs using one account?
- How do I remove the Android Enterprise bind from my current EMM?
- What is Android Enterprise Recommended?
- My AER device doesn’t work properly with Android Enterprise, what should I do?
- Is Android One better than AER? (Or the other way around?)
- How do I configure Google Workspace domains for provisioning?
- What’s the best provisioning method?
- What’s the difference between allow adding accounts vs allow configure credentials?
- Is it possible to utilise multiple VPN connections within a profile?
- Does Android support Kerberos natively?
- What’s the difference between device based accounts and user based accounts?
- How do I manage the new notifications runtime permission in Android 13?
- Can organisations see applications outside of the work profile?
- Can organisations deploy applications to the parent profile in a work profile deployment?
- Is it possible to migrate from DA to AE work profile without a re-enrol?
- What is a work challenge?
- Enrolment failed but the work profile was created. How do I remove it?
- How can I provision a fully managed device?
- Is it possible to “retire” (or enterprise wipe) a fully managed device?
- Devices factory reset as soon as they’re enrolled, why?
- Is Factory Reset Protection enabled on fully managed devices?
- Is it possible to migrate fully managed devices between EMM solutions?
- How has COPE changed in Android 11?
- Does Intune support COPE?
- Can organisations see applications outside of the work profile on a COPE device?
- Can organisations deploy applications to the parent profile in a COPE deployment?
- Is it possible to migrate from fully managed to work profiles on fully managed devices?
- How should system applications be handled on a COPE device?
- What OEMs currently support zero-touch?
- Where are zero-touch resellers located?
- Does zero-touch cost anything?
- Is an EMM still required with zero-touch?
- What happens if a fully set up device is added to the zero-touch console?
- What happens if a user starts setting up a device before the zero-touch config is applied?
- What happens if a zero-touch config is removed from an enrolled device?
- What happens if a new config for a different EMM or server is applied to an enrolled device?
- What happens if a zero-touch assigned device is reset?
- What happens if a device is unregistered from the zero-touch console?
- Can a device be OTA managed from the zero-touch console?
- Does enrolling via zero-touch slow down or cause any delay to the setup process while it’s retrieving the zero-touch config?
- What deployment scenario will a zero-touch device enrol under?
- Why does zero-touch require so much touching?
- Can anyone add a device to the zero-touch console?
- Is it possible for an organisation to add previously-purchased devices to zero-touch?
- Can a MADA device be converted to EDLA?
- Can anyone remove a device from the zero-touch console?
- Does Samsung support zero-touch?
- Is it possible to set a zero-touch default configuration?
- Is it possible to bulk update zero-touch devices?
- Is it possible to change zero-touch resellers?
- Are all zero-touch devices Android Enterprise Recommended?
- What are DPC extras?
- What should I put in DPC extras?
- What happens if a device is uploaded to zero-touch with the wrong manufacturer?
- The device registered with zero-touch, but doesn’t launch during setup, why?
- Does Android Go support zero-touch?
- Are employee-owned devices eligible for zero-touch?
- What’s the recommended way of managing in-house (private) applications?
- Is it possible to deploy app shortcuts to the homescreen of an Android Enterprise device?
- The Google Play iFrame is missing a feature in my UEM. How do I enable it?
- How do I configure allowlist/blocklist domains for Google Chrome?
- How to configure Chrome managed bookmarks