Contents
Docs
General
- Introduction
- What is Android Enterprise?
- Android versions matrix
- Considerations when migrating from device administrator to Android Enterprise
- Android Enterprise feature requests
- What is Android Enterprise Recommended?
- Android Enterprise FAQ
- How to migrate Android devices from one EMM to another
- Android Enterprise device testing
- What is Private Space in Android 15, and how can organisations manage it?
- Why don't all Android devices come with GMS?
- What is Android One?
- Android Enterprise vs Device Admin: Why DA is no longer suitable
- Considerations for choosing Android in the Enterprise
- Feature spotlight: Android Smartlock
- Android glossary
- Android version evolution graphics
- Infobyte: Device Admin deprecation
- How to submit a device for Android Enterprise Recommended validation
- How to view software version information
- How to capture a bug report and device logs
- Gartner comparison of security controls for mobile devices 2019
Provisioning
- How to become a zero-touch enrolment reseller
- What is Android zero-touch enrolment?
- Android Enterprise zero-touch console administration guide
- Android Enterprise DPC identifier collection
- Android Enterprise provisioning guides
- Android Enterprise zero-touch DPC extras collection
- Infobyte: Android Enterprise deployment scenarios
- Infobyte: Android Enterprise fully managed provisioning methods
- Manual Android Enterprise work-managed QR code generation for MobileIron
Work profile
Fully managed
App management
- Set up Hypergate's Kerberos Authentication on MobileIron Core for Android Enterprise
- Managed Google Play, allowlist or blocklist?
- Considerations when deploying MTD with Android Enterprise
- Why you shouldn't install apps from unknown sources
- Create and manage private apps for Android Enterprise
- What is OEMConfig?
- Create and manage web apps for Android Enterprise
- How to locate a private Android app assigned to an organisation ID
- How to host enterprise apps outside of Google Play
- The Google Play iFrame app approval flow is deprecated
- Android 13 adds notifications access as a runtime permission
- Android 14 blocks apps targeting old Android versions
- Android 13 & up restricts permissions when apps are sideloaded
- Android system apps database
- How to resolve common Android app install failures, by error message
FAQ
- Is Android Enterprise supported on uncertified (non-GMS) devices?
- Can apps be sideloaded into the Private Space?
- Is Private Space supported on fully managed devices?
- Why don't Private Space apps go through VPN?
- Is it possible to manage personal applications on a work profile device?
- Does Samsung support Android Enterprise?
- How can apps be managed in the Private Space?
- Are Private Space apps visible to enterprise admins?
- Are Private Space applications truly hidden?
- Why has USB data access been disabled suddenly?
- What versions of Android support Android Enterprise?
- Is it possible to manage eSIM?
- How to check if an Android device is GMS/Play Protect certified?
- To use Android Enterprise do I need to buy Google Workspace (G Suite) and register my domain?
- What devices should I buy for my organisation?
- If Android Enterprise is supported from Lollipop, why is Marshmallow often mentioned instead?
- What’s the difference between Device Admin and Android Enterprise?
- What is the Android Enterprise bind?
- Can I change the account I used to bind Android Enterprise?
- Is it possible to bind Android Enterprise with multiple EMMs using one account?
- How do I remove the Android Enterprise bind from my current EMM?
- What is Android Enterprise Recommended?
- My AER device doesn’t work properly with Android Enterprise, what should I do?
- Is Android One better than AER? (Or the other way around?)
- How do I configure Google Workspace domains for provisioning?
- What’s the best provisioning method?
- What’s the difference between allow adding accounts vs allow configure credentials?
- Is it possible to utilise multiple VPN connections within a profile?
- Is it possible to utilise a single VPN connection across the entire device?
- Does Android support Kerberos natively?
- What’s the difference between device based accounts and user based accounts?
- How do I manage the new notifications runtime permission in Android 13?
- Can organisations see applications outside of the work profile?
- Can organisations deploy applications to the parent profile in a work profile deployment?
- Is it possible to migrate from DA to AE work profile without a re-enrol?
- What is a work challenge?
- Enrolment failed but the work profile was created. How do I remove it?
- Why can’t I install or uninstall apps on my managed device?
- How can I provision a fully managed device?
- Is it possible to “retire” (or enterprise wipe) a fully managed device?
- Devices factory reset as soon as they’re enrolled, why?
- Is Factory Reset Protection enabled on fully managed devices?
- Is it possible to migrate fully managed devices between EMM solutions?
- How has COPE changed in Android 11?
- Does Intune support COPE?
- Can organisations see applications outside of the work profile on a COPE device?
- Can organisations deploy applications to the parent profile in a COPE deployment?
- Is it possible to migrate from fully managed to work profiles on fully managed devices?
- How should system applications be handled on a COPE device?
- What OEMs currently support zero-touch?
- Where are zero-touch resellers located?
- Does zero-touch cost anything?
- Is an EMM still required with zero-touch?
- What happens if a fully set up device is added to the zero-touch console?
- What happens if a user starts setting up a device before the zero-touch config is applied?
- What happens if a zero-touch config is removed from an enrolled device?
- What happens if a new config for a different EMM or server is applied to an enrolled device?
- Can I add/remove users on a fully managed device?
- How can I access a Wi-Fi captive portal when devices are in Kiosk?
- My AMAPI project returns a usage limit error, why?
- What happens if a zero-touch assigned device is reset?
- What happens if a device is unregistered from the zero-touch console?
- Can a device be OTA managed from the zero-touch console?
- Does enrolling via zero-touch slow down or cause any delay to the setup process while it’s retrieving the zero-touch config?
- What deployment scenario will a zero-touch device enrol under?
- Why does zero-touch require so much touching?
- Can anyone add a device to the zero-touch console?
- Is it possible for an organisation to add previously-purchased devices to zero-touch?
- Can a MADA device be converted to EDLA?
- Can anyone remove a device from the zero-touch console?
- Does Samsung support zero-touch?
- Is it possible to set a zero-touch default configuration?
- Is it possible to bulk update zero-touch devices?
- Is it possible to change zero-touch resellers?
- Are all zero-touch devices Android Enterprise Recommended?
- What are DPC extras?
- What should I put in DPC extras?
- What happens if a device is uploaded to zero-touch with the wrong manufacturer?
- The device registered with zero-touch, but doesn’t launch during setup, why?
- Does Android Go support zero-touch?
- Are employee-owned devices eligible for zero-touch?
- What’s the recommended way of managing private (in-house) applications?
- How do I turn off Google Play app collections?
- Is it possible to deploy app shortcuts to the homescreen of an Android Enterprise device?
- Is it possible to backup & restore device data on a fully managed device?
- The Google Play iFrame is missing a feature in my UEM. How do I enable it?
- How do I configure allowlist/blocklist domains for Google Chrome?
- How to configure Chrome managed bookmarks
- Play Protect blocked my DPC, why?
Change log
Android Enterprise vs Device Admin: Why DA is no longer suitable
Contents
If you’ve read What is Android Enterprise and why is it used?, you’ll know Android Enterprise (AE) offers several rather useful features and deployment scenarios to suit many business requirements. If you haven’t read the above document, please do so either before or after this to compare.
A recurring query when discussing Android Enterprise is, as might be expected:
How is it different from legacy (device administrator) enrolment?
That question used to depend on whether we were referring to vanilla Android or Samsung & Knox; today with Samsung’s Android Enterprise unification and capabilities sitting comfortably atop the base layer of Android Enterprise APIs, it’s no longer necessary to decide between them, they can be leveraged together (though there will be references below).
What is Device Admin?
#Device Admin, introduced with Android 2.2 Froyo, offered something of a limited offering to fill the void for applications requiring elevated administrative permissions in order to perform certain tasks.
These permissions could be locally implemented within the app, or remotely pushed from an external server.
One such well-known example of an application leveraging Device Admin is the native email client, this is because this and many other email clients must accommodate basic security and control in order to enforce Exchange policies; an example requirement of an Exchange policy is the ability to wipe a lost or stolen device, and Device Admin APIs offered this capability.
Another API, long-since deprecated, included the ability for a DA application to change the passcode of the device. Something that would prove troublesome as Android grew in popularity.
The capabilities of DA grew as adoption increased, though the reason I refer to it as a limited offering in the opening paragraph is due to the fact it was never intended to be used in the way it has been, particularly for enterprise, and ramifications today can still be seen.
Challenges with Device Admin
#Below are a collection of challenges associated with device administrator, or legacy Android management generally. Organisations leveraging purely Samsung devices today may not necessarily have experienced some of these, but this is broadly speaking across the ecosystem as a whole. There’s a very good reason Samsung have dominated the enterprise space for so long – they’ve developed the tools and capabilities to mostly overcome the pitfalls of legacy management, though not entirely.
Difficult, error-prone enrolment
#Without provisioning methods, DA device enrolment has always been a long, fragmented, and inconsistent process requiring an end-user works through the whole setup wizard, manually downloads the EMM agent via Google Play or sideloads (the latter requiring enabling unknown sources, though this is often required anyway) and accepts various permissions.
There are a number of opportunities for error, such as skipping the adding of a Google account, denying permissions, downloading the wrong EMM agent and more; an example of this process on a Nexus 5 is documented here. It’s worth noting the Nexus 5 shipped without the typical array of additional OEM setup wizard screens and services which often add many more steps to the process.
With the exception of Samsung who have developed and leveraged Knox Mobile Enrolment (KME) for a number of years to ease DA EMM enrolment, for organisations who didn’t or couldn’t use it, Android enrolment has been consistently complex and error-prone.
Limited, inconsistent control
#Out of the box, Android as provided by many OEMs offers very few management APIs for EMMs to leverage, simply because they’ve never – before Android Enterprise – been included in the Android source code OEMs use to build their device images.
Some OEMs have over the years implemented their own APIs for various capabilities that make for a partially (or in Samsung’s case, very) manageable device, however this equally requires that EMMs choose to implement the respective bespoke APIs for the functionality offered, which hasn’t always been the case.
When EMMs do implement these bespoke APIs, in addition to having to request device administrator permissions for the EMM agent, it’s highly likely the EMM would also require an additional, per-OEM, application installed on the device to better utilise them; SOTI is most notable for having over 170 of OEM plugins, but the act of installing one involves enabling unknown sources and sideloading APKs. Not very secure.
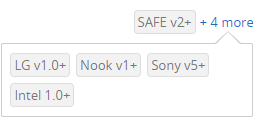 AirWatch restriction support by different OEMs
AirWatch restriction support by different OEMs
Beyond basic security policies and perhaps a simple email/Wi-Fi/etc configuration then, outside of the bigger OEMs (Samsung, Huawei, Sony, others to a lesser degree), there’s not a lot administrators can manipulate and control with a legacy-managed Android device, which already makes them rather unappealing for use in an enterprise setting.
The exception, as mentioned above, is Samsung. When a Samsung device is enrolled normally (as in, not via Knox Premium), EMM administrators have management over the device to a degree similar to that of an Android Enterprise fully managed device; there are an abundance of restrictions available and excellent visibility of device posture. Samsung’s DA offering isn’t perfect however, and encounters many of the other shortfalls of DA.
A poor app management experience
#When you then consider application management relies on the use of a Google account and requires users manually download applications from Google Play distributed to them via the EMM platform, it becomes even clearer to see the overhead for supporting these devices is rather high.
In some cases, again leveraging bespoke APIs of OEMs, it has been possible to push and install applications distributed in APK format from the EMM silently, but at a cost once more of security and management overhead.
For example, a single application hosted in Google Play may distribute upwards of 5 separate versions of an app depending on:
- OS version
- Architecture (32/64bit, ARM or Intel)
- Screen size or display density
If an IT admin were to simply extract from a device – or worse, download from the internet – a copy of the APK to be uploaded and distributed from the EMM, there’s little guarantee it is the correct version for the estate, particularly if that estate is varied, which they often are.
Worst case, the IT admin might inadvertently push a PHA (potentially harmful application) which could be anything from adware to a keylogger, screen recorder, or in another dire scenario, a derivative of double locker, which after gaining device admin privileges will change the passcode of the device and encrypt its contents.
Assuming the APK is safe, but not appropriate for the device, the organisation may end up incurring large mobile data fees as the EMM tries and fails to install an unsuitable APK repeatedly; the device will reject the installation, the EMM will see the failure and re-push the APK once more. Potentially at every checkin until admin intervention. I have seen this situation play out several times and it is not pleasant.
If taking the more sensible approach to application management by utilising Google Play, a Google account is required on the device and users of legacy-managed devices will simply be prompted, often repeatedly, to go and install it manually from Google Play as mentioned above. When retiring the device (as in, enterprise wipe – not a full reset) there’s no consistent guarantee those download applications and their accounts will be removed with it, potentially leaving corporate data on an unmanaged device.
Further complicating things, the introduction of Factory Reset Protection (FRP) means wiping a device without first removing the users’ Google account may render the device unusable. Really not an ideal situation to end up in as without end-user cooperation, it can be costly to send devices off for repair, a necessity if the device is to be re-deployed.
This is not to say these devices have no place in an enterprise setting. Organisations that support a Bring Your Own Device (BYOD) initiative will find most EMMs have containerisation solutions permitting the use of corporate applications within an encrypted, sandboxed environment. In the case of Samsung these solutions are again built in! Assuming the organisation doesn’t want to control the devices, rather only the corporate data on those devices, it’s possible to support legacy Android, at least until Android Q when DA is deprecated.
Permissions – management and abuse
#Permissions management: Depending on the permissions required for applications, be that the DPC (EMM agent) or those brought down from the Play Store, applications can either function well, on a limited basis or simply not at all when those required permissions are not granted.
App permissions have gotten increasingly more granular, easier to understand and offer far greater control since Android 6.0, but with that comes the potential, from the perspective of an organisation, for increased overhead and potential issues.
With device admin, app permissions cannot be managed by anyone but the end-user, meaning where problems arise in the function of managed applications, it is highly likely due to the accidental or intentional denial of a critical permission.
A user may not wish to grant a managed application access to contacts or calendar, or perhaps a request for location gives the impression an application may be tracking the end-user location.
Whatever the reasoning behind it, the only means for overcoming mismanagement of permissions requires users manually approving them via application settings, something which will often require IT assistance. When it’s a few devices this can be problematic, when it affects a reasonable proportion of a large fleet, the time and associated costs may rise considerably.
Permissions abuse: with the Device Admin model, there’s no single “owner” of a device. As many device admin-enabled apps as desired may control a device, all with as many or as few implemented DA permissions as app developers desire.
With this model, it’s all too easy for permissions abuse to flourish.
Take Double Locker mentioned above, this app disguised itself as Flash Player. This is not an uncommon method of distributing PHAs and for many users, the DA permissions request is no different to any other app asking for any other permission.
Users are conditioned to agree to such requests with little consideration, and thus, PHA developers can easily take advantage.
There is justification for such a model however, with no alternatives at the time, and multiple legitimate applications making use of various capabilities for password management, locking the device or otherwise by EMM solutions, MTD/AV applications, even Google’s own Find My Device utilises it to this day.
Device Admin is going away
#Even if DA was considered passable today, there is no future for legacy device management. With the introduction of Android Q, EMMs targeting API level 29 will no longer be able to adequately manage DA-enrolled devices.
For more information on DA deprecation, check out the following resources:
- Infobyte – Did you know? Device Admin deprecation
- Google is deprecating device admin in favour of Android Enterprise
How Android Enterprise compares
#- Consistent, reliable management
- Flexible, simple & safe application management
- Zero-day support for new features and functionality
- Secure by default
- A solid foundation on which to build
All of these aspects of Android Enterprise are explained in detail in the following documents:
- What is Android Enterprise?
- Considerations when migrating from device administrator to Android Enterprise
- Considerations for choosing Android in the enterprise
Conclusion
#Most organisations, and particularly those who want to more easily support a diverse range of devices will benefit massively from the consistent experience, the automated management of Google accounts and the remote application configuration of Android Enterprise; more from the security, privacy and modern approach to management.
In any case, what should be abundantly clear is how ill-equipped Device Admin is for corporate management, and with it’s impending demise, organisations can’t risk putting off a migration.
Docs
General
- Introduction
- What is Android Enterprise?
- Android versions matrix
- Considerations when migrating from device administrator to Android Enterprise
- Android Enterprise feature requests
- What is Android Enterprise Recommended?
- Android Enterprise FAQ
- How to migrate Android devices from one EMM to another
- Android Enterprise device testing
- What is Private Space in Android 15, and how can organisations manage it?
- Why don't all Android devices come with GMS?
- What is Android One?
- Android Enterprise vs Device Admin: Why DA is no longer suitable
- Considerations for choosing Android in the Enterprise
- Feature spotlight: Android Smartlock
- Android glossary
- Android version evolution graphics
- Infobyte: Device Admin deprecation
- How to submit a device for Android Enterprise Recommended validation
- How to view software version information
- How to capture a bug report and device logs
- Gartner comparison of security controls for mobile devices 2019
Provisioning
- How to become a zero-touch enrolment reseller
- What is Android zero-touch enrolment?
- Android Enterprise zero-touch console administration guide
- Android Enterprise DPC identifier collection
- Android Enterprise provisioning guides
- Android Enterprise zero-touch DPC extras collection
- Infobyte: Android Enterprise deployment scenarios
- Infobyte: Android Enterprise fully managed provisioning methods
- Manual Android Enterprise work-managed QR code generation for MobileIron
Work profile
Fully managed
App management
- Set up Hypergate's Kerberos Authentication on MobileIron Core for Android Enterprise
- Managed Google Play, allowlist or blocklist?
- Considerations when deploying MTD with Android Enterprise
- Why you shouldn't install apps from unknown sources
- Create and manage private apps for Android Enterprise
- What is OEMConfig?
- Create and manage web apps for Android Enterprise
- How to locate a private Android app assigned to an organisation ID
- How to host enterprise apps outside of Google Play
- The Google Play iFrame app approval flow is deprecated
- Android 13 adds notifications access as a runtime permission
- Android 14 blocks apps targeting old Android versions
- Android 13 & up restricts permissions when apps are sideloaded
- Android system apps database
- How to resolve common Android app install failures, by error message
FAQ
- Is Android Enterprise supported on uncertified (non-GMS) devices?
- Can apps be sideloaded into the Private Space?
- Is Private Space supported on fully managed devices?
- Why don't Private Space apps go through VPN?
- Is it possible to manage personal applications on a work profile device?
- Does Samsung support Android Enterprise?
- How can apps be managed in the Private Space?
- Are Private Space apps visible to enterprise admins?
- Are Private Space applications truly hidden?
- Why has USB data access been disabled suddenly?
- What versions of Android support Android Enterprise?
- Is it possible to manage eSIM?
- How to check if an Android device is GMS/Play Protect certified?
- To use Android Enterprise do I need to buy Google Workspace (G Suite) and register my domain?
- What devices should I buy for my organisation?
- If Android Enterprise is supported from Lollipop, why is Marshmallow often mentioned instead?
- What’s the difference between Device Admin and Android Enterprise?
- What is the Android Enterprise bind?
- Can I change the account I used to bind Android Enterprise?
- Is it possible to bind Android Enterprise with multiple EMMs using one account?
- How do I remove the Android Enterprise bind from my current EMM?
- What is Android Enterprise Recommended?
- My AER device doesn’t work properly with Android Enterprise, what should I do?
- Is Android One better than AER? (Or the other way around?)
- How do I configure Google Workspace domains for provisioning?
- What’s the best provisioning method?
- What’s the difference between allow adding accounts vs allow configure credentials?
- Is it possible to utilise multiple VPN connections within a profile?
- Is it possible to utilise a single VPN connection across the entire device?
- Does Android support Kerberos natively?
- What’s the difference between device based accounts and user based accounts?
- How do I manage the new notifications runtime permission in Android 13?
- Can organisations see applications outside of the work profile?
- Can organisations deploy applications to the parent profile in a work profile deployment?
- Is it possible to migrate from DA to AE work profile without a re-enrol?
- What is a work challenge?
- Enrolment failed but the work profile was created. How do I remove it?
- Why can’t I install or uninstall apps on my managed device?
- How can I provision a fully managed device?
- Is it possible to “retire” (or enterprise wipe) a fully managed device?
- Devices factory reset as soon as they’re enrolled, why?
- Is Factory Reset Protection enabled on fully managed devices?
- Is it possible to migrate fully managed devices between EMM solutions?
- How has COPE changed in Android 11?
- Does Intune support COPE?
- Can organisations see applications outside of the work profile on a COPE device?
- Can organisations deploy applications to the parent profile in a COPE deployment?
- Is it possible to migrate from fully managed to work profiles on fully managed devices?
- How should system applications be handled on a COPE device?
- What OEMs currently support zero-touch?
- Where are zero-touch resellers located?
- Does zero-touch cost anything?
- Is an EMM still required with zero-touch?
- What happens if a fully set up device is added to the zero-touch console?
- What happens if a user starts setting up a device before the zero-touch config is applied?
- What happens if a zero-touch config is removed from an enrolled device?
- What happens if a new config for a different EMM or server is applied to an enrolled device?
- Can I add/remove users on a fully managed device?
- How can I access a Wi-Fi captive portal when devices are in Kiosk?
- My AMAPI project returns a usage limit error, why?
- What happens if a zero-touch assigned device is reset?
- What happens if a device is unregistered from the zero-touch console?
- Can a device be OTA managed from the zero-touch console?
- Does enrolling via zero-touch slow down or cause any delay to the setup process while it’s retrieving the zero-touch config?
- What deployment scenario will a zero-touch device enrol under?
- Why does zero-touch require so much touching?
- Can anyone add a device to the zero-touch console?
- Is it possible for an organisation to add previously-purchased devices to zero-touch?
- Can a MADA device be converted to EDLA?
- Can anyone remove a device from the zero-touch console?
- Does Samsung support zero-touch?
- Is it possible to set a zero-touch default configuration?
- Is it possible to bulk update zero-touch devices?
- Is it possible to change zero-touch resellers?
- Are all zero-touch devices Android Enterprise Recommended?
- What are DPC extras?
- What should I put in DPC extras?
- What happens if a device is uploaded to zero-touch with the wrong manufacturer?
- The device registered with zero-touch, but doesn’t launch during setup, why?
- Does Android Go support zero-touch?
- Are employee-owned devices eligible for zero-touch?
- What’s the recommended way of managing private (in-house) applications?
- How do I turn off Google Play app collections?
- Is it possible to deploy app shortcuts to the homescreen of an Android Enterprise device?
- Is it possible to backup & restore device data on a fully managed device?
- The Google Play iFrame is missing a feature in my UEM. How do I enable it?
- How do I configure allowlist/blocklist domains for Google Chrome?
- How to configure Chrome managed bookmarks
- Play Protect blocked my DPC, why?