Contents
Docs
General
- Introduction
- What is Android Enterprise?
- Android versions matrix
- Considerations when migrating from device administrator to Android Enterprise
- Android Enterprise feature requests
- What is Android Enterprise Recommended?
- Android Enterprise FAQ
- Android Enterprise device testing
- What is Private Space in Android 15, and how can organisations manage it?
- Why don't all Android devices come with GMS?
- What is Android One?
- Android Enterprise vs Device Admin: Why DA is no longer suitable
- Considerations for choosing Android in the Enterprise
- Feature spotlight: Android Smartlock
- Android glossary
- Android version evolution graphics
- Infobyte: Device Admin deprecation
- How to submit a device for Android Enterprise Recommended validation
- How to view software version information
- How to capture a bug report and device logs
- Gartner comparison of security controls for mobile devices 2019
Provisioning
- How to become a zero-touch enrolment reseller
- What is Android zero-touch enrolment?
- Android Enterprise zero-touch console administration guide
- Android Enterprise DPC identifier collection
- Android Enterprise provisioning guides
- Android Enterprise zero-touch DPC extras collection
- Infobyte: Android Enterprise deployment scenarios
- Infobyte: Android Enterprise fully managed provisioning methods
- Manual Android Enterprise work-managed QR code generation for MobileIron
Work profile
Fully managed
App management
- Set up Hypergate's Kerberos Authentication on MobileIron Core for Android Enterprise
- Managed Google Play, allowlist or blocklist?
- Considerations when deploying MTD with Android Enterprise
- Why you shouldn't install apps from unknown sources
- Create and manage private apps for Android Enterprise
- What is OEMConfig?
- Create and manage web apps for Android Enterprise
- How to locate a private Android app assigned to an organisation ID
- How to host enterprise apps outside of Google Play
- The Google Play iFrame app approval flow is deprecated
- Android 13 adds notifications access as a runtime permission
- Android 14 blocks apps targeting old Android versions
- Android 13 & up restricts permissions when apps are sideloaded
- Android system apps database
- How to resolve common Android app install failures, by error message
FAQ
- Is Android Enterprise supported on uncertified (non-GMS) devices?
- Can apps be sideloaded into the Private Space?
- Is Private Space supported on fully managed devices?
- Why don't Private Space apps go through VPN?
- Is it possible to manage personal applications on a work profile device?
- Does Samsung support Android Enterprise?
- How can apps be managed in the Private Space?
- Are Private Space apps visible to enterprise admins?
- Are Private Space applications truly hidden?
- Why has USB data access been disabled suddenly?
- What versions of Android support Android Enterprise?
- Is it possible to manage eSIM?
- How to check if an Android device is GMS/Play Protect certified?
- To use Android Enterprise do I need to buy Google Workspace (G Suite) and register my domain?
- What devices should I buy for my organisation?
- If Android Enterprise is supported from Lollipop, why is Marshmallow often mentioned instead?
- What’s the difference between Device Admin and Android Enterprise?
- What is the Android Enterprise bind?
- Can I change the account I used to bind Android Enterprise?
- Is it possible to bind Android Enterprise with multiple EMMs using one account?
- How do I remove the Android Enterprise bind from my current EMM?
- What is Android Enterprise Recommended?
- My AER device doesn’t work properly with Android Enterprise, what should I do?
- Is Android One better than AER? (Or the other way around?)
- How do I configure Google Workspace domains for provisioning?
- What’s the best provisioning method?
- What’s the difference between allow adding accounts vs allow configure credentials?
- Is it possible to utilise multiple VPN connections within a profile?
- Is it possible to utilise a single VPN connection across the entire device?
- Does Android support Kerberos natively?
- What’s the difference between device based accounts and user based accounts?
- How do I manage the new notifications runtime permission in Android 13?
- Can organisations see applications outside of the work profile?
- Can organisations deploy applications to the parent profile in a work profile deployment?
- Is it possible to migrate from DA to AE work profile without a re-enrol?
- What is a work challenge?
- Enrolment failed but the work profile was created. How do I remove it?
- Why can’t I install or uninstall apps on my managed device?
- How can I provision a fully managed device?
- Is it possible to “retire” (or enterprise wipe) a fully managed device?
- Devices factory reset as soon as they’re enrolled, why?
- Is Factory Reset Protection enabled on fully managed devices?
- Is it possible to migrate fully managed devices between EMM solutions?
- How has COPE changed in Android 11?
- Does Intune support COPE?
- Can organisations see applications outside of the work profile on a COPE device?
- Can organisations deploy applications to the parent profile in a COPE deployment?
- Is it possible to migrate from fully managed to work profiles on fully managed devices?
- How should system applications be handled on a COPE device?
- What OEMs currently support zero-touch?
- Where are zero-touch resellers located?
- Does zero-touch cost anything?
- Is an EMM still required with zero-touch?
- What happens if a fully set up device is added to the zero-touch console?
- What happens if a user starts setting up a device before the zero-touch config is applied?
- What happens if a zero-touch config is removed from an enrolled device?
- What happens if a new config for a different EMM or server is applied to an enrolled device?
- Can I add/remove users on a fully managed device?
- How can I access a Wi-Fi captive portal when devices are in Kiosk?
- My AMAPI project returns a usage limit error, why?
- What happens if a zero-touch assigned device is reset?
- What happens if a device is unregistered from the zero-touch console?
- Can a device be OTA managed from the zero-touch console?
- Does enrolling via zero-touch slow down or cause any delay to the setup process while it’s retrieving the zero-touch config?
- What deployment scenario will a zero-touch device enrol under?
- Why does zero-touch require so much touching?
- Can anyone add a device to the zero-touch console?
- Is it possible for an organisation to add previously-purchased devices to zero-touch?
- Can a MADA device be converted to EDLA?
- Can anyone remove a device from the zero-touch console?
- Does Samsung support zero-touch?
- Is it possible to set a zero-touch default configuration?
- Is it possible to bulk update zero-touch devices?
- Is it possible to change zero-touch resellers?
- Are all zero-touch devices Android Enterprise Recommended?
- What are DPC extras?
- What should I put in DPC extras?
- What happens if a device is uploaded to zero-touch with the wrong manufacturer?
- The device registered with zero-touch, but doesn’t launch during setup, why?
- Does Android Go support zero-touch?
- Are employee-owned devices eligible for zero-touch?
- What’s the recommended way of managing private (in-house) applications?
- How do I turn off Google Play app collections?
- Is it possible to deploy app shortcuts to the homescreen of an Android Enterprise device?
- Is it possible to backup & restore device data on a fully managed device?
- The Google Play iFrame is missing a feature in my UEM. How do I enable it?
- How do I configure allowlist/blocklist domains for Google Chrome?
- How to configure Chrome managed bookmarks
- Play Protect blocked my DPC, why?
Feature spotlight: Block unknown sources on work profile deployments
Contents
In November 2018, Google released a new feature enabling the ability to disable unknown sources device-wide on work profile deployments as far back as Android 6.0.
Google docs state 8.0 as this is the earliest version of Android which supports preventing verify apps from being disabled (the feature this relies on), however it will function as far back 6.0 as long as verify apps is enabled with the caveat it may be overridden by the end-user.
In Android 10 this feature became a natively supported AE API, rather than one managed through Google Play Services.
Context
#App installation via unknown sources remains a primary source of potentially harmful applications (PHA), with users being considerably more likely to install a PHA when downloading APKs from the internet, email or other means compared to those who only install applications from the Play Store.
For all fully managed deployment scenarios (COBO, COPE, COSU) this isn’t a concern; in most cases EMMs disable unknown sources by default or at least offer the opportunity to do so via configs and policies.
Work profile deployments however have been the exception; with intentionally limited management of a work profile device on a device level, and a greater focus on user privacy, many controls – including the blocking of unknown sources outside of the work profile – have not been available for organisations.
This is a good thing, and a differentiating feature with Android.
BYOD deployments are just that, bring your own as opposed to using a corporate device. Which means users will have their own apps, data, and control over their personally owned devices, extending also to what and how they install applications.
Why this matters
#Unfortunately, while many PHAs aren’t massively harmful, many more do have the ability to be quite disruptive. They can target the SIM, network, device, leverage vulnerabilities, abuse permissions and more.
Even with corporate data securely isolated and separately encrypted from the parent profile, there are other means of causing harm to the organisation without gaining direct access to data on disk; while the EMM can often detect device-based attacks (compromised status), without an MTD on the device, other attacks may go unnoticed.
Without a way of preventing PHAs from being sideloaded, there is a level of risk which entirely relies on the end-user as the last line of defence.
The solution
#With the introduction of this new feature, installation from unknown sources on work profile devices can be prevented. Unusually, this has been introduced in a GMS update and therefore is supported as far back as Android 6.0.
Like enforcing a passcode on a device, organisations now have the capability to ensure any users opting to bring their personal devices into the business will not be installing applications outside of the Google Play Store, offering additional security and peace of mind.
Preventing installation via unknown sources requires EMM integration, so may not be available for use on all platforms (and some may opt not to implement it at all).
Block unknown sources in MobileIron Core
#To enable this within MobileIron Core, simply ensure the the box for Allow unknown sources in device in Lockdown Policy is unchecked:
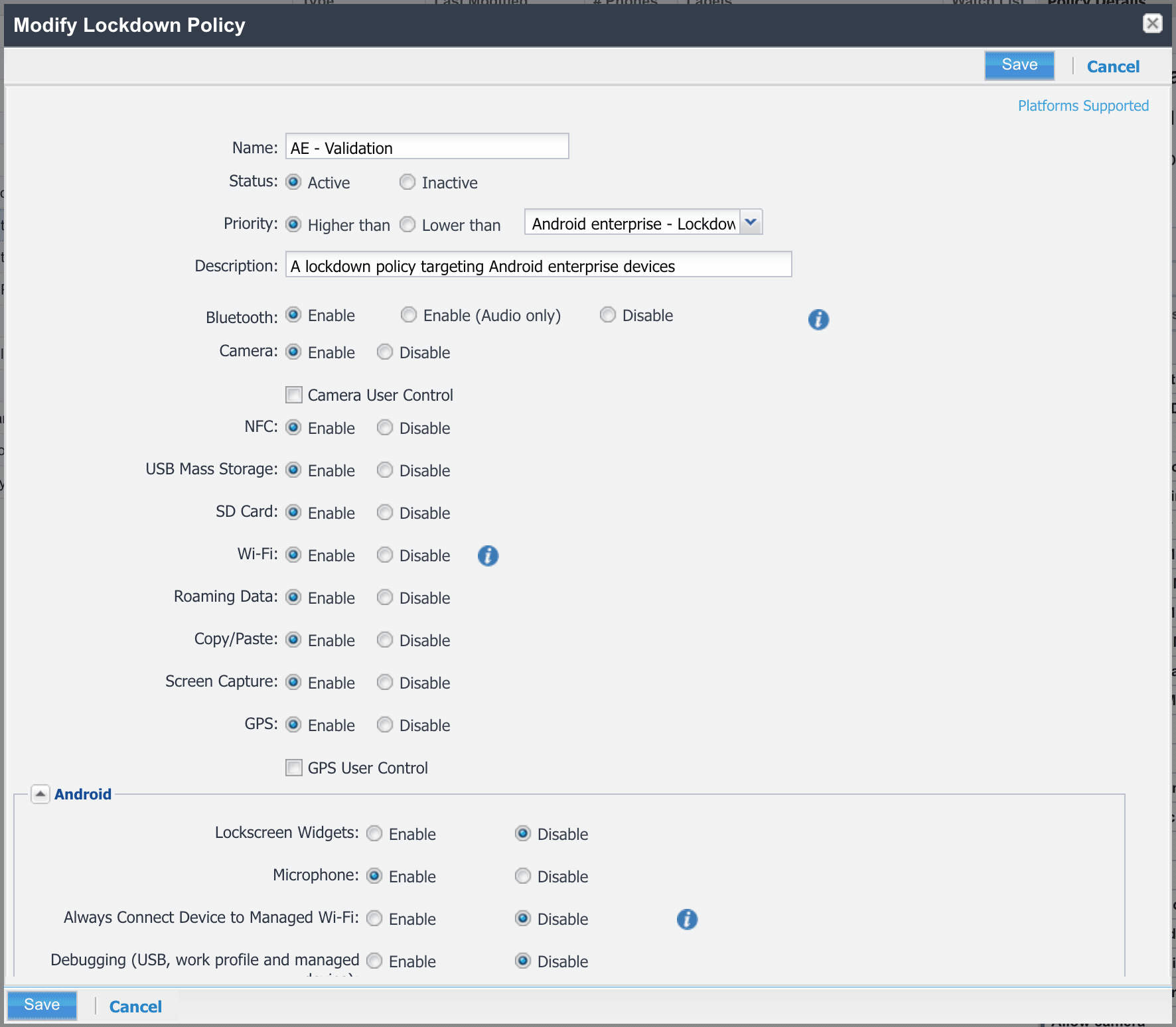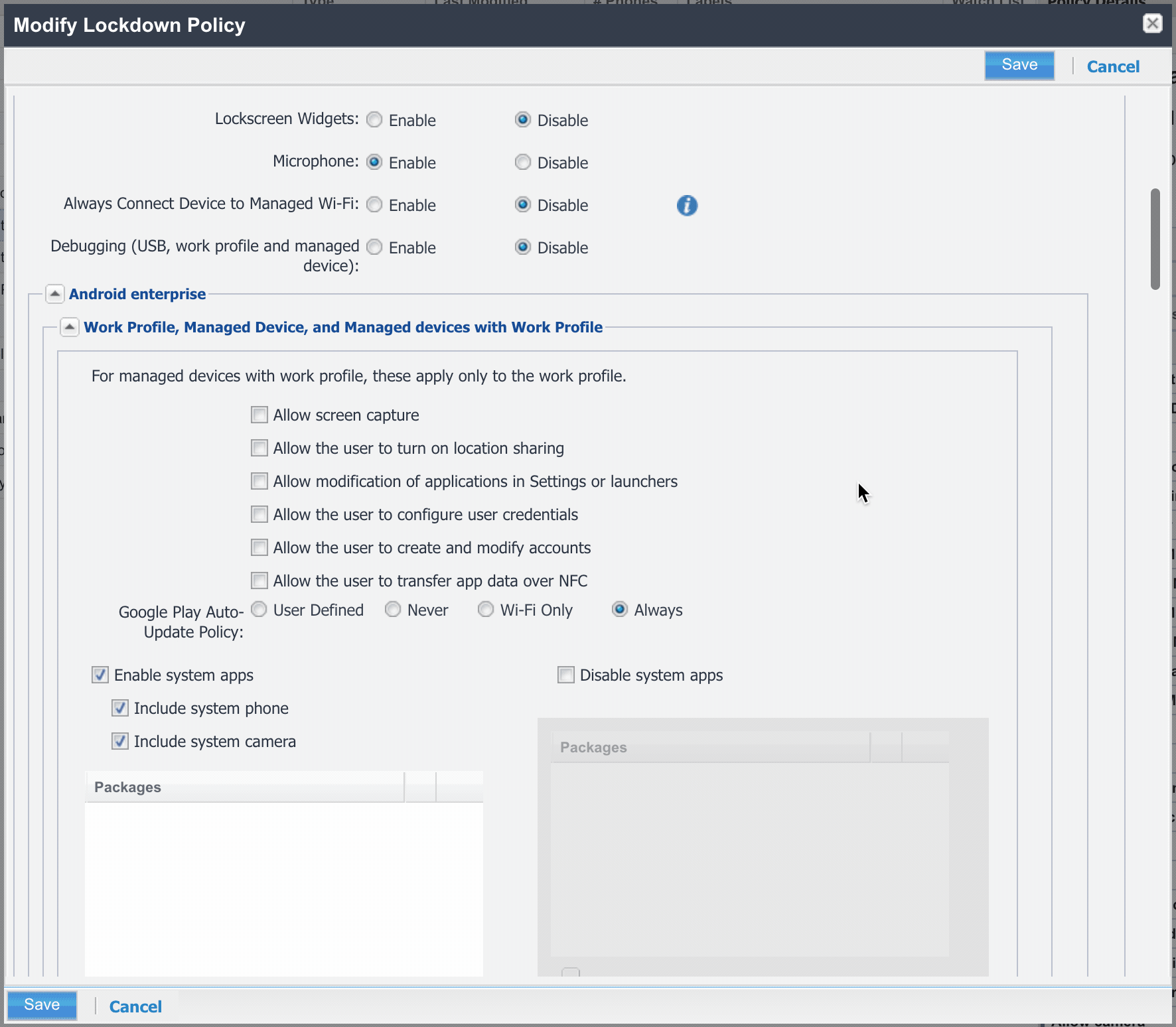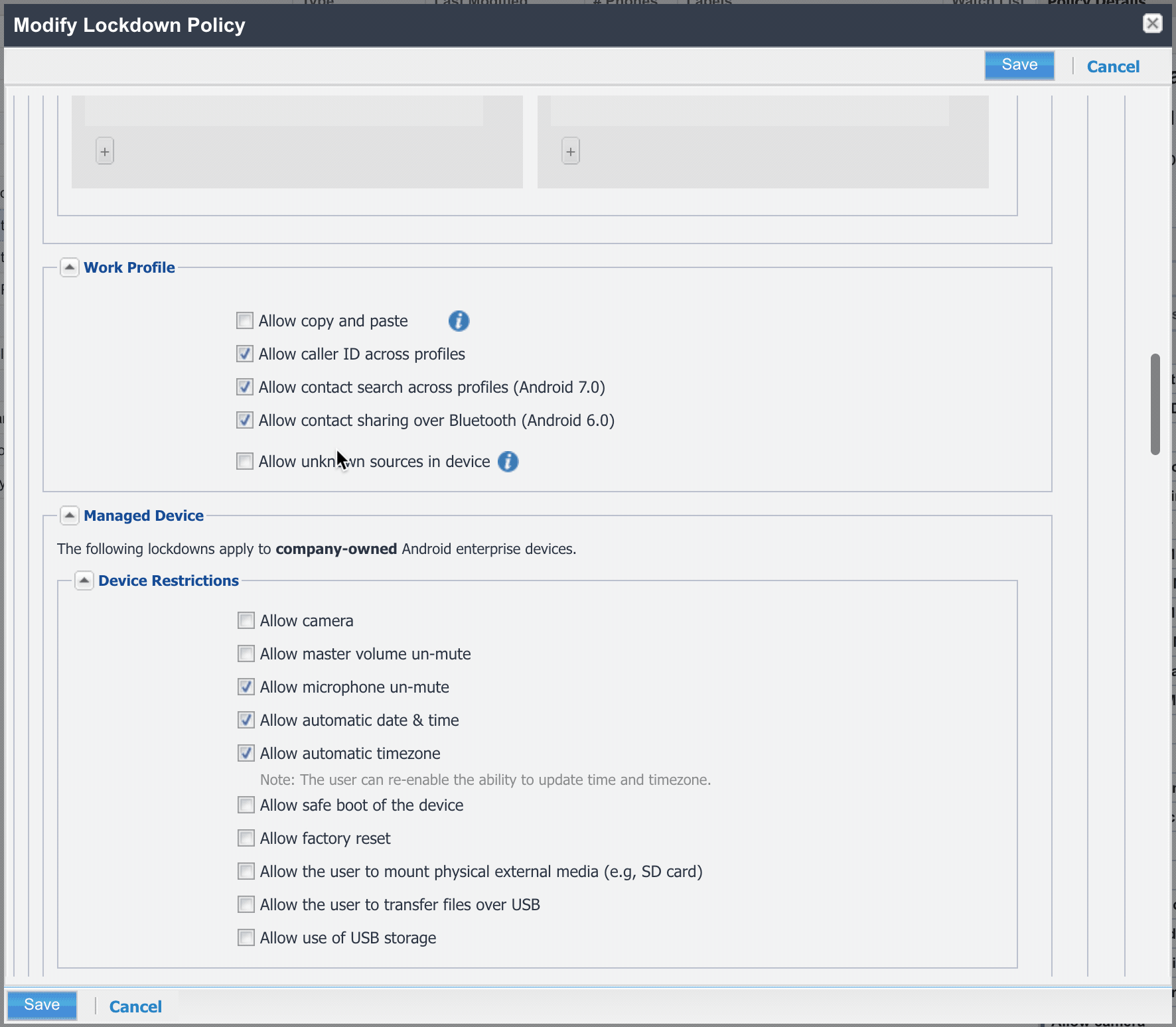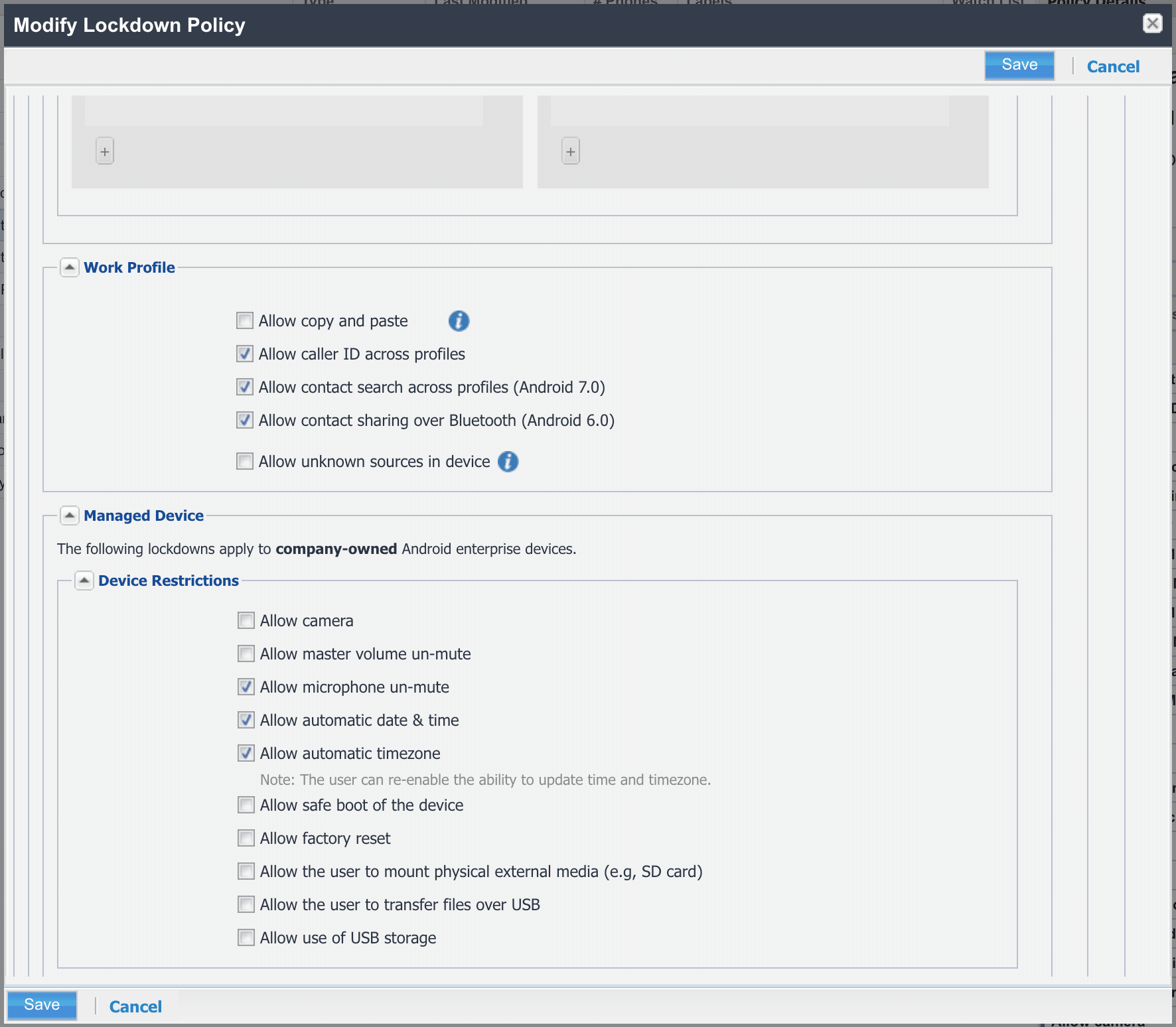
Block unknown sources in Workspace One UEM
#WS1 UEM requires a custom XML payload for support below Android 10. Use the following XML sample:
<characteristic type="com.airwatch.android.androidwork.app:com.android.vending" uuid="b4yt0nb43-3df7-4845-aeea-795020609ead">
<parm name="verify_apps:device_wide_unknown_source_block" value="true" type="boolean" />
</characteristic>
Then create a new profile, opting for the Custom Settings payload:
For Android 10 and future versions it’s possible to configure this in the restrictions payload.
Contact your EMM for additional information and support.
Docs
General
- Introduction
- What is Android Enterprise?
- Android versions matrix
- Considerations when migrating from device administrator to Android Enterprise
- Android Enterprise feature requests
- What is Android Enterprise Recommended?
- Android Enterprise FAQ
- Android Enterprise device testing
- What is Private Space in Android 15, and how can organisations manage it?
- Why don't all Android devices come with GMS?
- What is Android One?
- Android Enterprise vs Device Admin: Why DA is no longer suitable
- Considerations for choosing Android in the Enterprise
- Feature spotlight: Android Smartlock
- Android glossary
- Android version evolution graphics
- Infobyte: Device Admin deprecation
- How to submit a device for Android Enterprise Recommended validation
- How to view software version information
- How to capture a bug report and device logs
- Gartner comparison of security controls for mobile devices 2019
Provisioning
- How to become a zero-touch enrolment reseller
- What is Android zero-touch enrolment?
- Android Enterprise zero-touch console administration guide
- Android Enterprise DPC identifier collection
- Android Enterprise provisioning guides
- Android Enterprise zero-touch DPC extras collection
- Infobyte: Android Enterprise deployment scenarios
- Infobyte: Android Enterprise fully managed provisioning methods
- Manual Android Enterprise work-managed QR code generation for MobileIron
Work profile
Fully managed
App management
- Set up Hypergate's Kerberos Authentication on MobileIron Core for Android Enterprise
- Managed Google Play, allowlist or blocklist?
- Considerations when deploying MTD with Android Enterprise
- Why you shouldn't install apps from unknown sources
- Create and manage private apps for Android Enterprise
- What is OEMConfig?
- Create and manage web apps for Android Enterprise
- How to locate a private Android app assigned to an organisation ID
- How to host enterprise apps outside of Google Play
- The Google Play iFrame app approval flow is deprecated
- Android 13 adds notifications access as a runtime permission
- Android 14 blocks apps targeting old Android versions
- Android 13 & up restricts permissions when apps are sideloaded
- Android system apps database
- How to resolve common Android app install failures, by error message
FAQ
- Is Android Enterprise supported on uncertified (non-GMS) devices?
- Can apps be sideloaded into the Private Space?
- Is Private Space supported on fully managed devices?
- Why don't Private Space apps go through VPN?
- Is it possible to manage personal applications on a work profile device?
- Does Samsung support Android Enterprise?
- How can apps be managed in the Private Space?
- Are Private Space apps visible to enterprise admins?
- Are Private Space applications truly hidden?
- Why has USB data access been disabled suddenly?
- What versions of Android support Android Enterprise?
- Is it possible to manage eSIM?
- How to check if an Android device is GMS/Play Protect certified?
- To use Android Enterprise do I need to buy Google Workspace (G Suite) and register my domain?
- What devices should I buy for my organisation?
- If Android Enterprise is supported from Lollipop, why is Marshmallow often mentioned instead?
- What’s the difference between Device Admin and Android Enterprise?
- What is the Android Enterprise bind?
- Can I change the account I used to bind Android Enterprise?
- Is it possible to bind Android Enterprise with multiple EMMs using one account?
- How do I remove the Android Enterprise bind from my current EMM?
- What is Android Enterprise Recommended?
- My AER device doesn’t work properly with Android Enterprise, what should I do?
- Is Android One better than AER? (Or the other way around?)
- How do I configure Google Workspace domains for provisioning?
- What’s the best provisioning method?
- What’s the difference between allow adding accounts vs allow configure credentials?
- Is it possible to utilise multiple VPN connections within a profile?
- Is it possible to utilise a single VPN connection across the entire device?
- Does Android support Kerberos natively?
- What’s the difference between device based accounts and user based accounts?
- How do I manage the new notifications runtime permission in Android 13?
- Can organisations see applications outside of the work profile?
- Can organisations deploy applications to the parent profile in a work profile deployment?
- Is it possible to migrate from DA to AE work profile without a re-enrol?
- What is a work challenge?
- Enrolment failed but the work profile was created. How do I remove it?
- Why can’t I install or uninstall apps on my managed device?
- How can I provision a fully managed device?
- Is it possible to “retire” (or enterprise wipe) a fully managed device?
- Devices factory reset as soon as they’re enrolled, why?
- Is Factory Reset Protection enabled on fully managed devices?
- Is it possible to migrate fully managed devices between EMM solutions?
- How has COPE changed in Android 11?
- Does Intune support COPE?
- Can organisations see applications outside of the work profile on a COPE device?
- Can organisations deploy applications to the parent profile in a COPE deployment?
- Is it possible to migrate from fully managed to work profiles on fully managed devices?
- How should system applications be handled on a COPE device?
- What OEMs currently support zero-touch?
- Where are zero-touch resellers located?
- Does zero-touch cost anything?
- Is an EMM still required with zero-touch?
- What happens if a fully set up device is added to the zero-touch console?
- What happens if a user starts setting up a device before the zero-touch config is applied?
- What happens if a zero-touch config is removed from an enrolled device?
- What happens if a new config for a different EMM or server is applied to an enrolled device?
- Can I add/remove users on a fully managed device?
- How can I access a Wi-Fi captive portal when devices are in Kiosk?
- My AMAPI project returns a usage limit error, why?
- What happens if a zero-touch assigned device is reset?
- What happens if a device is unregistered from the zero-touch console?
- Can a device be OTA managed from the zero-touch console?
- Does enrolling via zero-touch slow down or cause any delay to the setup process while it’s retrieving the zero-touch config?
- What deployment scenario will a zero-touch device enrol under?
- Why does zero-touch require so much touching?
- Can anyone add a device to the zero-touch console?
- Is it possible for an organisation to add previously-purchased devices to zero-touch?
- Can a MADA device be converted to EDLA?
- Can anyone remove a device from the zero-touch console?
- Does Samsung support zero-touch?
- Is it possible to set a zero-touch default configuration?
- Is it possible to bulk update zero-touch devices?
- Is it possible to change zero-touch resellers?
- Are all zero-touch devices Android Enterprise Recommended?
- What are DPC extras?
- What should I put in DPC extras?
- What happens if a device is uploaded to zero-touch with the wrong manufacturer?
- The device registered with zero-touch, but doesn’t launch during setup, why?
- Does Android Go support zero-touch?
- Are employee-owned devices eligible for zero-touch?
- What’s the recommended way of managing private (in-house) applications?
- How do I turn off Google Play app collections?
- Is it possible to deploy app shortcuts to the homescreen of an Android Enterprise device?
- Is it possible to backup & restore device data on a fully managed device?
- The Google Play iFrame is missing a feature in my UEM. How do I enable it?
- How do I configure allowlist/blocklist domains for Google Chrome?
- How to configure Chrome managed bookmarks
- Play Protect blocked my DPC, why?