Contents
Articles
2025
- The Android Management API doesn't support pulling managed properties (config) from app tracks. Here's how to work around it
- Hands-on with CVE-2025-22442, a work profile sideloading vulnerability affecting most Android devices today
- AAB support for private apps in the managed Google Play iFrame is coming, take a first look here
- What's new (so far) for enterprise in Android 16
2024
- Android 15: What's new for enterprise?
- How Goto's acquisition of Miradore is eroding a once-promising MDM solution
- Google Play Protect no longer sends sideloaded applications for scanning on enterprise-managed devices
- Mobile Pros is moving to Discord
- Avoid another CrowdStrike takedown: Two approaches to replacing Windows
- Introducing MANAGED SETTINGS
- I'm joining NinjaOne
- Samsung announces Knox SDK restrictions for Android 15
- What's new (so far) for enterprise in Android 15
- Google quietly introduces new quotas for unvalidated AMAPI use
- What is Play Auto Install (PAI) in Android and how does it work?
- AMAPI publicly adds support for DPC migration
- How do Android devices become certified?
2023
- Mute @channel & @here notifications in Slack
- A guide to raising better support requests
- Ask Jason: How should we manage security and/or OS updates for our devices?
- Pixel 8 series launches with 7 years of software support
- Android's work profile behaviour has been reverted in 14 beta 5.3
- Fairphone raises the bar with commitment to Android updates
- Product files: The DoorDash T8
- Android's work profile gets a major upgrade in 14
- Google's inactive account policy may not impact Android Enterprise customers
- Product files: Alternative form factors and power solutions
- What's new in Android 14 for enterprise
- Introducing Micro Mobility
- Android Enterprise: A refresher
2022
- What I'd like to see from Android Enterprise in 2023
- Thoughts on Android 12's password complexity changes
- Google Play target API requirements & impact on enterprise applications
- Sunsetting Discuss comment platform
- Google publishes differences between Android and Android Go
- Android Go & EMM support
- Relaunching bayton.org
- AER dropped the 3/5 year update mandate with Android 11, where are we now?
- I made a bet with Google (and lost)
2020
- Product files: Building Android devices
- Google announce big changes to zero-touch
- VMware announces end of support for Device Admin
- Google launch the Android Enterprise Help Community
- Watch: An Android Enterprise discussion with Hypergate
- Listen again: BM podcast #144 - Jason Bayton & Russ Mohr talk Android!
- Google's Android Management API will soon support COPE
- Android Enterprise in 11: Google reduces visibility and control with COPE to bolster privacy.
- The decade that redefined Android in the enterprise
2019
- Why Intune doesn't support Android Enterprise COPE
- VMware WS1 UEM 1908 supports Android Enterprise enrolments on closed networks and AOSP devices
- The Bayton 2019 Android Enterprise experience survey
- Android Enterprise Partner Summit 2019 highlights
- The Huawei ban and Enterprise: what now?
- Dabbling with Android Enterprise in Q beta 3
- Why I moved from Google WiFi to Netgear Orbi
- I'm joining Social Mobile as Director of Android Innovation
- Android Enterprise in Q/10: features and clarity on DA deprecation
- MWC 2019: Mid-range devices excel, 5G everything, form-factors galore and Android Enterprise
- UEM tools managing Android-powered cars
- Joining the Android Enterprise Experts community
- February was an interesting month for OEMConfig
- Google launch Android Enterprise Recommended for Managed Service Providers
- Migrating from Windows 10 Mobile? Here's why you should consider Android
- AER expands: Android Enterprise Recommended for EMMs
- What I'd like to see from Android Enterprise in 2019
2018
- My top Android apps in 2018
- Year in review: 2018
- MobileIron Cloud R58 supports Android Enterprise fully managed devices with work profiles
- Hands on with the Huawei Mate 20 Pro
- Workspace ONE UEM 1810 introduces support for Android Enterprise fully managed devices with work profiles
- G Suite no longer prevents Android data leakage by default
- Live: Huawei Mate series launch
- How to sideload the Digital Wellbeing beta on Pie
- How to manually update the Nokia 7 Plus to Android Pie
- Hands on with the BQ Aquaris X2 Pro
- Hands on with Sony OEMConfig
- The state of Android Enterprise in 2018
- BYOD & Privacy: Don’t settle for legacy Android management in 2018
- Connecting two Synologies via SSH using public and private key authentication
- How to update Rsync on Mac OS Mojave and High Sierra
- Intune gains support for Android Enterprise COSU deployments
- Android Enterprise Recommended: HMD Global launch the Nokia 3.1 and Nokia 5.1
- Android Enterprise Partner Summit 2018 highlights
- Live: MobileIron LIVE! 2018
- Android Enterprise first: AirWatch 9.4 lands with a new name and focus
- Live: Android Enterprise Partner Summit 2018
- Samsung, Oreo and an inconsistent Android Enterprise UX
- MobileIron launch Android Enterprise work profiles on fully managed devices
- Android P demonstrates Google's focus on the enterprise
- An introduction to managed Google Play
- MWC 2018: Android One, Oreo Go, Android Enterprise Recommended & Android Enterprise
- Enterprise ready: Google launch Android Enterprise Recommended
2017
- Year in review: 2017
- Google is deprecating device admin in favour of Android Enterprise
- Hands on with the Sony Xperia XZ1 Compact
- Moto C Plus giveaway
- The state of Android Enterprise in 2017
- Samsung launched a Note 8 for enterprise
- MobileIron officially supports Android Enterprise QR code provisioning
- Android zero-touch enrolment has landed
- MobileIron unofficially supports QR provisioning for Android Enterprise work-managed devices, this is how I found it
- Hands on with the Nokia 3
- Experimenting with clustering and data replication in Nextcloud with MariaDB Galera and SyncThing
- Introducing documentation on bayton.org
- Goodbye Alexa, Hey Google: Hands on with the Google Home
- Restricting access to Exchange ActiveSync
- What is Mobile Device Management?
- 8 tips for a successful EMM deployment
- Long-term update: the fitlet-RM, a fanless industrial mini PC by Compulab
- First look: the FreedomPop V7
- Vault7 and the CIA: This is why we need EMM
- What is Android Enterprise (Android for Work) and why is it used?
- Introducing night mode on bayton.org
- What is iOS Supervision and why is it used?
- Hands on with the Galaxy TabPro S
- Introducing Nextcloud demo servers
- Part 4 - Project Obsidian: Obsidian is dead, long live Obsidian
2016
- My top Android apps 2016
- Hands on with the Linx 12V64
- Wandera review 2016: 2 years on
- Deploying MobileIron 9.1+ on KVM
- Hands on with the Nextcloud Box
- How a promoted tweet landed me on Finnish national news
- Using RWG Mobile for simple, cross-device centralised voicemail
- Part 3 – Project Obsidian: A change, data migration day 1 and build day 2
- Hands on: fitlet-RM, a fanless industrial mini PC by Compulab
- Part 2 - Project Obsidian: Build day 1
- Part 1 - Project Obsidian: Objectives & parts list
- Part 0 - Project Obsidian: Low power NAS & container server
- 5 Android apps improving my Chromebook experience
- First look: Android apps on ChromeOS
- Competition: Win 3 months of free VPS/Container hosting - Closed!
- ElasticHosts review
- ElasticHosts: Cloud Storage vs Folders, what's the difference?
- Adding bash completion to LXD
- Android N: First look & hands-on
- Springs.io - Container hosting at container prices
- Apple vs the FBI: This is why we need MDM
- Miradore Online MDM: Expanding management with subscriptions
- Lenovo Yoga 300 (11IBY) hard drive upgrade
- I bought a Lenovo Yoga 300, this is why I'm sending it back
- Restricting access to Exchange ActiveSync
- Switching to HTTPS on WordPress
2015
2014
- Is CYOD the answer to the BYOD headache?
- BYOD Management: Yes, we can wipe your phone
- A fortnight with Android Wear: LG G Watch review
- First look: Miradore Online free MDM
- Hands on: A weekend with Google Glass
- A month with Wandera Mobile Gateway
- Final thoughts: Dell Venue Pro 11 (Atom)
- Thoughts on BYOD
- Will 2014 bring better battery life?
- My year in review: Bayton.org
- The best purchase I've ever made? A Moto G for my father
2013
2012
- My Top Android Apps 12/12
- The Nexus 7 saga: Resolved
- Recycling Caps Lock into something useful - Ubuntu (12.04)
- The Nexus 7 saga continues
- From Wows to Woes: Why I won't be recommending a Nexus7 any time soon.
- Nexus7: What you need to know
- Why I disabled dlvr.it links on Facebook
- HTC Sense: Changing the lockscreen icons from within ADW
2011
- Push your Google+ posts to Twitter and Facebook
- Using multiple accounts with Google.
- The "Wn-R48" (Windows on the Cr-48)
- Want a Google+ invite?
- Publishing to external sources from Google+
- Dell Streak review. The Phone/Tablet Hybrid
- BlueInput: The Bluetooth HID driver Google forgot to include
- Pushing Buzz to Twitter with dlvr.it
- Managing your social outreach with dlvr.it
- When Awe met Some. The Cr-48 and Gnome3.
- Living with Google's Cr-48 and the cloud.
- Downtime 23-25/04/2011
- Are you practising "safe surfing"?
- The Virtualbox bug: "Cannot access the kernel driver" in Windows
- Putting tech into perspective
2010
- Have a Google Buzz Christmas
- Root a G1 running Android 1.6 without recovery!
- Windows 7 display issues on old Dell desktops
- Google added the Apps flexibility we've been waiting for!
- Part I: My 3 step program for moving to Google Apps
- Downloading torrents
- Completing the Buzz experience for Google Maps Mobile
- Quicktip: Trial Google Apps
- Quicktip: Save internet images fast
- Turn your desktop 3D!
- Part III - Device not compatible - Skype on 3
- Swype not compatible? ShapeWriter!
- Don't wait, get Swype now!
- HideIP VPN. Finally!
- Google enables Wave for Apps domains
- Aspire One touch screen
- Streamline XP into Ubuntu
- Edit a PDF with Zamzar
- Google offering Gmail addresses in the UK
- Google Wave: Revolutionising blogs!
- Hexxeh's Google Chrome OS builds
- Update: Buzz on Windows Mobile
- Alternatives to Internet Explorer
- Wordress 3.0 is coming!
- Skype for WM alternatives
- Browsing on a (data) budget? Opera!
- Buzz on unsupported mobiles
- Buzz on your desktop
- What's all the Buzz?
- Part II: Device not compatible - Skype on 3
- Part I - Device not compatible - Skype on 3
- Dreamscene on Windows 7
- Free Skype with 3? There's a catch..
Wandera review 2016: 2 years on
Contents
Back in 2014 I came across a new, powerful and totally unique solution to the growing problem of telecoms expense management (TEM) in the enterprise: Wandera. It offered unparalleled insight into data usage across the corporate mobile estate and helped tremendously in the never-ending quest to monitor and control data usage both at home and abroad.
I’m really, really impressed by how the solution works and how theoretically easy Wandera makes it to manage devices. Considering at the moment I’ve got very little insight into how users use their allocated data on a monthly basis, Wandera really appeals to me.
It wasn’t perfect however, missing functionality I felt made bulk-deployment something of a challenge; even adding additional administrators required a ticket to be raised with Wandera support. For the benefits Wandera offered though, I was willing to mostly overlook the drawbacks for what was otherwise a fantastic new service with a lot of potential.
As it turns out, being a simple data monitoring solution wasn’t enough for the good people of Wandera; not too long after my first review they announced they were entering the security sector. Today, two years later and after pivoting their focus to mobile threat defense, let’s see what’s changed, what’s remained the same and where there’s still room for improvement.
How does Wandera work?
#Unlike typical EMM platforms with TEM built in or even popular data monitoring applications that estimate and/or periodically report data usage, Wandera acts as a proxy (or “gateway”), taking control of the APN settings of enrolled devices in order to divert all cellular traffic through Wandera servers where it is analysed, compressed and forwarded on to its final destination in real time.
With policies, data caps and traffic shaping at its core, Wandera has the ability to block traffic on the fly whether due to a restricted site/genre, a soft data cap, a detected security issue or simply switching over to a roaming profile. It can do this while still providing access to core corporate services such as Exchange so as not to prevent employees from performing their job function. How Wandera behaves is entirely down to how the administrator sets up the various policies.
Some traffic cannot be optimised due to SSL encryption and therefore a lack of visibility of the data it captures. In these circumstances, Wandera simply measures the amount of traffic passing through and counts it up against the respective device in the console. The data that can be compressed however can help to considerably lower data usage and, in combination with real-time reports, alerts and data blocking, Wandera can help to almost completely eliminate bill-shock.
Logging in
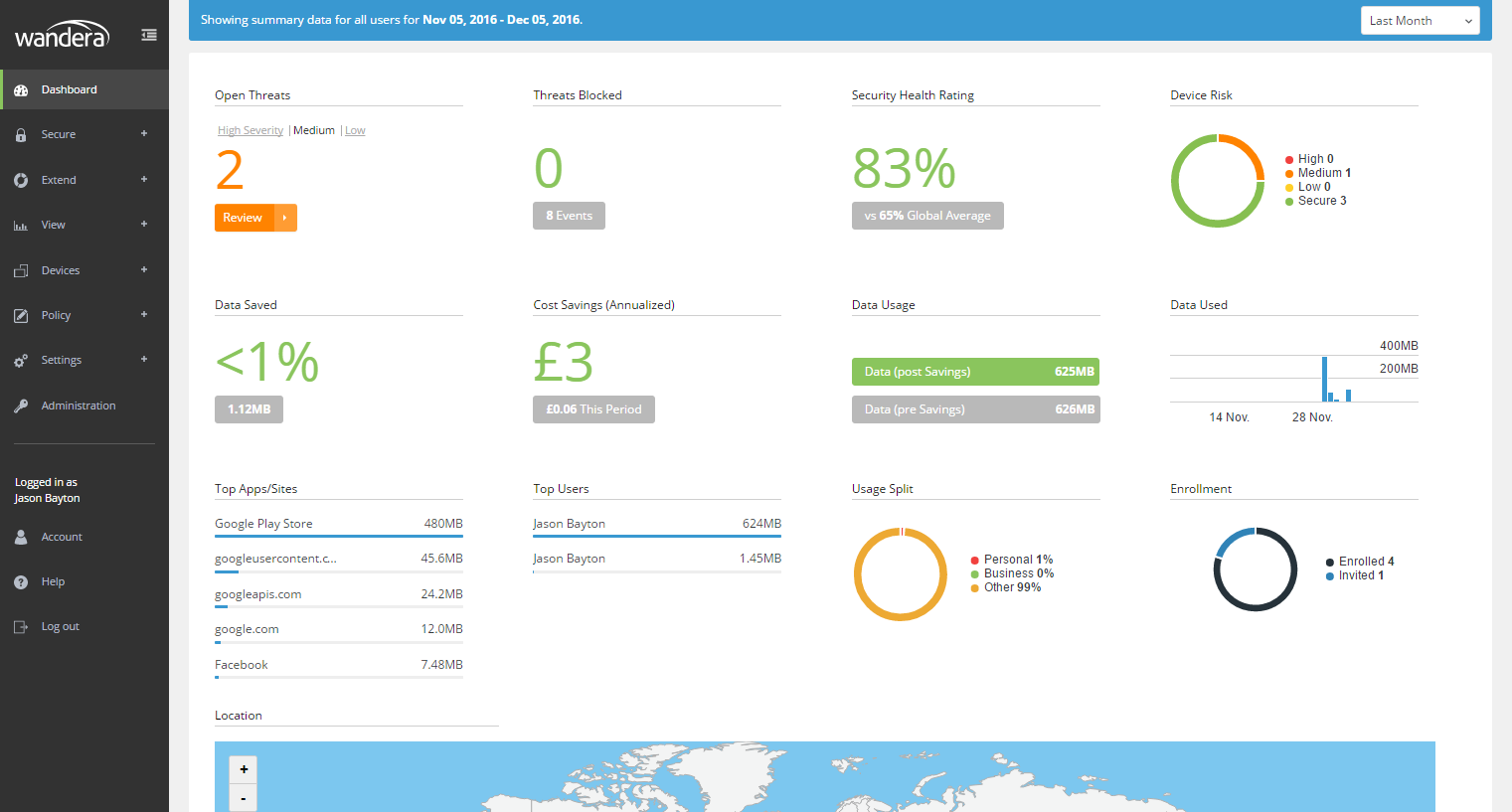
#On logging into the console at https://radar.wandera.com, I’m greeted with a familiar, though busier dashboard offering a redesigned overview featuring a new focus on mobile threat defense at the very top; this shows threats and risk for mobile devices enrolled on the platform. Below this are the familiar data usage metrics, savings provided by Wandera’s compression engine and an overview of on what (and where) data has been used.
On the left I notice there are a number of new areas in the navigation, including Secure, Administration, and Policy which I’ll touch on below.
The dashboard is now much cleaner and offers more information at a glance. It’s a nice update on what was already a very useful landing page.
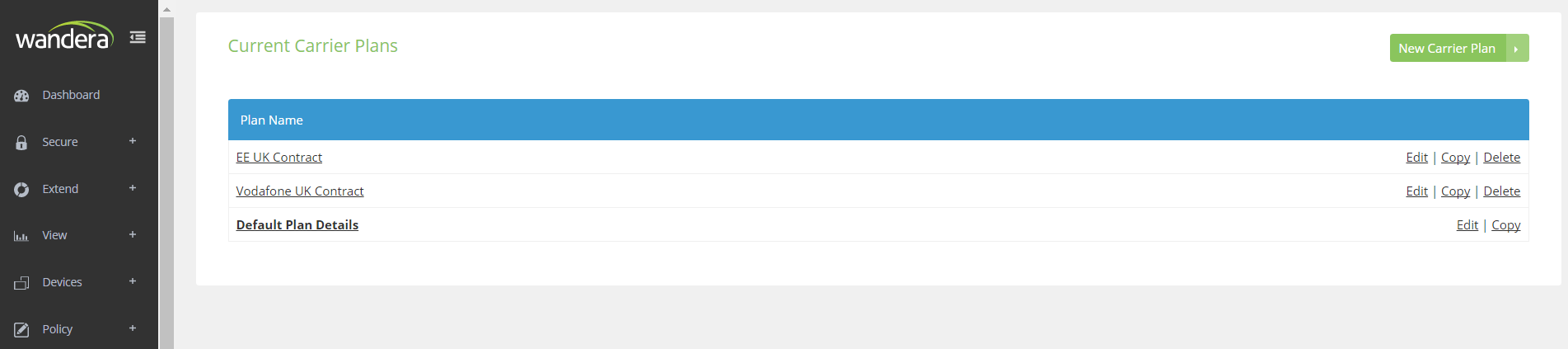
Estimated cost savings
#The cost savings demonstrated in the dashboard above are only accurate after configuring the default (and any other) Plan Details located in Settings.
Enrolling a device
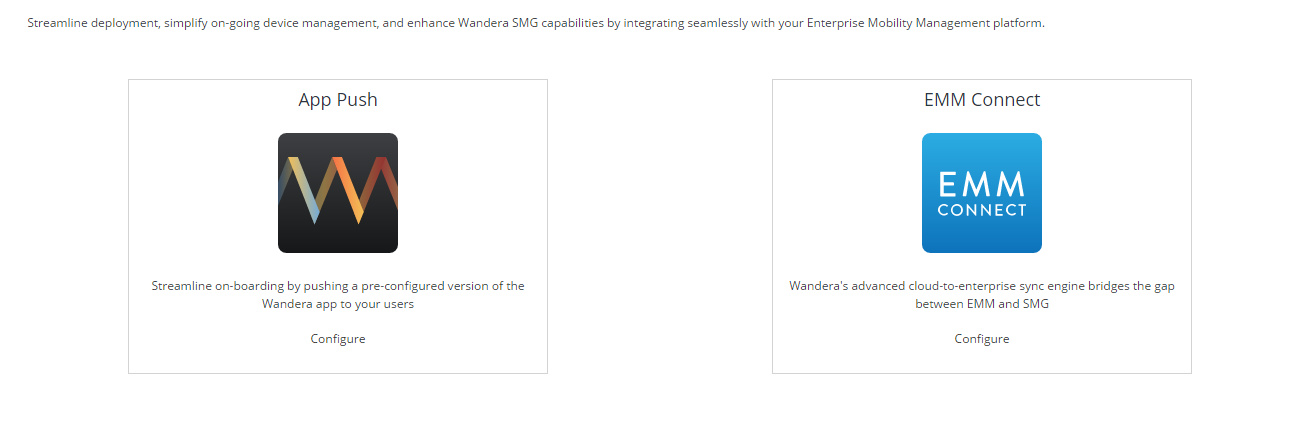
#Device enrolment is definitely an area that has seen some significant improvement over the last two years. While the traditional single and bulk enrolment options still exist from within the Wandera console, they have since expanded the number of EMM solutions App Push works with and have introduced a feature that I find particularly exciting – EMM Connect.
What’s the difference?
#App Push was the first attempt at EMM integration and today still supports the highest number of EMM platforms.
Using the EMM-provided Application Management tools, the Wandera app can be imported into the EMM platform, staged using provisioning keys unique to each Wandera customer and distributed automatically to enrolled devices. When the end-user then opens the Wandera application, it will provision automatically with only a few taps required to confirm profile installation.
This is the process on iOS at least and is definitely smoother than on Android, wherein an additional activation app is required for the provisioning steps which can later be removed. I picture this improving in the near future with the uptick in Android for Work deployments and although Wandera don’t support AfW currently, the Wandera App appears to be compatible (though not enabled) in some preliminary testing I undertook.
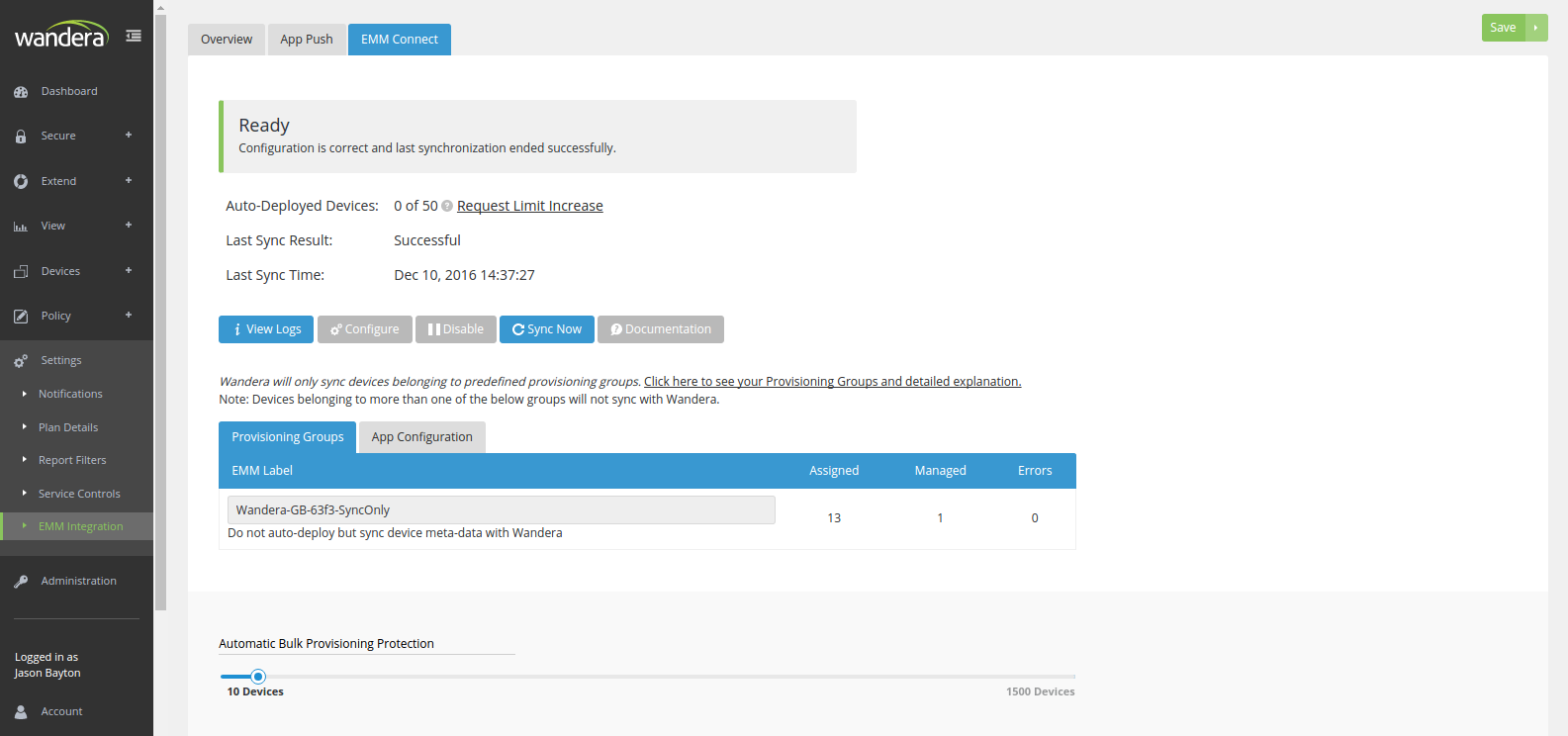
EMM Connect, by contrast, utilises the APIs of popular EMM platforms AirWatch and MobileIron to automatically sync and provision EMM-enrolled devices/users with Wandera, without all of the extra hands-on required with provisioning keys as used with App Push, the app itself will still need to be distributed though .
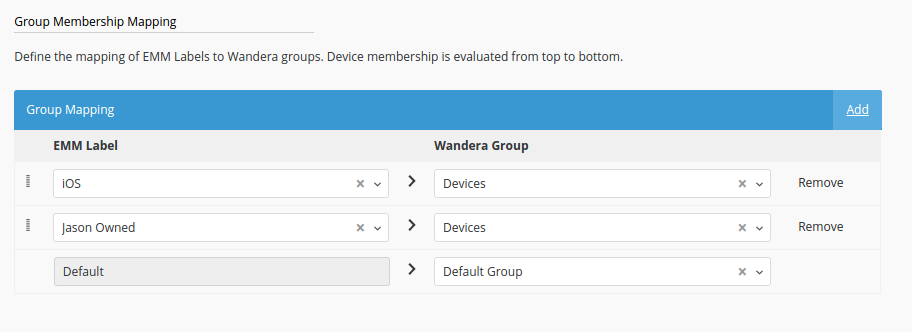
EMMC once connected will generate a unique EMM label to be created within the EMM platform. All devices assigned to this label will then be synced to Wandera automatically and provisioned on launch of the Wandera app. Furthermore, Wandera can see any other groups/labels through the EMM API and allows administrators to assign different labels to various Wandera Groups, an excellent and simple way of dynamically assigning devices to group-based data policies.
Wandera Groups
#Wandera Groups, much like groups or labels in EMM products, allow for multiple unique policies to be applied to devices based on group membership and dramatically increase the flexibility of the platform. Data policies can then be set according to department, operating system and more.
As of publishing, EMMC only works with iOS devices and while silent provisioning is an option, it requires the devices be Supervised and/or enrolled onto Apple’s Device Enrolment Program (DEP); non-supervised iOS users will be prompted to manually allow the installation of the relevant profiles, a familiar process for those who have previously enrolled onto an EMM platform.
A further benefit of Supervision is the ability to manage not only mobile data but WIFI also. It has long been the case that no matter what rules are put in place to block access to various services, switching on WIFI circumvents it all. Once Supervised this is no longer the case.
In testing I found the EMMC method was very reliable, though it took a few days to get set up due to using Let’s Encrypt SSL certificates for my MobileIron Core. I worked with Wandera to get these certificates supported as I know for a fact they will only grow in popularity as time goes on. From here on out that will no longer be an issue.
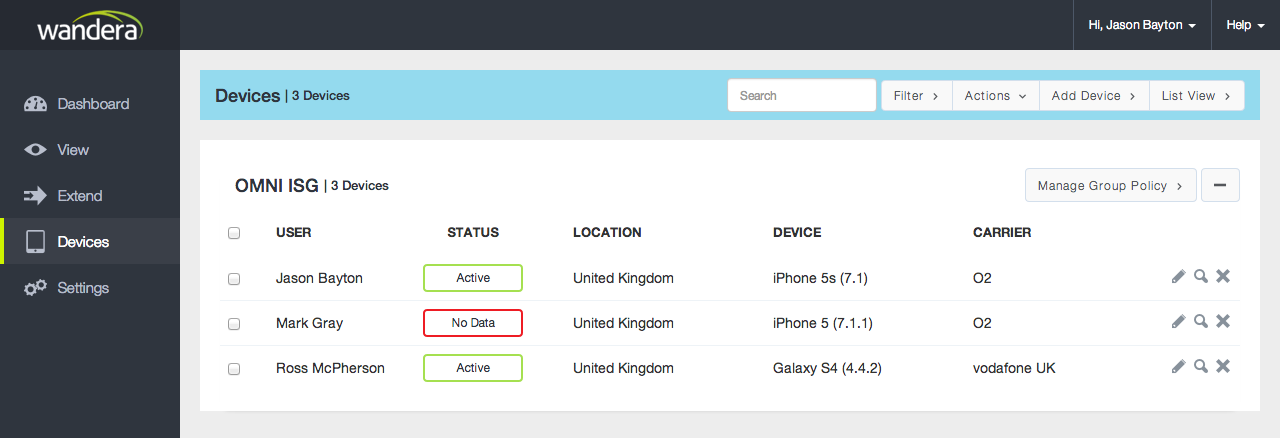
Here’s how an EMM-connected device is displayed within the console:
I look forward to seeing Android devices supported in EMMC, once again perhaps in tandem with Android for Work we will soon see far more opportunities for integration on par with what iOS users get today.
What’s supported?
#One of my biggest criticisms of Wandera was only offering support for iOS and Samsung – not Android, just Samsung devices. Two years on and unfortunately nothing has changed in this regard; Wandera will not run on Android devices except those by Samsung due to the required APIs in the AOSP simply being non-existent.
It’s no secret Samsung is the Android Enterprise manufacturer; with SAFE, KNOX and the respective APIs available with these solutions that simply don’t exist in other Android OEMs, it’s no surprise Wandera are only focused on working with the platforms they know they can support reliably.
That doesn’t mean I like it however. With no less than 7 Android devices of varying ages in my house, I still had to go out and buy a Samsung Galaxy (J3, for those interested) in order to be able to review the Wandera platform from an Android perspective. It’s my hope that as Android for Work evolves, these APIs currently exclusive to Samsung will be replicated on all OEM devices out of the box in the near future. I’ve mentioned AfW several times in this review already with good reason, it should completely change the game for Android management as it matures.
Setting up plans and data policies
#Wandera have introduced the Policies heading which brings both Data Policy and Business/Personal across from the previous location in Settings, along with a new Security Policies configuration discussed further below.
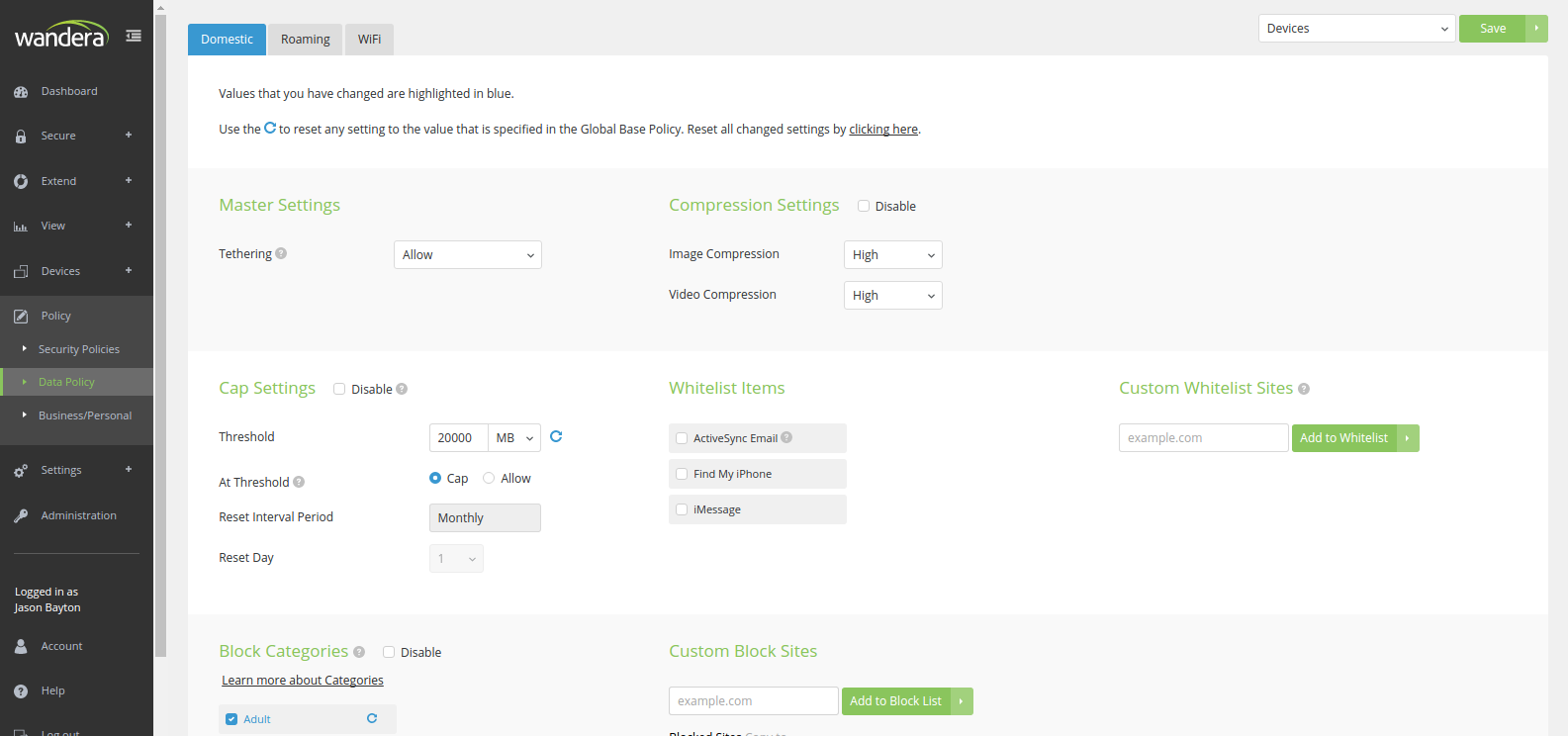
Data policies provide limitations around how data can be used for managed devices. Different policies can be created for different groups, for example in the image above I have limited data to 20GB per month, allowing tethering but setting compression to its most aggressive level in order to preserve some bandwidth where possible. This is only for devices in the Devices group and won’t affect anyone else.
Above the group level is a Global policy in which settings such as Reset Interval Period and Reset Day are set globally. As the screenshot above shows this cannot then be changed on the group-level, a possible problem in an environment where different providers with different billing dates operate together.
Different caps and limitations can be enforced for different situations: domestic, roaming and (where supported) WIFI. This means it’s possible to disable tethering and prevent data being used excessively abroad, even if the policy is rather liberal at home.
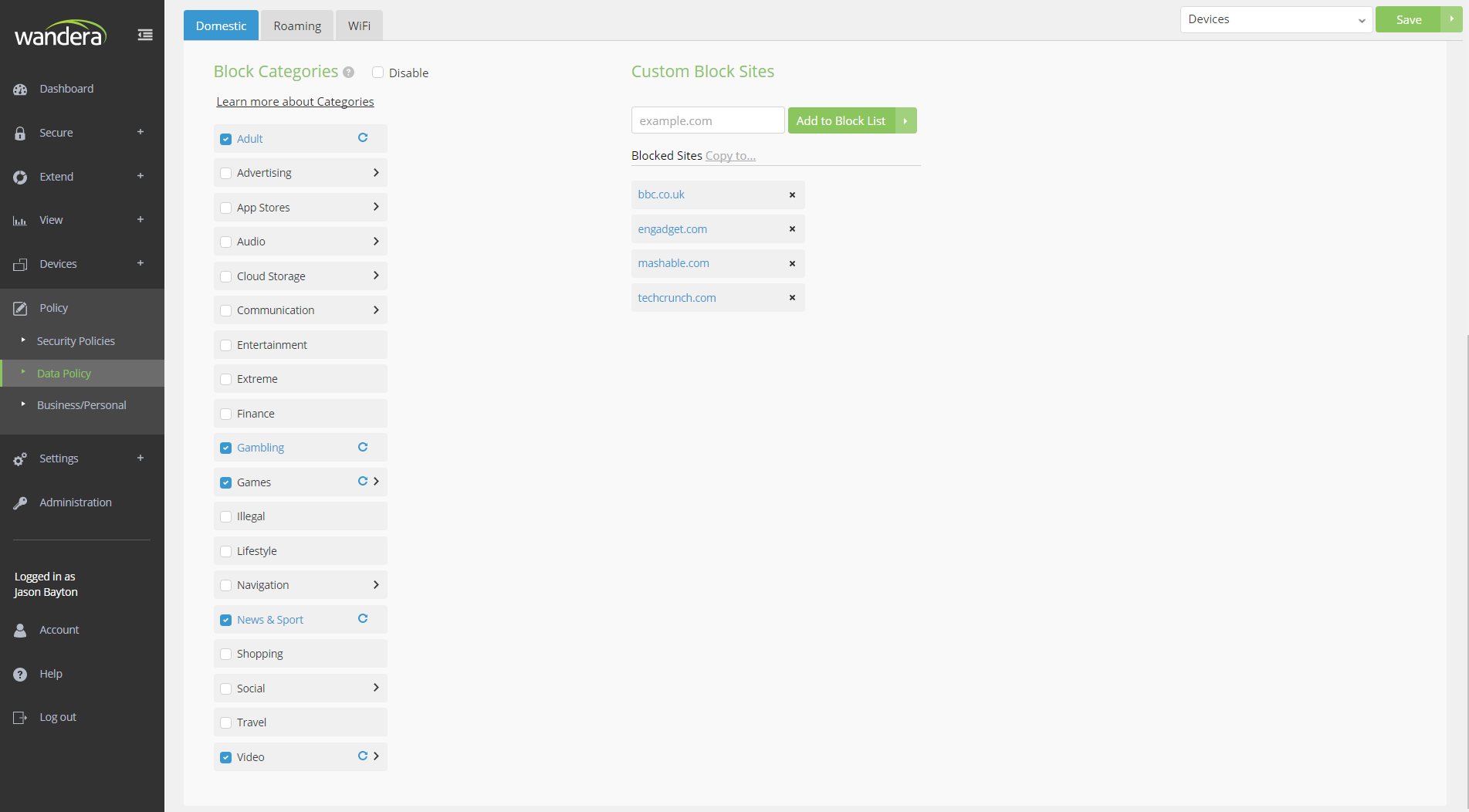
Furthermore, anything from one particular website to a full range of sites under any one of several categories can be blocked, as shown here:
In the above example, among other things I have blocked both News & Sport as a genre, but also techcrunch.com as an individual website. As soon as this policy is saved devices are updated immediately and all blocks are enforced without any further action required from the administrator.
One of the best features here I think is the whitelist; a common conundrum I hear is how to effectively stop users from running up huge bills once they’ve breached their data allowance, but at the same time avoid cutting them off completely to the point where they can no longer do their job. Whitelisting applications such as email or iMessage (or anything else) allows the user to remain online in a capacity that is controlled by the business until such time a new billing period starts or an additional bundle can be added, offering data at a much cheaper rate than those incurred through overages.
For those who’ve adopted BYOD, Business/Personal is simply a collection of checkboxes that allow traffic to be appropriately categorised. Facebook, for example, would usually be marked as a personal site and can therefore be reported as such within Wandera to aid with reimbursements based on usage.
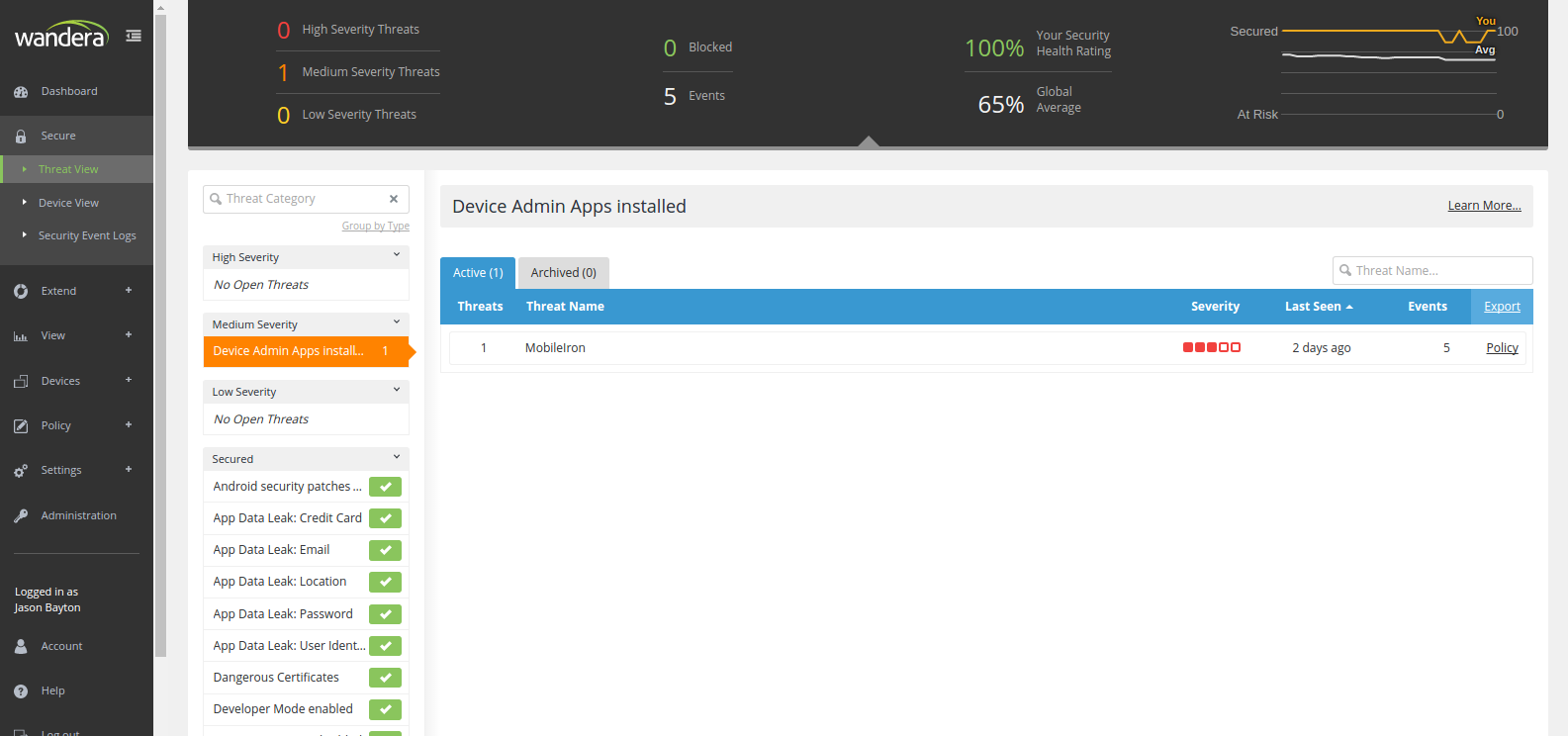
Secure devices
#Secure is a new function that encompasses mobile threat defense and content filtering to prevent targeted mobile attacks, identify data leaks, and filter access to risky or unapproved usage. It does this by not only reviewing the sites visited, but also the state of the device itself (as demonstrated above). In testing I found it could be a little over-sensitive (MobileIron, my EMM platform, is naturally going to be a device admin) but the insight Secure offers generally is both vast and incredibly useful. Some of the security threats it’ll pick up on include:
- Data leakage (unencrypted transport) of email, credit card info, authentication credentials
- Developer mode
- Android root / iOS jailbreak
- OS version, security patch levels
- Bad apps
- Risky WIFI APs
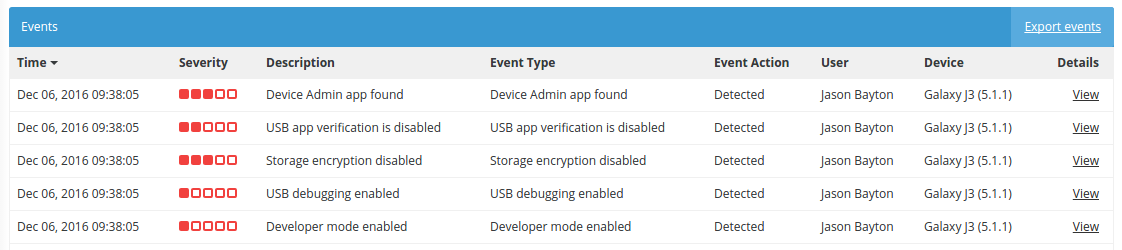
In fact, just looking at the Event Logs gives an indication of what has been detected on my device over the last week:
Some of these are less severe (according to Wandera) than others, though ultimately the administrator has the ability to either receive alerts on detection or ignore these events all together. By default these are reported silently, requiring the administrator to actively investigate. I’m OK with this as typically being bombarded by email alerts doesn’t particularly excite me. Notifications can be set up in Settings > Notifications.
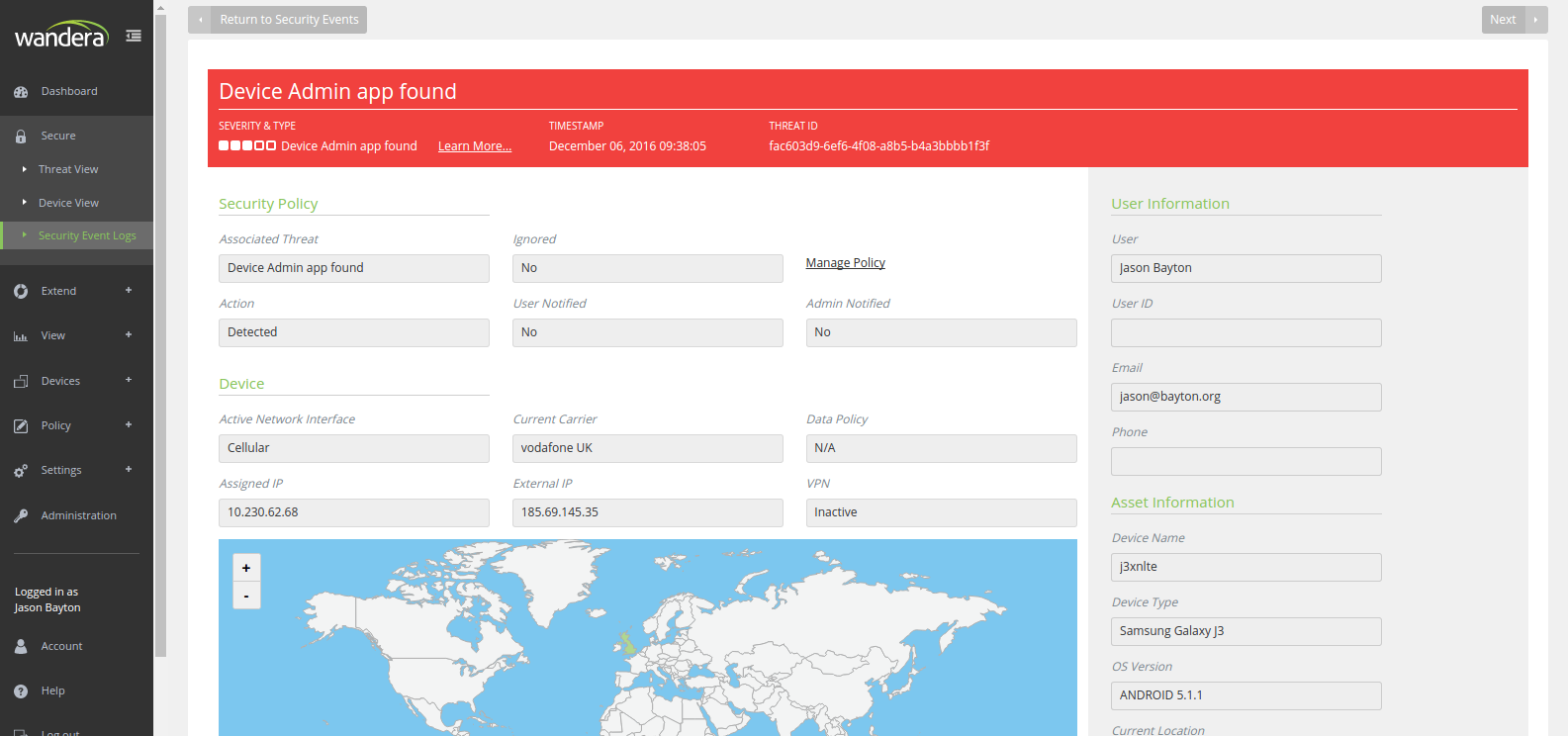
Each event listed can be drilled down further in order to provide more context around the device it was flagged against:
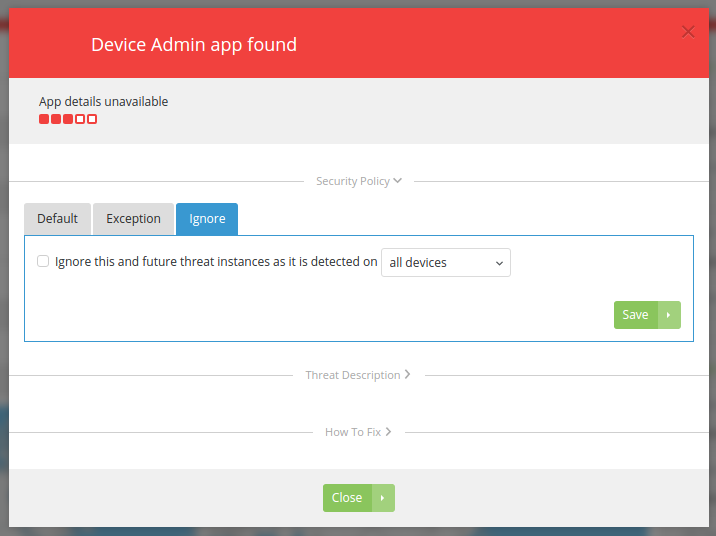
If an event, such as Device Admin app found is not a concern, it can be turned off by clicking Manage Policy in the above screenshot:
The issue I see here is I can seemingly only turn all Device Admin alerts off for one device or all devices. While I’m confident MobileIron in this case is safe, there’s no guarantee anything a user installs requiring Device Admin later would be. I’d rather turn it off on a case-by-case basis, opting to whitelist MobileIron or any other perceived low-risk Device Admin at the moment it is brought to the administrator’s attention.
Security Policies
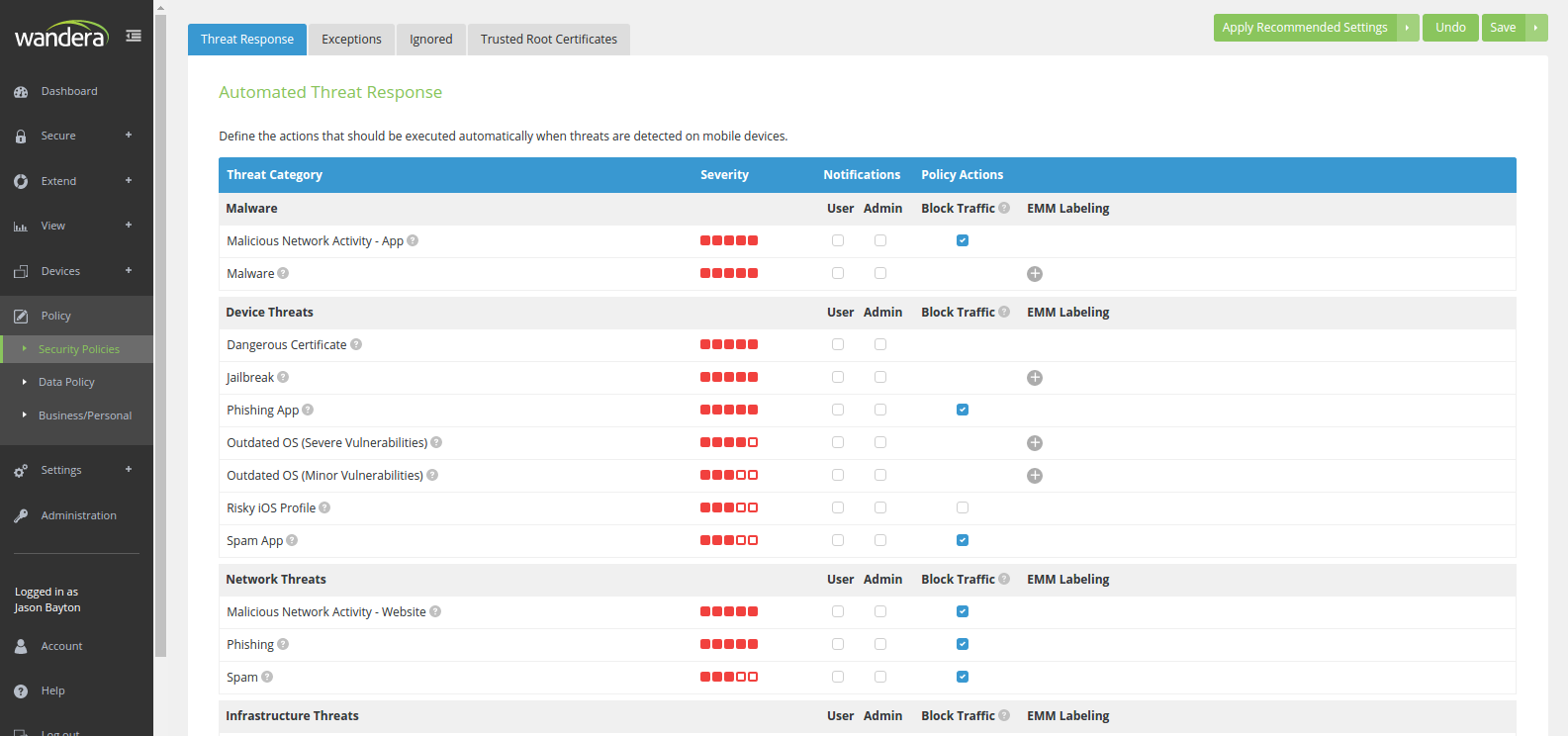
#Naturally reporting any security concerns is nice, but it’s only half a solution; Wandera have as such also introduced Security Policies that sit within the new Policies area of the console to enable automated actions based on the incident detected.
By default Wandera has a number of Recommended Settings enabled to offer out-of-the-box protection, including blocking traffic for phishing apps or credit card information being transferred over unencrypted channels, though again no alerts are set up to avoid swamping administrators (or users!). As an administrator it’s additionally possible to manage exceptions, rule ignores and supply trusted root certificates to aid in the prevention of false positives and unimportant alerts.
In testing I wasn’t able to replicate a scenario whereby traffic would be blocked due to a security concern – partly because I had no intention of downloading a phishing app, but also with everything generally quite secure browsing around my typical sites there wasn’t much in the way of opportunities to do so.
Managing the console
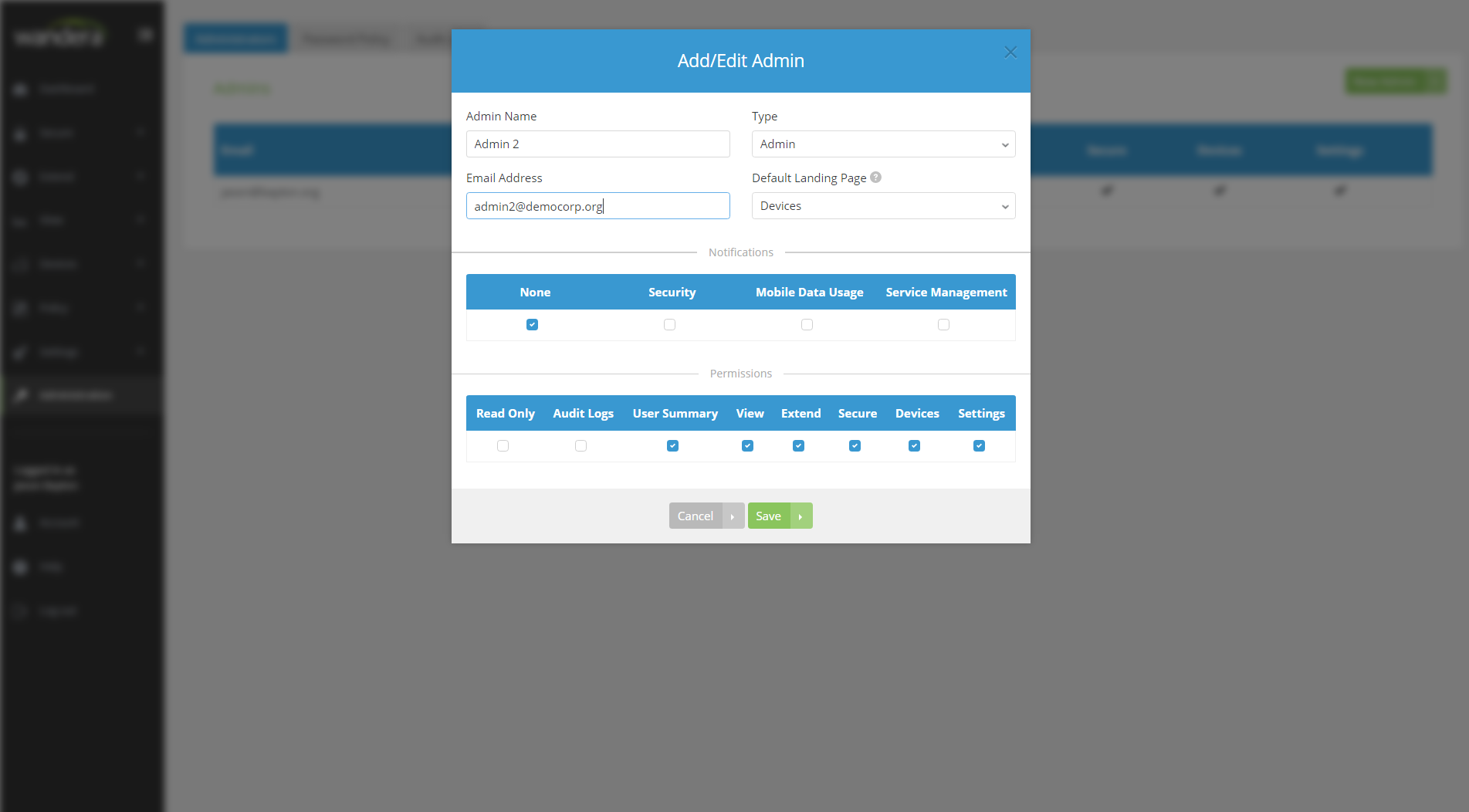
#I’m pleased to see since my last look at Wandera it’s no longer necessary to submit a support ticket in order to add another administrator. This was an immensely basic necessity which I couldn’t believe was overlooked initially, but adding additional admins today is a piece of cake.
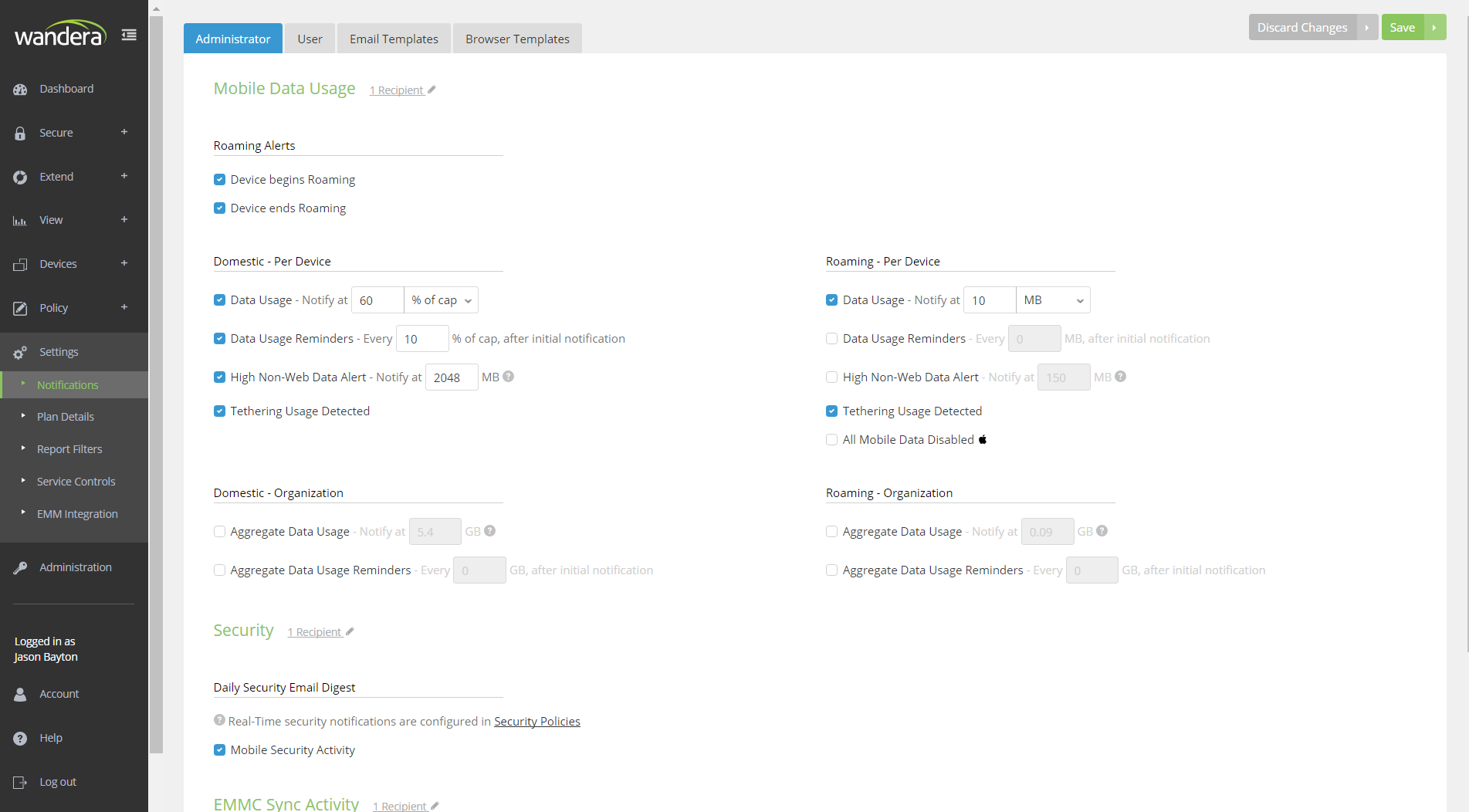
Other than this, notifications can easily be set up through Settings > Notifications, allowing for very simple yes/no decisions on what alerts should be sent to the admin, the user or nowhere at all.
Other changes
#As with the dashboard, a number of changes since my last review appear to be mostly cosmetic – offering a better layout with more information at a glance. Wandera have again dropped the dated design:
In favour of a much cleaner, nicer interface with richer filtering and search options:
Devices
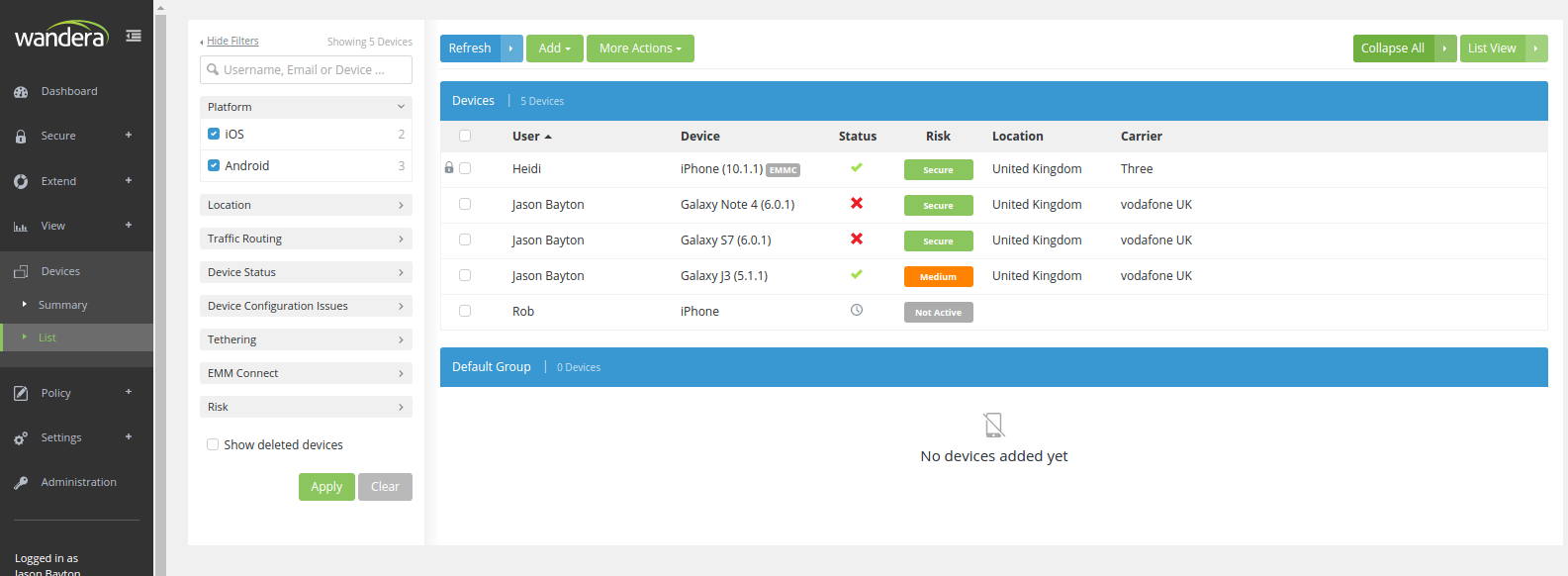
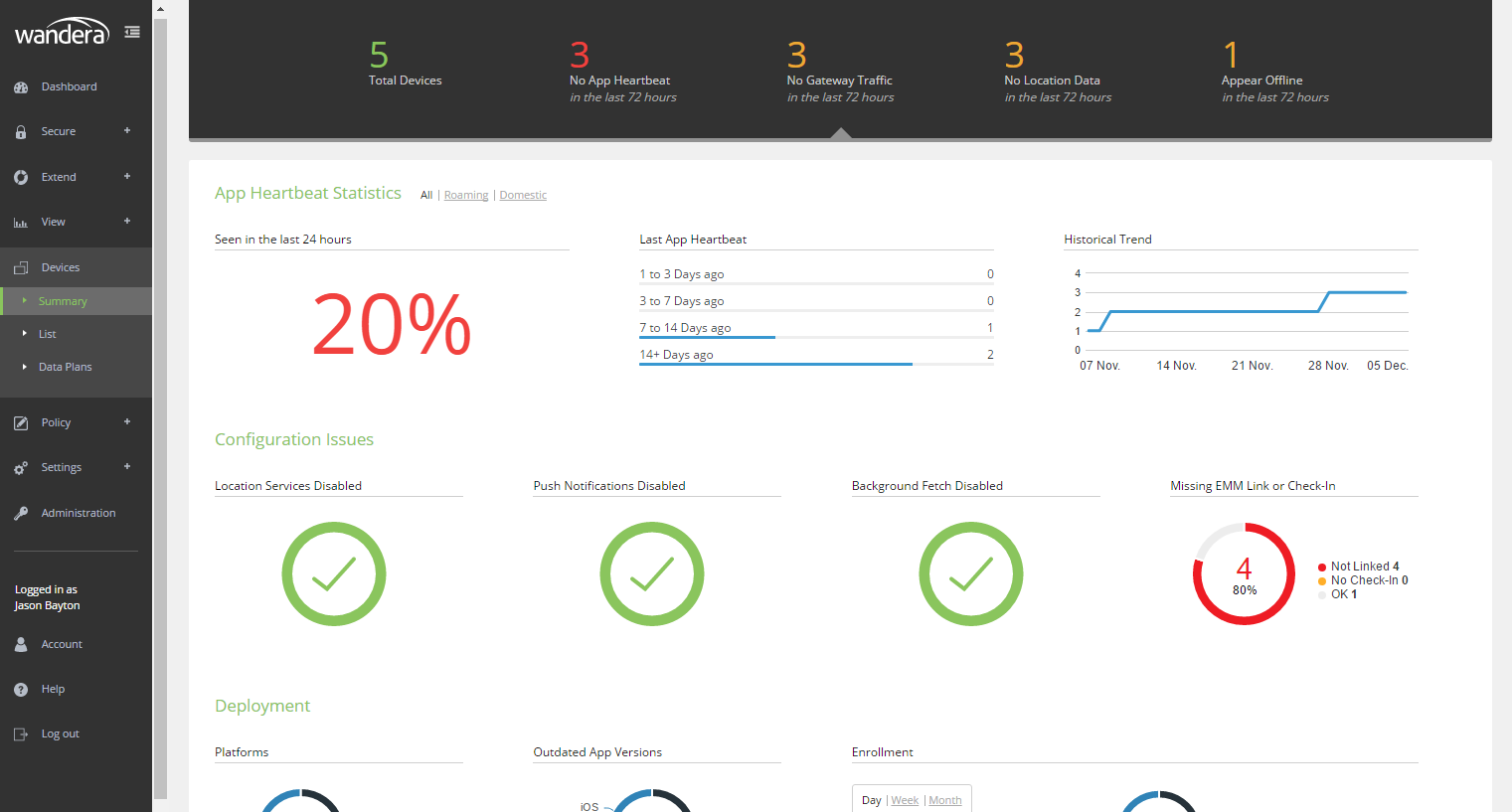
#In addition for Devices, Wandera have added a Summary view which is not drastically different from that of the dashboard:
Though it does offer a somewhat different visualisation of the data available, instead focusing on device availability and connectivity to the Wandera platform. Admittedly I didn’t find myself looking at this too often with such a small deployment of devices, but it’s not dissimilar to the dashboard views I’m used to seeing (and heavily utilising) on various EMM platforms.
View
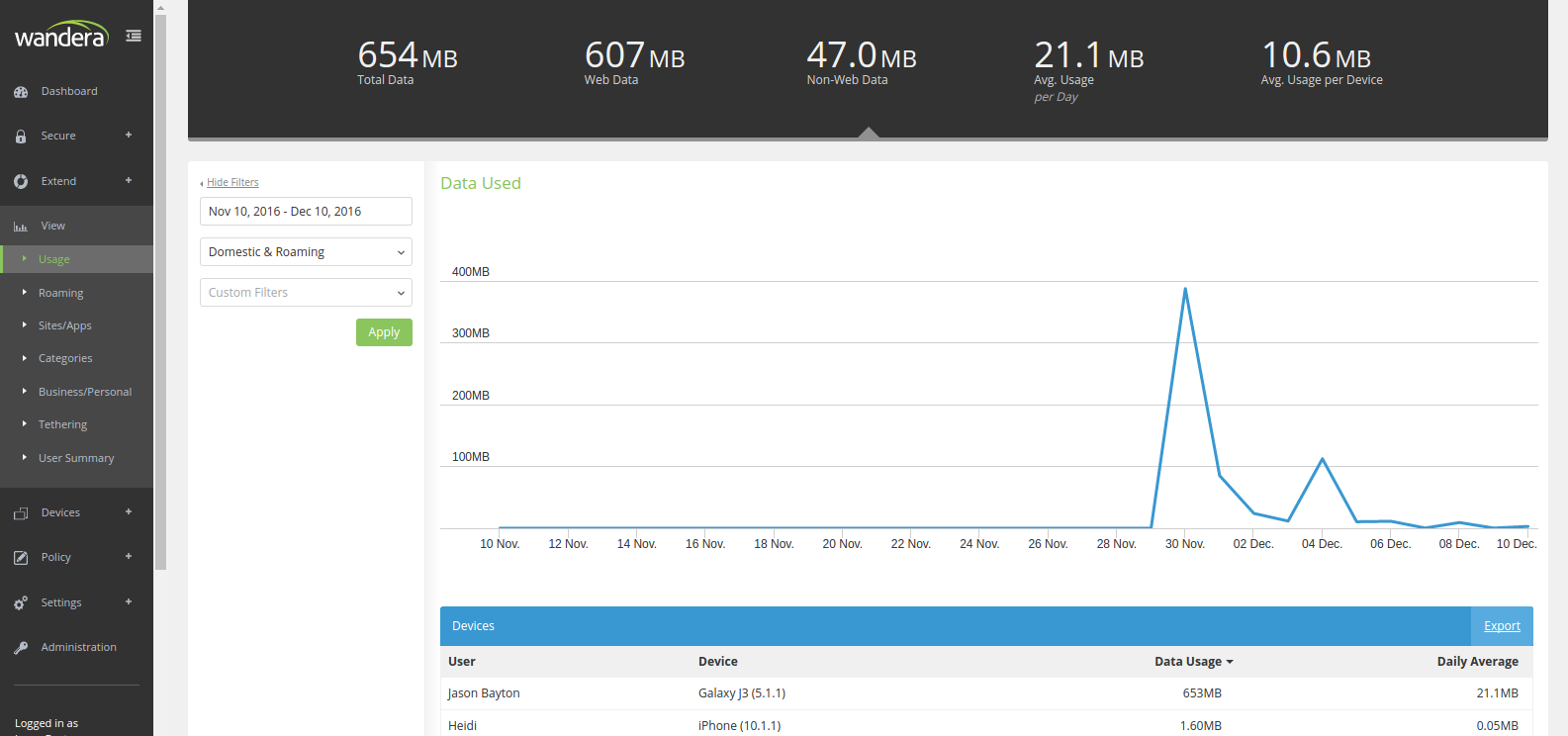
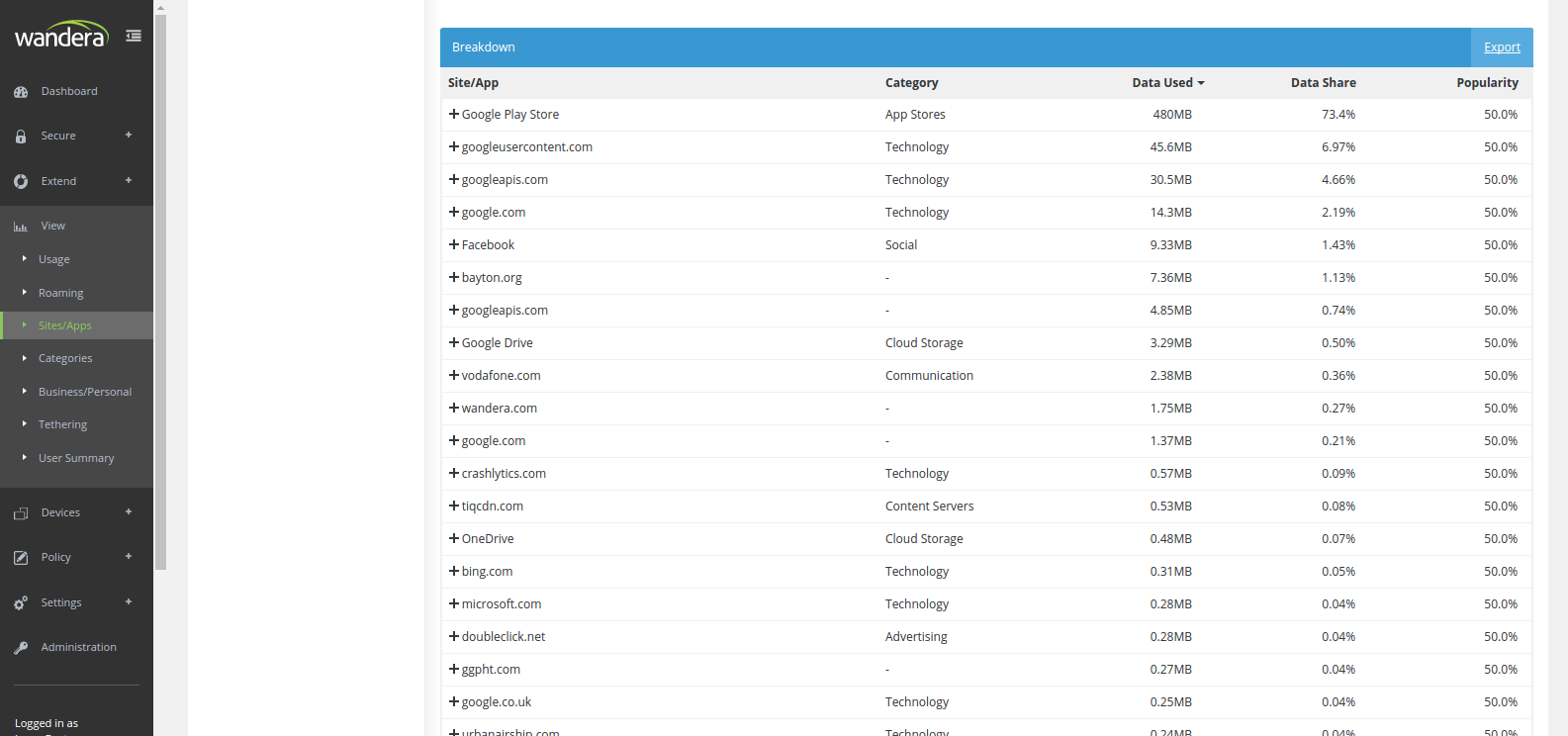
#One of the more interesting features under View was Real-Time which gave an indication of the data passing through the server as it happened. It was a little gimmicky perhaps, but for troubleshooting purposes was probably as close to a tool as Wandera offers for administrators. Unfortunately that’s now gone, but the excellent tables and graphs showing data usage clearly, along with the apps and sites frequented by users, is still all very much present:
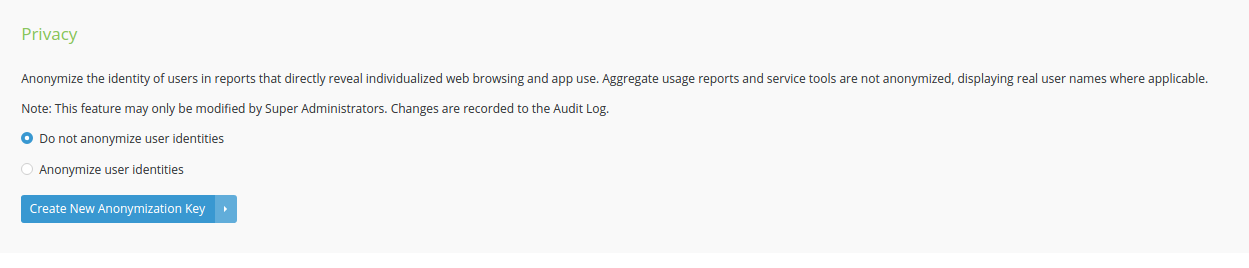
An interesting addition I don’t recall seeing in the past is under Settings > Service Controls. Particularly in the run-up to the new General Data Protection Regulation (GDPR), having the ability to anonymise reported data feels like a crucial necessity to prevent huge fines for breaches of data protection:
For those interested, Wandera themselves have published a whitepaper outlining the implications of GDPR.
The user experience
#As an end-user it can obviously be frustrating if out of nowhere websites are blocked and data caps are enforced. Wandera however do a really good job of keeping the user informed and the application is completely transparent in showing what limits are applied to the device as well as why a site may have failed to load.
Furthermore, there’s a really nice data monitor built in so a user will never not be able to know how much data they’ve used and how much is left.
Browsing with blocks in place:
Browsing the Wandera app:
Conclusion
#I’m impressed by the changes and new features I’ve seen once again with Wandera and maintain it’s one of the best solutions for TEM on the market today. Combined with the new mobile threat defense features ensuring devices are safe and compliant, it feels almost untouchable against the competition as an all-in-one solution.
Wandera works reliably, integrates well into existing EMM platforms for simple (bulk) provisioning, offers a completely transparent user experience and provides all the tools necessary to ensure bills remain well and truly within budget.
I’ve by no means covered everything here again, but I’d hope this review gives a good overview of what Wandera is, does and how it can help. If you have questions or comments, or would like to see more reviews, guides or general chat about Wandera here, let me know and I’ll be sure to write more about it in the future.
As always I’m @jasonbayton on Twitter, @bayton.org on Facebook and will also respond to comments below.
If you spot any errors in the above or have suggestions on how to improve this review, feel free to reach out.
Articles
2025
- The Android Management API doesn't support pulling managed properties (config) from app tracks. Here's how to work around it
- Hands-on with CVE-2025-22442, a work profile sideloading vulnerability affecting most Android devices today
- AAB support for private apps in the managed Google Play iFrame is coming, take a first look here
- What's new (so far) for enterprise in Android 16
2024
- Android 15: What's new for enterprise?
- How Goto's acquisition of Miradore is eroding a once-promising MDM solution
- Google Play Protect no longer sends sideloaded applications for scanning on enterprise-managed devices
- Mobile Pros is moving to Discord
- Avoid another CrowdStrike takedown: Two approaches to replacing Windows
- Introducing MANAGED SETTINGS
- I'm joining NinjaOne
- Samsung announces Knox SDK restrictions for Android 15
- What's new (so far) for enterprise in Android 15
- Google quietly introduces new quotas for unvalidated AMAPI use
- What is Play Auto Install (PAI) in Android and how does it work?
- AMAPI publicly adds support for DPC migration
- How do Android devices become certified?
2023
- Mute @channel & @here notifications in Slack
- A guide to raising better support requests
- Ask Jason: How should we manage security and/or OS updates for our devices?
- Pixel 8 series launches with 7 years of software support
- Android's work profile behaviour has been reverted in 14 beta 5.3
- Fairphone raises the bar with commitment to Android updates
- Product files: The DoorDash T8
- Android's work profile gets a major upgrade in 14
- Google's inactive account policy may not impact Android Enterprise customers
- Product files: Alternative form factors and power solutions
- What's new in Android 14 for enterprise
- Introducing Micro Mobility
- Android Enterprise: A refresher
2022
- What I'd like to see from Android Enterprise in 2023
- Thoughts on Android 12's password complexity changes
- Google Play target API requirements & impact on enterprise applications
- Sunsetting Discuss comment platform
- Google publishes differences between Android and Android Go
- Android Go & EMM support
- Relaunching bayton.org
- AER dropped the 3/5 year update mandate with Android 11, where are we now?
- I made a bet with Google (and lost)
2020
- Product files: Building Android devices
- Google announce big changes to zero-touch
- VMware announces end of support for Device Admin
- Google launch the Android Enterprise Help Community
- Watch: An Android Enterprise discussion with Hypergate
- Listen again: BM podcast #144 - Jason Bayton & Russ Mohr talk Android!
- Google's Android Management API will soon support COPE
- Android Enterprise in 11: Google reduces visibility and control with COPE to bolster privacy.
- The decade that redefined Android in the enterprise
2019
- Why Intune doesn't support Android Enterprise COPE
- VMware WS1 UEM 1908 supports Android Enterprise enrolments on closed networks and AOSP devices
- The Bayton 2019 Android Enterprise experience survey
- Android Enterprise Partner Summit 2019 highlights
- The Huawei ban and Enterprise: what now?
- Dabbling with Android Enterprise in Q beta 3
- Why I moved from Google WiFi to Netgear Orbi
- I'm joining Social Mobile as Director of Android Innovation
- Android Enterprise in Q/10: features and clarity on DA deprecation
- MWC 2019: Mid-range devices excel, 5G everything, form-factors galore and Android Enterprise
- UEM tools managing Android-powered cars
- Joining the Android Enterprise Experts community
- February was an interesting month for OEMConfig
- Google launch Android Enterprise Recommended for Managed Service Providers
- Migrating from Windows 10 Mobile? Here's why you should consider Android
- AER expands: Android Enterprise Recommended for EMMs
- What I'd like to see from Android Enterprise in 2019
2018
- My top Android apps in 2018
- Year in review: 2018
- MobileIron Cloud R58 supports Android Enterprise fully managed devices with work profiles
- Hands on with the Huawei Mate 20 Pro
- Workspace ONE UEM 1810 introduces support for Android Enterprise fully managed devices with work profiles
- G Suite no longer prevents Android data leakage by default
- Live: Huawei Mate series launch
- How to sideload the Digital Wellbeing beta on Pie
- How to manually update the Nokia 7 Plus to Android Pie
- Hands on with the BQ Aquaris X2 Pro
- Hands on with Sony OEMConfig
- The state of Android Enterprise in 2018
- BYOD & Privacy: Don’t settle for legacy Android management in 2018
- Connecting two Synologies via SSH using public and private key authentication
- How to update Rsync on Mac OS Mojave and High Sierra
- Intune gains support for Android Enterprise COSU deployments
- Android Enterprise Recommended: HMD Global launch the Nokia 3.1 and Nokia 5.1
- Android Enterprise Partner Summit 2018 highlights
- Live: MobileIron LIVE! 2018
- Android Enterprise first: AirWatch 9.4 lands with a new name and focus
- Live: Android Enterprise Partner Summit 2018
- Samsung, Oreo and an inconsistent Android Enterprise UX
- MobileIron launch Android Enterprise work profiles on fully managed devices
- Android P demonstrates Google's focus on the enterprise
- An introduction to managed Google Play
- MWC 2018: Android One, Oreo Go, Android Enterprise Recommended & Android Enterprise
- Enterprise ready: Google launch Android Enterprise Recommended
2017
- Year in review: 2017
- Google is deprecating device admin in favour of Android Enterprise
- Hands on with the Sony Xperia XZ1 Compact
- Moto C Plus giveaway
- The state of Android Enterprise in 2017
- Samsung launched a Note 8 for enterprise
- MobileIron officially supports Android Enterprise QR code provisioning
- Android zero-touch enrolment has landed
- MobileIron unofficially supports QR provisioning for Android Enterprise work-managed devices, this is how I found it
- Hands on with the Nokia 3
- Experimenting with clustering and data replication in Nextcloud with MariaDB Galera and SyncThing
- Introducing documentation on bayton.org
- Goodbye Alexa, Hey Google: Hands on with the Google Home
- Restricting access to Exchange ActiveSync
- What is Mobile Device Management?
- 8 tips for a successful EMM deployment
- Long-term update: the fitlet-RM, a fanless industrial mini PC by Compulab
- First look: the FreedomPop V7
- Vault7 and the CIA: This is why we need EMM
- What is Android Enterprise (Android for Work) and why is it used?
- Introducing night mode on bayton.org
- What is iOS Supervision and why is it used?
- Hands on with the Galaxy TabPro S
- Introducing Nextcloud demo servers
- Part 4 - Project Obsidian: Obsidian is dead, long live Obsidian
2016
- My top Android apps 2016
- Hands on with the Linx 12V64
- Wandera review 2016: 2 years on
- Deploying MobileIron 9.1+ on KVM
- Hands on with the Nextcloud Box
- How a promoted tweet landed me on Finnish national news
- Using RWG Mobile for simple, cross-device centralised voicemail
- Part 3 – Project Obsidian: A change, data migration day 1 and build day 2
- Hands on: fitlet-RM, a fanless industrial mini PC by Compulab
- Part 2 - Project Obsidian: Build day 1
- Part 1 - Project Obsidian: Objectives & parts list
- Part 0 - Project Obsidian: Low power NAS & container server
- 5 Android apps improving my Chromebook experience
- First look: Android apps on ChromeOS
- Competition: Win 3 months of free VPS/Container hosting - Closed!
- ElasticHosts review
- ElasticHosts: Cloud Storage vs Folders, what's the difference?
- Adding bash completion to LXD
- Android N: First look & hands-on
- Springs.io - Container hosting at container prices
- Apple vs the FBI: This is why we need MDM
- Miradore Online MDM: Expanding management with subscriptions
- Lenovo Yoga 300 (11IBY) hard drive upgrade
- I bought a Lenovo Yoga 300, this is why I'm sending it back
- Restricting access to Exchange ActiveSync
- Switching to HTTPS on WordPress
2015
2014
- Is CYOD the answer to the BYOD headache?
- BYOD Management: Yes, we can wipe your phone
- A fortnight with Android Wear: LG G Watch review
- First look: Miradore Online free MDM
- Hands on: A weekend with Google Glass
- A month with Wandera Mobile Gateway
- Final thoughts: Dell Venue Pro 11 (Atom)
- Thoughts on BYOD
- Will 2014 bring better battery life?
- My year in review: Bayton.org
- The best purchase I've ever made? A Moto G for my father
2013
2012
- My Top Android Apps 12/12
- The Nexus 7 saga: Resolved
- Recycling Caps Lock into something useful - Ubuntu (12.04)
- The Nexus 7 saga continues
- From Wows to Woes: Why I won't be recommending a Nexus7 any time soon.
- Nexus7: What you need to know
- Why I disabled dlvr.it links on Facebook
- HTC Sense: Changing the lockscreen icons from within ADW
2011
- Push your Google+ posts to Twitter and Facebook
- Using multiple accounts with Google.
- The "Wn-R48" (Windows on the Cr-48)
- Want a Google+ invite?
- Publishing to external sources from Google+
- Dell Streak review. The Phone/Tablet Hybrid
- BlueInput: The Bluetooth HID driver Google forgot to include
- Pushing Buzz to Twitter with dlvr.it
- Managing your social outreach with dlvr.it
- When Awe met Some. The Cr-48 and Gnome3.
- Living with Google's Cr-48 and the cloud.
- Downtime 23-25/04/2011
- Are you practising "safe surfing"?
- The Virtualbox bug: "Cannot access the kernel driver" in Windows
- Putting tech into perspective
2010
- Have a Google Buzz Christmas
- Root a G1 running Android 1.6 without recovery!
- Windows 7 display issues on old Dell desktops
- Google added the Apps flexibility we've been waiting for!
- Part I: My 3 step program for moving to Google Apps
- Downloading torrents
- Completing the Buzz experience for Google Maps Mobile
- Quicktip: Trial Google Apps
- Quicktip: Save internet images fast
- Turn your desktop 3D!
- Part III - Device not compatible - Skype on 3
- Swype not compatible? ShapeWriter!
- Don't wait, get Swype now!
- HideIP VPN. Finally!
- Google enables Wave for Apps domains
- Aspire One touch screen
- Streamline XP into Ubuntu
- Edit a PDF with Zamzar
- Google offering Gmail addresses in the UK
- Google Wave: Revolutionising blogs!
- Hexxeh's Google Chrome OS builds
- Update: Buzz on Windows Mobile
- Alternatives to Internet Explorer
- Wordress 3.0 is coming!
- Skype for WM alternatives
- Browsing on a (data) budget? Opera!
- Buzz on unsupported mobiles
- Buzz on your desktop
- What's all the Buzz?
- Part II: Device not compatible - Skype on 3
- Part I - Device not compatible - Skype on 3
- Dreamscene on Windows 7
- Free Skype with 3? There's a catch..