Contents
Articles
2026
2025
- Google Play Protect is now the custom DPC gatekeeper, and everyone is a threat by default
- 12 deliveries of AE-mas (What shipped in Android Enterprise in 2025)
- The 12 AE requests of Christmas (2025 Edition)
- RCS Archival and you: clearing up the misconceptions
- Device Trust from Android Enterprise: What it is and how it works (hands-on)
- Android developer verification: what this means for consumers and enterprise
- AMAPI finally supports direct APK installation, this is how it works
- The Android Management API doesn't support pulling managed properties (config) from app tracks. Here's how to work around it
- Hands-on with CVE-2025-22442, a work profile sideloading vulnerability affecting most Android devices today
- AAB support for private apps in the managed Google Play iFrame is coming, take a first look here
- What's new (so far) for enterprise in Android 16
2024
- Android 15: What's new for enterprise?
- How Goto's acquisition of Miradore is eroding a once-promising MDM solution
- Google Play Protect no longer sends sideloaded applications for scanning on enterprise-managed devices
- Mobile Pros is moving to Discord
- Avoid another CrowdStrike takedown: Two approaches to replacing Windows
- Introducing MANAGED SETTINGS
- I'm joining NinjaOne
- Samsung announces Knox SDK restrictions for Android 15
- What's new (so far) for enterprise in Android 15
- Google quietly introduces new quotas for unvalidated AMAPI use
- What is Play Auto Install (PAI) in Android and how does it work?
- AMAPI publicly adds support for DPC migration
- How do Android devices become certified?
2023
- Mute @channel & @here notifications in Slack
- A guide to raising better support requests
- Ask Jason: How should we manage security and/or OS updates for our devices?
- Pixel 8 series launches with 7 years of software support
- Android's work profile behaviour has been reverted in 14 beta 5.3
- Fairphone raises the bar with commitment to Android updates
- Product files: The DoorDash T8
- Android's work profile gets a major upgrade in 14
- Google's inactive account policy may not impact Android Enterprise customers
- Product files: Alternative form factors and power solutions
- What's new in Android 14 for enterprise
- Introducing Micro Mobility
- Android Enterprise: A refresher
2022
- What I'd like to see from Android Enterprise in 2023
- Thoughts on Android 12's password complexity changes
- Google Play target API requirements & impact on enterprise applications
- Sunsetting Discuss comment platform
- Google publishes differences between Android and Android Go
- Android Go & EMM support
- Relaunching bayton.org
- AER dropped the 3/5 year update mandate with Android 11, where are we now?
- I made a bet with Google (and lost)
2020
- Product files: Building Android devices
- Google announce big changes to zero-touch
- VMware announces end of support for Device Admin
- Google launch the Android Enterprise Help Community
- Watch: An Android Enterprise discussion with Hypergate
- Listen again: BM podcast #144 - Jason Bayton & Russ Mohr talk Android!
- Google's Android Management API will soon support COPE
- Android Enterprise in 11: Google reduces visibility and control with COPE to bolster privacy.
- The decade that redefined Android in the enterprise
2019
- Why Intune doesn't support Android Enterprise COPE
- VMware WS1 UEM 1908 supports Android Enterprise enrolments on closed networks and AOSP devices
- The Bayton 2019 Android Enterprise experience survey
- Android Enterprise Partner Summit 2019 highlights
- The Huawei ban and Enterprise: what now?
- Dabbling with Android Enterprise in Q beta 3
- Why I moved from Google WiFi to Netgear Orbi
- I'm joining Social Mobile as Director of Android Innovation
- Android Enterprise in Q/10: features and clarity on DA deprecation
- MWC 2019: Mid-range devices excel, 5G everything, form-factors galore and Android Enterprise
- UEM tools managing Android-powered cars
- Joining the Android Enterprise Experts community
- February was an interesting month for OEMConfig
- Google launch Android Enterprise Recommended for Managed Service Providers
- Migrating from Windows 10 Mobile? Here's why you should consider Android
- AER expands: Android Enterprise Recommended for EMMs
- What I'd like to see from Android Enterprise in 2019
2018
- My top Android apps in 2018
- Year in review: 2018
- MobileIron Cloud R58 supports Android Enterprise fully managed devices with work profiles
- Hands on with the Huawei Mate 20 Pro
- Workspace ONE UEM 1810 introduces support for Android Enterprise fully managed devices with work profiles
- G Suite no longer prevents Android data leakage by default
- Live: Huawei Mate series launch
- How to sideload the Digital Wellbeing beta on Pie
- How to manually update the Nokia 7 Plus to Android Pie
- Hands on with the BQ Aquaris X2 Pro
- Hands on with Sony OEMConfig
- The state of Android Enterprise in 2018
- BYOD & Privacy: Don’t settle for legacy Android management in 2018
- Connecting two Synologies via SSH using public and private key authentication
- How to update Rsync on Mac OS Mojave and High Sierra
- Intune gains support for Android Enterprise COSU deployments
- Android Enterprise Recommended: HMD Global launch the Nokia 3.1 and Nokia 5.1
- Android Enterprise Partner Summit 2018 highlights
- Live: MobileIron LIVE! 2018
- Android Enterprise first: AirWatch 9.4 lands with a new name and focus
- Live: Android Enterprise Partner Summit 2018
- Samsung, Oreo and an inconsistent Android Enterprise UX
- MobileIron launch Android Enterprise work profiles on fully managed devices
- Android P demonstrates Google's focus on the enterprise
- An introduction to managed Google Play
- MWC 2018: Android One, Oreo Go, Android Enterprise Recommended & Android Enterprise
- Enterprise ready: Google launch Android Enterprise Recommended
2017
- Year in review: 2017
- Google is deprecating device admin in favour of Android Enterprise
- Hands on with the Sony Xperia XZ1 Compact
- Moto C Plus giveaway
- The state of Android Enterprise in 2017
- Samsung launched a Note 8 for enterprise
- MobileIron officially supports Android Enterprise QR code provisioning
- Android zero-touch enrolment has landed
- MobileIron unofficially supports QR provisioning for Android Enterprise work-managed devices, this is how I found it
- Hands on with the Nokia 3
- Experimenting with clustering and data replication in Nextcloud with MariaDB Galera and SyncThing
- Introducing documentation on bayton.org
- Goodbye Alexa, Hey Google: Hands on with the Google Home
- Restricting access to Exchange ActiveSync
- What is Mobile Device Management?
- 8 tips for a successful EMM deployment
- Long-term update: the fitlet-RM, a fanless industrial mini PC by Compulab
- First look: the FreedomPop V7
- Vault7 and the CIA: This is why we need EMM
- What is Android Enterprise (Android for Work) and why is it used?
- Introducing night mode on bayton.org
- What is iOS Supervision and why is it used?
- Hands on with the Galaxy TabPro S
- Introducing Nextcloud demo servers
- Part 4 - Project Obsidian: Obsidian is dead, long live Obsidian
2016
- My top Android apps 2016
- Hands on with the Linx 12V64
- Wandera review 2016: 2 years on
- Deploying MobileIron 9.1+ on KVM
- Hands on with the Nextcloud Box
- How a promoted tweet landed me on Finnish national news
- Using RWG Mobile for simple, cross-device centralised voicemail
- Part 3 – Project Obsidian: A change, data migration day 1 and build day 2
- Hands on: fitlet-RM, a fanless industrial mini PC by Compulab
- Part 2 - Project Obsidian: Build day 1
- Part 1 - Project Obsidian: Objectives & parts list
- Part 0 - Project Obsidian: Low power NAS & container server
- 5 Android apps improving my Chromebook experience
- First look: Android apps on ChromeOS
- Competition: Win 3 months of free VPS/Container hosting - Closed!
- ElasticHosts review
- ElasticHosts: Cloud Storage vs Folders, what's the difference?
- Adding bash completion to LXD
- Android N: First look & hands-on
- Springs.io - Container hosting at container prices
- Apple vs the FBI: This is why we need MDM
- Miradore Online MDM: Expanding management with subscriptions
- Lenovo Yoga 300 (11IBY) hard drive upgrade
- I bought a Lenovo Yoga 300, this is why I'm sending it back
- Restricting access to Exchange ActiveSync
- Switching to HTTPS on WordPress
2015
2014
- Is CYOD the answer to the BYOD headache?
- BYOD Management: Yes, we can wipe your phone
- A fortnight with Android Wear: LG G Watch review
- First look: Miradore Online free MDM
- Hands on: A weekend with Google Glass
- A month with Wandera Mobile Gateway
- Final thoughts: Dell Venue Pro 11 (Atom)
- Thoughts on BYOD
- Will 2014 bring better battery life?
- My year in review: Bayton.org
- The best purchase I've ever made? A Moto G for my father
2013
2012
- My Top Android Apps 12/12
- The Nexus 7 saga: Resolved
- Recycling Caps Lock into something useful - Ubuntu (12.04)
- The Nexus 7 saga continues
- From Wows to Woes: Why I won't be recommending a Nexus7 any time soon.
- Nexus7: What you need to know
- Why I disabled dlvr.it links on Facebook
- HTC Sense: Changing the lockscreen icons from within ADW
2011
- Push your Google+ posts to Twitter and Facebook
- Using multiple accounts with Google.
- The "Wn-R48" (Windows on the Cr-48)
- Want a Google+ invite?
- Publishing to external sources from Google+
- Dell Streak review. The Phone/Tablet Hybrid
- BlueInput: The Bluetooth HID driver Google forgot to include
- Pushing Buzz to Twitter with dlvr.it
- Managing your social outreach with dlvr.it
- When Awe met Some. The Cr-48 and Gnome3.
- Living with Google's Cr-48 and the cloud.
- Downtime 23-25/04/2011
- Are you practising "safe surfing"?
- The Virtualbox bug: "Cannot access the kernel driver" in Windows
- Putting tech into perspective
2010
- Have a Google Buzz Christmas
- Root a G1 running Android 1.6 without recovery!
- Windows 7 display issues on old Dell desktops
- Google added the Apps flexibility we've been waiting for!
- Part I: My 3 step program for moving to Google Apps
- Downloading torrents
- Completing the Buzz experience for Google Maps Mobile
- Quicktip: Trial Google Apps
- Quicktip: Save internet images fast
- Turn your desktop 3D!
- Part III - Device not compatible - Skype on 3
- Swype not compatible? ShapeWriter!
- Don't wait, get Swype now!
- HideIP VPN. Finally!
- Google enables Wave for Apps domains
- Aspire One touch screen
- Streamline XP into Ubuntu
- Edit a PDF with Zamzar
- Google offering Gmail addresses in the UK
- Google Wave: Revolutionising blogs!
- Hexxeh's Google Chrome OS builds
- Update: Buzz on Windows Mobile
- Alternatives to Internet Explorer
- Wordress 3.0 is coming!
- Skype for WM alternatives
- Browsing on a (data) budget? Opera!
- Buzz on unsupported mobiles
- Buzz on your desktop
- What's all the Buzz?
- Part II: Device not compatible - Skype on 3
- Part I - Device not compatible - Skype on 3
- Dreamscene on Windows 7
- Free Skype with 3? There's a catch..
Android 15: What's new for enterprise?
Contents
Android 15 launched officially for Pixel on October 15th. This was about a month and a half after the release to AOSP on September 3rd.
It has been a rather odd series of events this year; Pixel typically receives the latest and greatest version of Android in tandem with its release to AOSP, and the marketing and messaging goes out in unison for Android as a whole, but with Pixel's delay it caused something of an anticlimactic debut for AOSP, with most of the Android 15 blogs and announcements only really happening at Pixel's launch.
Hopefully that doesn't become the norm, I'm not a fan of delaying announcements until an OEM - Pixel or otherwise - is ready with their own implementation; I can't imagine Google would have done this if Oppo, Samsung, HMD or others asked for the same.
That said, here we are.
I could have covered this post off for the most-part after the AOSP drop, I chose to wait until Google released their marketing materials. AOSP/developer docs rarely tell the whole story of enterprise support in an Android release, and 15 has been no different; I'd covered pretty much everything I found for AOSP in What's new (so far) for enterprise in Android 15 and so it was the wider Google Play Services and undocumented functionalities that were left to be covered.
The below aims to provide a comprehensive overview of enterprise features, so may skip some items mentioned in the blog from April. Feel free to jump back there (link above) for more general Android 15 features. Let's start with a headline feature.
Private Space
#Android 15 introduces Private Space, the ability for users to protect a selection of apps in a private, additionally-authenticated profile on the device. These applications are isolated - similar to a work profile - from the rest of the applications on the primary parent profile.
When Google announced Private Space with 15, I wrongfully anticipated this to be a mostly non-enterprise feature that wouldn't coexist in the management space. After all, it comes across as the work profile for unmanaged devices, in a way (certainly the tech it's built on tells me this).
But here we are! The multiple work profiles on one device I've been asking for that Google said they'd never support 😁.
Default behaviour for managed devices
#The way this is managed is nuanced, per Google:
The default value for an unmanaged user is false. For users with a device owner set, the default value is true and the device owner currently cannot change it to false. On organization-owned managed profile devices, the default value is false but the profile owner can change it to true via the parent profile to block creating of private profiles on the personal user.
So in other words Private Space is disabled for fully managed devices by default, and cannot be enabled. For work profile-enabled company-owned devices, this can be managed.
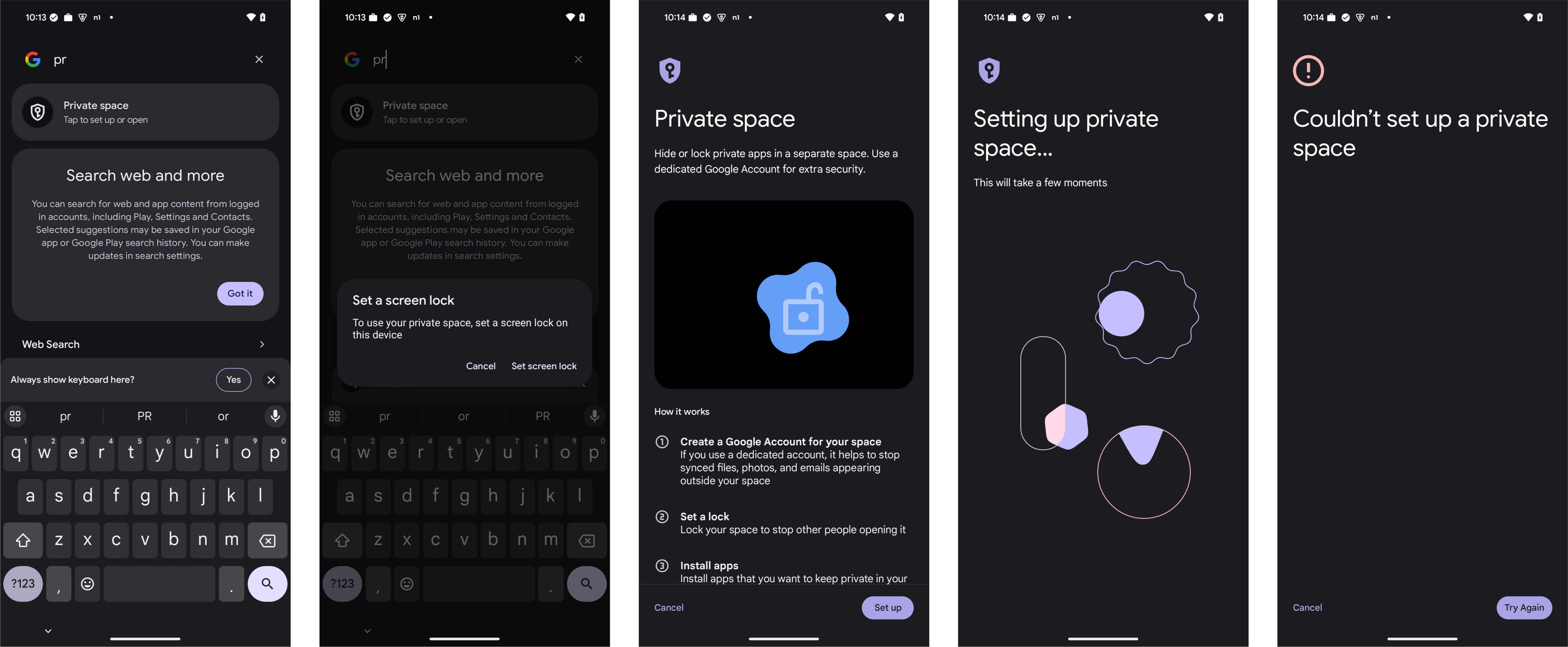
In testing, my fully managed device does indeed fail to create a Private Space, but doesn't indicate why - it simply fails:
An interjection from the DPC to say this isn't possible would tremendously improve the UX.
General management policies in the Private Space
#If you're concerned the Private Space may become a wild-west of hidden app and user activity, fret not! Policies that have previously applied device-wide, such as the installation of apps from unknown sources, are still device-wide. The Private Space adopts these restrictions with no additional management overhead.
Application management in the Private Space
#While it's blocked on fully managed devices (which would be a great use case for a reversed COPE, I'll touch on below), it's very much possible to create a Private Space in COPE and co-exist with the work profile.
Hang on, you may be thinking, doesn't that just mean users can add apps to a Private Space if they're not permitted to add them to their personal profile?
As it turns out, no.
Android 15 for business introduces the ability to apply a limited set of security restrictions to specific apps outside the Work Profile. Existing personal app allowlist or blocklist policies can be extended to the new private space feature. In the future, additional privacy preserving security configurations for core apps will be introduced and made backward compatible with Android 15.
The policies applied for permitted or blocked apps in a COPE deployment scenario also apply to the Private Space for AMAPI enrolments. CustomDPC EMMs will gain the same functionality at a later date (no ETA provided by Google).
The case for Private Space on fully managed devices
#It popped up in the AE Customer Community and I think it's worth further discussion:
I quite like the prospect of reversing the existing COPE model to fully manage the device, but have an inaccessible profile (Private Space) for workers. Maximum control of the device with a lower-perceived, but potentially acceptable level of privacy for workers. As indicated for pool/shared devices where you auth, but can pop a few personal apps for break/other reasons the admins can ultimately remove at will.. I like it.
Private Space has obviously not been enabled on fully managed devices due to the privacy concerns, I would assume, previously associated with work profiles on fully managed devices. Furthermore, I would expect there are nuances within a fully managed and dedicated use cases (which are mostly shared under the Device Owner (DO) ownership model) that would render this feature incompatible and possibly cause problems. It's also likely a lot of work resurrecting deprecated approaches to cross-profile policies and such that would bring this much closer to pre-11 Android fully managed devices with work profiles..
..but it could be disabled by default, as it is for fully managed devices, and in organisations that want to allow a reverse-COPE wherein personal apps and data live in a separately encrypted, isolated container with limited cross-profile oversight (personal usage policies would have to apply on fully managed only, just for Private Space), it could work.
Supporting this would further add the flexibility organisations want as the personally-owned vs company-owned debate rages on amongst admins.
What Private Space isn't
#Fort Knox.
Unfortunately, and Google to their credit do highlight this, Private Space is still a profile running within Android; the applications installed in this space can be detected with relative ease and so although it makes it extremely difficult to access app data, it doesn't prevent the determined from piecing together a perception of someone based on the apps they're hiding away. Assuming they have access to the device.

Giant Private Space icons added in PACKAGE SEARCH for emphasis only.
I do feel it could be improved, for example with the work profile implementation there are policies that prevent an app inside the profile from locating applications outside of it, so if I run PACKAGE SEARCH within a work profile, I cannot see the user apps installed in the parent profile.
I appreciate this is not 1:1, effectively asking apps in the parent profile to be blocked from running package manager searches on any packages flagged against the Private Space, but I'd like to believe it's possible.
So that's Private Space. Next? COPE:
Enhancements to company-owned work profiles (COPE)
#Google has been busy this year boosting the functionality of the company-owned work profile deployment scenario, and it's a trend I'm here for! Still struggling with the loss of work profiles on fully managed devices, every small bump in functionality that regains some control over the parent (personal) profile of a company-owned device is nothing short of a treat.
Here's what's new in Android 15:
Control of parent profile screen settings in company-owned work profile deployment scenarios
#For company-owned devices running work profile, the following previously fully managed-only restrictions can be applied to devices:
- Screen off timeout (not to be confused with time to lock, which still supersedes this in terms of hierarchy)
- Screen brightness (the actual brightness or the screen)
- Screen brightness mode (manual or automatic)
Google announced these as power management controls, I suppose they could contribute to lower power consumption at the cost of user satisfaction if you were to enforce fixed brightness on personal-use devices. They could also contribute to significantly higher power consumption.
I'm not sure what use cases were identified here that led to it being framed this way, but I imagine this could be a frustrating experience for knowledge workers if not implemented by organisations appropriately; who could use a device outside on a Summer's day while being limited to 30% brightness? Who would want to check an incoming call or notification in the middle of the night with a screen that doesn't adapt to the ambient conditions of the room, but rather turn on at 100% brightness?
In contrast, enforcing automatic would be a sensible default. Be mindful if deploying fixed brightness or brightness modes to personal-use devices.
Application defaults in the personal profile for company-owned work profile devices
#Extending further control of the personal side of the device for COPE deployments, Google is allowing organisations in Android 15 to set default applications for the dialler, messaging app, and browser.
To be absolutely clear, these defaults will be whatever the Android device ships with, so it wouldn't be possible to set Edge as a default in the personal profile across a managed estate. Rather, Samsung may default to Samsung Internet, Pixel to Chrome, etc. This avoids a potential privacy risk in allowing organisations to set their preferred apps as the personal default, complete with whatever identifying information and usage data they may be able to extract from the personal profile and into corporate servers.
By implementing these defaults, organisations prevent the opposite scenario where a user may choose to use a non-recommended (or downright potentially harmful app) as their default in the personal profile, and open the device up to additional security risks.
Google states these must be initially configured at provisioning time. That is to say set in the policy applied at the time of enrolment. If being set retrospectively, as would be required for any existing device updating to Android 15, this can be done through the use of allowlists:
The default messaging app can be set at any time. To enforce OEM defaults for dialler and browser after set up, this control must be combined with an app allowlist.
These do not apply to Android 15's Private Space (discussed below), as these applications should not be present in the Space to begin with.
Security & privacy changes
#Android 15 additionally introduces a fair few security improvements also, some of which include:
Migration of events from logcat to SecurityLog
#From 15 we'll start seeing more information provided to SecurityLog. For those who've debugged an Android device under management, unless you're working with the device directly, pulling & reviewing logcat can be a pain.
As SecurityLog, along with NetworkLog, can be fetched through the EMM, this offers a much simpler option and ongoing review of the respective logs.
The intention is to more closely align with NIAP requirements, and allow for quick review of administrative device changes.
In addition, Android adds an event for the backup service being toggled by an admin which will also now be available for admins from 15 when pulling security logs.
Improvements to Factory Reset Protection
#Though there are no enterprise-specific changes to factory reset protection, I believe it's important to highlight some changes made to how it works within the context of an enterprise device, namely:
- Enabling OEM unlock in developer settings will no longer deactivate FRP
- Bypassing the setup wizard, which isn't uncommon for dedicated devices/OEMs, will no longer deactivate FRP.
- Adding accounts, passwords, and applications will no longer be possible while FRP is active
Going forward it will be evermore important to ensure both FRP, and enterprise FRP (wherein organisations set the allowlisted Google accounts), are properly maintained and processes correctly followed for resetting devices, if the EMM does not turn FRP off by default (hi, Omnissa..)
A bump to minimum SDK version for installation of apps
#As expected, the restriction on installing applications targeting very old versions of Android is getting a bump. In Android 15 it will no longer be possible to install apps targeting API level 23 - Android Marshmallow / 6.0 - or older. Only apps that target Android 7.0 - API level 24 - or later will be permitted.
jason@MBP Downloads % adb install app-release.apk
Performing Streamed Install
adb: failed to install app-release.apk: Failure [INSTALL_FAILED_DEPRECATED_SDK_VERSION: App package must target at least SDK version 24, but found 23]Just as last year, we're talking about applications targeting a version of Android 10+ years old. While some organisations with line-of-business apps that haven't seen an update in half a decade may balk at the idea of getting their applications updated or rewritten, the justification behind this limitation is solid - security. Where apps targeting <6.0 were able to abuse the old permissioning system (pre-runtime!), apps targeting 7.0 are still able to abuse device administrator and similar APIs. This isn't something you want potentially leveraged directly or indirectly on your managed estate.
Restrictions on device identifiers for personally-owned devices
#From Android 15, applications with the permission android.permission.MANAGE_DEVICE_POLICY_CERTIFICATES will be able to fetch getEnrollmentSpecificId, which is an enrolment-specific, unique device identifier that persists across re-enrolments when done so into the same deployment scenario (i.e. fully managed or personally-owned work profile), by the same vendor agent, into the same enterprise (organisation/bind).
It is an alternative to identifiers such as IMEI and serial number, which Google no longer grants access to for applications without the appropriate device or profile owner role, or DELEGATION_CERT_INSTALL via policy, and becomes the default and only option for fetching a unique device identifier for personally-owned work profile devices in future.
To be clear - applications in a personally-owned work profile deployment up to now with the delegated permission of DELEGATION_CERT_INSTALL have been able to fetch a device serial number with relative ease, something that defeats the entire purpose of restricting access to the identifiers, considered to be personally identifiable information, in the first place. That loophole is closing.
At time of writing there's a bug in 15 - on the Pixel 9 Pro XL at least - preventing delegated scopes from being retrieved by managed apps within the work profile. It works fine in the parent profile. If you'd like to validate this yourself, here's a snippet to call from within an application:
val dpm = context.getSystemService(Context.DEVICE_POLICY_SERVICE) as DevicePolicyManager
val delegatedScopes = dpm.getDelegatedScopes(null, context.packageName)Security exceptions for sensors-related permissions
#From 15, device admins targeting API level 35, including DPCs and device admin role holders, will begin throwing security exceptions when attempting to set permissions for some sensors-specific permissions, including:
- Manifest.permission.ACCESS_FINE_LOCATION
- Manifest.permission.ACCESS_BACKGROUND_LOCATION
- Manifest.permission.ACCESS_COARSE_LOCATION
- Manifest.permission.CAMERA
- Manifest.permission.RECORD_AUDIO
- Manifest.permission.RECORD_BACKGROUND_AUDIO
- Manifest.permission.ACTIVITY_RECOGNITION
- Manifest.permission.BODY_SENSORS
The two scenarios where this is expected to happen is:
- The calling agent is a profile owner, rather than a device owner (so work profile deployments, not fully managed)
- The agent is a device owned on a fully managed device, but has EXTRA_PROVISIONING_GRANT_OPT_OUT set during the provisioning process.
While this has been in place since Android 12, previously this would have silently failed. In future security exceptions will be triggered which should make it easier to debug.
New restrictions
#It wouldn't be an Android release unless we saw a few new features to manage. Here's the run-down:
Content protection policy
#The content protection policy offers admin control of a new feature for real-time threat detection within the Google Play Protect arsenal of protections covered in a prior security blog from February.
For Pixel devices, the toggle for this is in Settings > Security & privacy > More security & privacy > Scanning for deceptive apps.
It is buried deep in Settings.
When the configuration is unspecified, currently the respective toggle is off for fully managed devices. Switching to enforced then enables the setting.
This is a great approach, sympathetic to the feedback its announcement generated from administrators already frustrated with overbearing Google Play Protect policies that cannot be disabled (full disclosure, I'm generally in favour of GPP, but I'm aware of the problems it causes for some organisations), while allowing its use for organisations that feel they need it.
For EMM vendors, this is already present in AMAPI as contentProtectionPolicy under AdvancedSecurityOverrides.
Android 15 also introduces the permission android.permission.MANAGE_DEVICE_POLICY_CONTENT_PROTECTION for apps which are not the device or profile owner to be able to interface with this API.
Google Play Protect app scanning changes
#In a related note, in September 2024 Google made a considerable change that will placate any organisation deploying sideloaded enterprise applications, including those installed via the EMM DPC (agent), internal services, or sideloaded in more traditional ways. These applications will no longer be sent to Google for scanning, and no longer prompt end users to take any action against them unless they are known to Google to be potentially harmful. More information here.
Disallow NFC radio
#As it says on the tin. If you're thinking "Don't we already have an API for NFC?" Yes we do, but that's to control the beaming of data between devices. This is a full on radio disable and will probably live under DeviceRadioState in AMAPI at some point later.
This appears to be a natural progression from the earlier DISALLOW_CHANGE_NEAR_FIELD_COMMUNICATION_RADIO which prevents the turning on/off NFC in settings.
eSIM management
#eSIM has been given a respectable amount of attention in 15. Here's what's new:
Disallow SIM Globally
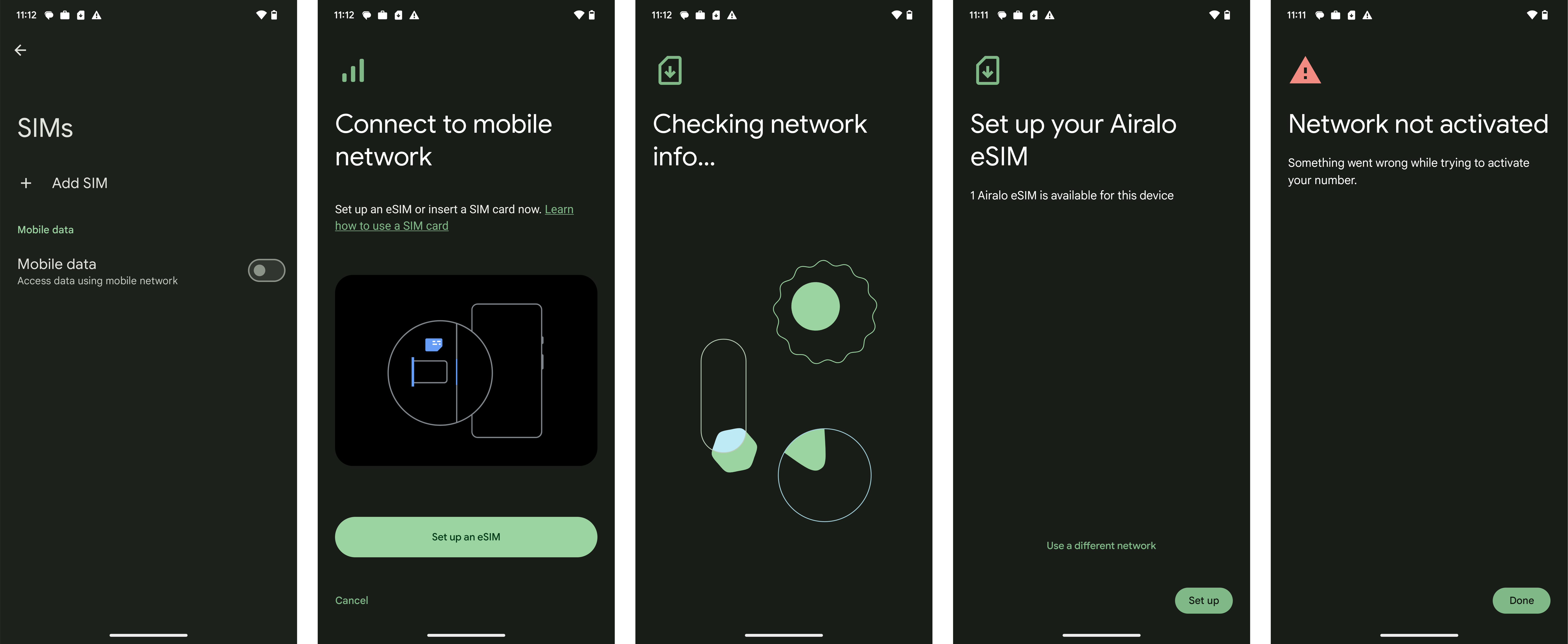
#The API I found earlier in the year appears to be a subset of a larger eSIM management framework being introduced with Android 15. For completeness, as the earlier post was quite light, here's what Disallow SIM Globally actually means:
Available for both fully managed and company-owned work profile devices, disallow SIM globally (DISALLOW_SIM_GLOBALLY) is an eSIM restriction to globally prevent the user download of eSIMs to a device.
While I earlier assumed it may have been globally disabling cellular, killing the radio and hiding the respective settings, status bar messaging, and so forth (useful particularly for lower-cost tablets that often come with cellular) this is not the case.
In my testing, with the restriction enabled I was able to go into settings, begin eSIM setup with the scan of a QR code, and only then did it prevent setup with a generic error message that suggests there's a problem with the eSIM rather than a policy restriction in place:
The experience could be improved dramatically here just with the addition of management UI, and preferably earlier in the process of adding an eSIM, also.
Expanding 9.0 APIs for eSIM management
#More broadly Android 15 introduces eSIM configuration capabilities via EMM. Based on what I've been able to find, eSIM management is directly associated with eSIM subscription management introduced in Android 9.0, and has been expanded in 15 to allow remote configuration via EMM, or the appropriate permission:
Starting from
Android Build.VERSION_CODES.VANILLA_ICE_CREAM, if the caller has theandroid.Manifest.permission#MANAGE_DEVICE_POLICY_MANAGED_SUBSCRIPTIONSpermission or is a profile owner or device owner, then the downloaded subscription will be managed by that caller. In case the caller is device owner or profile owner of an organization-owned device,switchAfterDownloadcan be set to true to automatically enable the subscription after download. If the caller is a profile owner on non organization owned deviceswitchAfterDownloadshould be false otherwise the operation will fail withEMBEDDED_SUBSCRIPTION_RESULT_ERROR.
It would appear EMM vendors with either custom DPCs or via AMAPI will be able to lean into this API from 15 to add and remove EUICC subscriptions. Neat.
Further, it will even support partial payloads! Providing the device has already been registered with an eSIM on a carrier's SMDP+ server, it will allow the device to reach out to that server, declare itself and get it's eSIM. This has the potential to significantly simplify eSIM management, reducing the number of eSIM configurations necessary for large deployments.
Personally-owned device users will be able to remove the configured eSIM, though for company-owned devices, the additional policy DISALLOW_CONFIG_MOBILE_NETWORKS can be set to ensure eSIMs aren't deleted.
Disallow assist content
#This restriction allows administrators to prevent privileged apps, such as Assistant, from receiving contextual device information. These include screenshots, package names, and more. Useful for admins wishing to reduce the sprawl of information access privileged apps can have. This is scope-specific, so on fully managed devices will apply device-wide, but on profile-enabled devices restricts only to the managed profile.
Circle to search
#Relatively straightforward, an enterprise API is being introduced to lock down circle to search - one of the most hyped up features I've seen in a long time.. but probably not something organisations want accidentally invoking on dedicated devices while customers try to order a Big Mac! This is a nice continuation of assist content above, limiting the amount of data being sent to Google services.
Widget management is back?!
#With Android 15, setKeyguardDisabledFeatures has been expanded with widget management to coincide with the re-introduction of lockscreen widgets for tablet devices. At this time it appears to only apply to widgets in managed profiles, with Google explicitly stating:
..the profile owner of an organization-owned managed profile can set
KEYGUARD_DISABLE_WIDGETS_ALLwhich affects the parent user when called on the parent profile.
More testing is needed to determine why this isn't available for fully managed devices.
To note for wider context, lock screen widgets were removed way back in 5.0 citing, if I remember correctly, low use. With the recent focus on tablets, and Apple adding their own, Google clearly figured they matter again!
Other changes and requirements for 15
#Rounding off what's new, here are some additional features that don't fit into the above categories:
Platform signed permission management
#When a vendor works with an OEM to get their application platform singed, the application is granted all system-level permissions available on the device. As you can imagine, that is an unprecedented level of device access to data and services reserved normally for only the OEM system apps, and Google's preloaded suite of applications.
In Android 15, Google is introducing system permission management, allowing OEMs to grant or deny permissions to signed applications that allows for the considerable down-scoping of access of a signed app to only the explicit permissions required to function. This won't apply to system apps bundled with a set of permissions in the OEM system image, but should permissions change in a later system app update, these permissions would also be denied automatically unless allowlisted in the respective system configuration.
There's an additional config to allow platform-signed shared UIDs for non-system applications that have additionally previously required access to this.
There are new alerts in logging to determine the permissions applications are no longer retaining access to, which vendors should already start looking at today to avoid loss of functionality.
Knowing how many enterprise vendors lean on platform signature permissions today (basically most EMMs, several SaaS products, etc), this has the potential to cause headaches as 15 lands on devices, unless OEMs and vendors work together proactively to avoid this.
Screen recording improvements
#If you're like me and record your screen far too often to demonstrate anything from a device feature to a bug, user guides and more, you'll be pleased to hear the previously Pixel-only feature introduced in Android 14 is coming to the wider ecosystem with the 15 update. Now users can limit screen sharing to just the app they want to show, and no longer fret on the possibility to showing something that may not be appropriate for the context.
Continuing the theme of recording, this is not so much an enterprise feature in and of itself explicitly, but Android 15 will alert apps when the screen is being recorded, allowing them to hide contents.
I can imagine this might be useful for enterprise applications across the board to bolster DLP (data loss prevention), and based on murmurings in Tech News, Google is testing restrictions in Chrome to prevent sensitive information from being recorded (addresses, card details, passwords, etc).
Broader system update visibility
#From 15, applications granted the permission android.permission.MANAGE_DEVICE_POLICY_QUERY_SYSTEM_UPDATES will be able to obtain information about a pending system update. This softens the current requirements that an application be a device or profile owner in order to fetch this information.
What this doesn't do, unfortunately, is offer any more information about the update(s) available. Today we can see an update is available and that it's a security update. This API needs to be updated to show -
- build info,
- size,
- how long it's been available (not just when first detected), - SPL/Android version
All of this is offered either through GOTA, Google's OTA management server many OEMs are encouraged to leverage (some don't of course, consider e-FOTA from Samsung, or HMD's new FOTA platform), or the build fingerprint of the package itself.
Check MTE status
#Expanding on the options for getting and setting MTE policies in Android 14, in 15 it will now be possible to merely query the current state (evidently something that should have, but didn't, quite make it to the 14 release!)
Deeper dedicated device experience management
#With Better Together Enterprise, AKA the new customer signup flow, Google is introducing a new provisioning option for dedicated devices, in addition to PERSONAL_USAGE_ALLOWED and PERSONAL_USAGE_DISALLOWED, Google are introducing a third allowPersonalUsage AMAPI enrolment token configuration option of DEDICATED_DEVICE.
That alone isn't an Android 15 feature, but an accompanying flag OEMs can set from 15 within the device software declaring it a dedicated device should give many dedicated device-based organisations a reason to take note.
Such distinguishing features between knowledge worker devices and the new dedicated devices flag include:
- Setup Wizard customisation
- Default restrictions within the Android experience
Managing dedicated devices, which have always been treated identically to any other consumer Android device on the market, has been a frustrating experience; devices an end user would never use shouldn't need to configure accounts, access Google Play, deal with all the setup wizard interruptions around privacy callouts and more. I'd really hoped the EDLA licence would have solved a lot of problems, but so many years now after its introduction the differentiation is still minimal from MADA.
Fortunately it looks like Google are taking another approach. Unfortunately a few years too late for the almost 5 years I supported dedicated devices on a daily basis, but I look forward to future projects benefiting from these changes.
What didn't make it
#These didn't make it today, but may pop up in a QPR or future Android version release:
Dedicated document preview app
#In the earlier Android 15 article I referenced a new mandate for OEMs to include a document viewing app, saying:
The absence of a document preview application for managed devices has been quite a noisy complaint from organisations for many years, overshadowed only by missing camera &/ gallery applications. None of these apps have been mandated by Google for the fully managed/work profile user experience, and so the common trend is to see them simply not added.
It appears Google changed their mind on this, which is not uncommon across releases by any means. The 4 or so years I spent working on Android hardware I saw many instances where proposals ultimately didn't make it - sometimes due to an internal direction change, sometimes pressure from OEMs. Either way it looks like that has happened here also, so we'll go another year without a dedicated document preview app.
Skip adding personal accounts during company-owned work profile provisioning
#In the earlier article I referenced a change I interpreted as offering the possibility for organisation admins to set provisioning-time configurations that skip the add-account flow during managed provisioning of a company-owned work profile device. This would have been a small quality-of-life improvement that would shorten down the COPE provisioning time for scenarios where either:
- users don't wish to immediately add a personal account and complete the full setup of their device, or
- where devices are perhaps staged elsewhere and sent to users registered and ready to go.
Alas, we won't see this in 15.
With that said, it has been submitted as a feature request to Google! In future, we may see a provisioning time option similar to allow the skipping of personal setup, perhaps palmed off to deferred setup, or triggered on the first boot after provisioning completes.
Why would it be useful? Mostly echoing the above - organisations still pre-provision devices, even those on zero-touch, before sending them out to users in an effort to reduce the hand-holding needed for setting up a device. With the COPE model there are privacy and ethical considerations preventing the setup of a personal profile with a user's account, and obviously skipping the account setup renders the setup process less intuitive, even with deferred setup.
Ensuring the work side is sorted, then shipping it out to an end user to add their Google account and go I find quite an enticing option in this and similar scenarios.
Disallow Thread Network
#At the time of writing, Google developer docs still don't have an entry for the Thread API, but reference it in the UserManager docs as an unlinked entity. At some point the link to UserManager should go to the right place.
In the meantime it appears the source for CTS contains a test for this API. From that it's somewhat clear what this API is intended for, and we no longer need to assume:
// If the device doesn't support Thread then as long as the user restriction doesn't throw an
// exception when setting - we can assume it's fine
@RequireFeature("android.hardware.thread_network")
@RequiresFlagsEnabled(Flags.FLAG_THREAD_USER_RESTRICTION_ENABLED)If that's too ambiguous, the CTS docs reference the hardware feature android.hardware.thread_network, which additional source commits tie directly to Thread network support.
It looks like it'll be a relatively straightforward boolean (on/off) restriction allowing managed devices to interface with thread network devices when it's added to Android at a later date.
Did I miss anything?
#If I did, you know where to find me.
Articles
2026
2025
- Google Play Protect is now the custom DPC gatekeeper, and everyone is a threat by default
- 12 deliveries of AE-mas (What shipped in Android Enterprise in 2025)
- The 12 AE requests of Christmas (2025 Edition)
- RCS Archival and you: clearing up the misconceptions
- Device Trust from Android Enterprise: What it is and how it works (hands-on)
- Android developer verification: what this means for consumers and enterprise
- AMAPI finally supports direct APK installation, this is how it works
- The Android Management API doesn't support pulling managed properties (config) from app tracks. Here's how to work around it
- Hands-on with CVE-2025-22442, a work profile sideloading vulnerability affecting most Android devices today
- AAB support for private apps in the managed Google Play iFrame is coming, take a first look here
- What's new (so far) for enterprise in Android 16
2024
- Android 15: What's new for enterprise?
- How Goto's acquisition of Miradore is eroding a once-promising MDM solution
- Google Play Protect no longer sends sideloaded applications for scanning on enterprise-managed devices
- Mobile Pros is moving to Discord
- Avoid another CrowdStrike takedown: Two approaches to replacing Windows
- Introducing MANAGED SETTINGS
- I'm joining NinjaOne
- Samsung announces Knox SDK restrictions for Android 15
- What's new (so far) for enterprise in Android 15
- Google quietly introduces new quotas for unvalidated AMAPI use
- What is Play Auto Install (PAI) in Android and how does it work?
- AMAPI publicly adds support for DPC migration
- How do Android devices become certified?
2023
- Mute @channel & @here notifications in Slack
- A guide to raising better support requests
- Ask Jason: How should we manage security and/or OS updates for our devices?
- Pixel 8 series launches with 7 years of software support
- Android's work profile behaviour has been reverted in 14 beta 5.3
- Fairphone raises the bar with commitment to Android updates
- Product files: The DoorDash T8
- Android's work profile gets a major upgrade in 14
- Google's inactive account policy may not impact Android Enterprise customers
- Product files: Alternative form factors and power solutions
- What's new in Android 14 for enterprise
- Introducing Micro Mobility
- Android Enterprise: A refresher
2022
- What I'd like to see from Android Enterprise in 2023
- Thoughts on Android 12's password complexity changes
- Google Play target API requirements & impact on enterprise applications
- Sunsetting Discuss comment platform
- Google publishes differences between Android and Android Go
- Android Go & EMM support
- Relaunching bayton.org
- AER dropped the 3/5 year update mandate with Android 11, where are we now?
- I made a bet with Google (and lost)
2020
- Product files: Building Android devices
- Google announce big changes to zero-touch
- VMware announces end of support for Device Admin
- Google launch the Android Enterprise Help Community
- Watch: An Android Enterprise discussion with Hypergate
- Listen again: BM podcast #144 - Jason Bayton & Russ Mohr talk Android!
- Google's Android Management API will soon support COPE
- Android Enterprise in 11: Google reduces visibility and control with COPE to bolster privacy.
- The decade that redefined Android in the enterprise
2019
- Why Intune doesn't support Android Enterprise COPE
- VMware WS1 UEM 1908 supports Android Enterprise enrolments on closed networks and AOSP devices
- The Bayton 2019 Android Enterprise experience survey
- Android Enterprise Partner Summit 2019 highlights
- The Huawei ban and Enterprise: what now?
- Dabbling with Android Enterprise in Q beta 3
- Why I moved from Google WiFi to Netgear Orbi
- I'm joining Social Mobile as Director of Android Innovation
- Android Enterprise in Q/10: features and clarity on DA deprecation
- MWC 2019: Mid-range devices excel, 5G everything, form-factors galore and Android Enterprise
- UEM tools managing Android-powered cars
- Joining the Android Enterprise Experts community
- February was an interesting month for OEMConfig
- Google launch Android Enterprise Recommended for Managed Service Providers
- Migrating from Windows 10 Mobile? Here's why you should consider Android
- AER expands: Android Enterprise Recommended for EMMs
- What I'd like to see from Android Enterprise in 2019
2018
- My top Android apps in 2018
- Year in review: 2018
- MobileIron Cloud R58 supports Android Enterprise fully managed devices with work profiles
- Hands on with the Huawei Mate 20 Pro
- Workspace ONE UEM 1810 introduces support for Android Enterprise fully managed devices with work profiles
- G Suite no longer prevents Android data leakage by default
- Live: Huawei Mate series launch
- How to sideload the Digital Wellbeing beta on Pie
- How to manually update the Nokia 7 Plus to Android Pie
- Hands on with the BQ Aquaris X2 Pro
- Hands on with Sony OEMConfig
- The state of Android Enterprise in 2018
- BYOD & Privacy: Don’t settle for legacy Android management in 2018
- Connecting two Synologies via SSH using public and private key authentication
- How to update Rsync on Mac OS Mojave and High Sierra
- Intune gains support for Android Enterprise COSU deployments
- Android Enterprise Recommended: HMD Global launch the Nokia 3.1 and Nokia 5.1
- Android Enterprise Partner Summit 2018 highlights
- Live: MobileIron LIVE! 2018
- Android Enterprise first: AirWatch 9.4 lands with a new name and focus
- Live: Android Enterprise Partner Summit 2018
- Samsung, Oreo and an inconsistent Android Enterprise UX
- MobileIron launch Android Enterprise work profiles on fully managed devices
- Android P demonstrates Google's focus on the enterprise
- An introduction to managed Google Play
- MWC 2018: Android One, Oreo Go, Android Enterprise Recommended & Android Enterprise
- Enterprise ready: Google launch Android Enterprise Recommended
2017
- Year in review: 2017
- Google is deprecating device admin in favour of Android Enterprise
- Hands on with the Sony Xperia XZ1 Compact
- Moto C Plus giveaway
- The state of Android Enterprise in 2017
- Samsung launched a Note 8 for enterprise
- MobileIron officially supports Android Enterprise QR code provisioning
- Android zero-touch enrolment has landed
- MobileIron unofficially supports QR provisioning for Android Enterprise work-managed devices, this is how I found it
- Hands on with the Nokia 3
- Experimenting with clustering and data replication in Nextcloud with MariaDB Galera and SyncThing
- Introducing documentation on bayton.org
- Goodbye Alexa, Hey Google: Hands on with the Google Home
- Restricting access to Exchange ActiveSync
- What is Mobile Device Management?
- 8 tips for a successful EMM deployment
- Long-term update: the fitlet-RM, a fanless industrial mini PC by Compulab
- First look: the FreedomPop V7
- Vault7 and the CIA: This is why we need EMM
- What is Android Enterprise (Android for Work) and why is it used?
- Introducing night mode on bayton.org
- What is iOS Supervision and why is it used?
- Hands on with the Galaxy TabPro S
- Introducing Nextcloud demo servers
- Part 4 - Project Obsidian: Obsidian is dead, long live Obsidian
2016
- My top Android apps 2016
- Hands on with the Linx 12V64
- Wandera review 2016: 2 years on
- Deploying MobileIron 9.1+ on KVM
- Hands on with the Nextcloud Box
- How a promoted tweet landed me on Finnish national news
- Using RWG Mobile for simple, cross-device centralised voicemail
- Part 3 – Project Obsidian: A change, data migration day 1 and build day 2
- Hands on: fitlet-RM, a fanless industrial mini PC by Compulab
- Part 2 - Project Obsidian: Build day 1
- Part 1 - Project Obsidian: Objectives & parts list
- Part 0 - Project Obsidian: Low power NAS & container server
- 5 Android apps improving my Chromebook experience
- First look: Android apps on ChromeOS
- Competition: Win 3 months of free VPS/Container hosting - Closed!
- ElasticHosts review
- ElasticHosts: Cloud Storage vs Folders, what's the difference?
- Adding bash completion to LXD
- Android N: First look & hands-on
- Springs.io - Container hosting at container prices
- Apple vs the FBI: This is why we need MDM
- Miradore Online MDM: Expanding management with subscriptions
- Lenovo Yoga 300 (11IBY) hard drive upgrade
- I bought a Lenovo Yoga 300, this is why I'm sending it back
- Restricting access to Exchange ActiveSync
- Switching to HTTPS on WordPress
2015
2014
- Is CYOD the answer to the BYOD headache?
- BYOD Management: Yes, we can wipe your phone
- A fortnight with Android Wear: LG G Watch review
- First look: Miradore Online free MDM
- Hands on: A weekend with Google Glass
- A month with Wandera Mobile Gateway
- Final thoughts: Dell Venue Pro 11 (Atom)
- Thoughts on BYOD
- Will 2014 bring better battery life?
- My year in review: Bayton.org
- The best purchase I've ever made? A Moto G for my father
2013
2012
- My Top Android Apps 12/12
- The Nexus 7 saga: Resolved
- Recycling Caps Lock into something useful - Ubuntu (12.04)
- The Nexus 7 saga continues
- From Wows to Woes: Why I won't be recommending a Nexus7 any time soon.
- Nexus7: What you need to know
- Why I disabled dlvr.it links on Facebook
- HTC Sense: Changing the lockscreen icons from within ADW
2011
- Push your Google+ posts to Twitter and Facebook
- Using multiple accounts with Google.
- The "Wn-R48" (Windows on the Cr-48)
- Want a Google+ invite?
- Publishing to external sources from Google+
- Dell Streak review. The Phone/Tablet Hybrid
- BlueInput: The Bluetooth HID driver Google forgot to include
- Pushing Buzz to Twitter with dlvr.it
- Managing your social outreach with dlvr.it
- When Awe met Some. The Cr-48 and Gnome3.
- Living with Google's Cr-48 and the cloud.
- Downtime 23-25/04/2011
- Are you practising "safe surfing"?
- The Virtualbox bug: "Cannot access the kernel driver" in Windows
- Putting tech into perspective
2010
- Have a Google Buzz Christmas
- Root a G1 running Android 1.6 without recovery!
- Windows 7 display issues on old Dell desktops
- Google added the Apps flexibility we've been waiting for!
- Part I: My 3 step program for moving to Google Apps
- Downloading torrents
- Completing the Buzz experience for Google Maps Mobile
- Quicktip: Trial Google Apps
- Quicktip: Save internet images fast
- Turn your desktop 3D!
- Part III - Device not compatible - Skype on 3
- Swype not compatible? ShapeWriter!
- Don't wait, get Swype now!
- HideIP VPN. Finally!
- Google enables Wave for Apps domains
- Aspire One touch screen
- Streamline XP into Ubuntu
- Edit a PDF with Zamzar
- Google offering Gmail addresses in the UK
- Google Wave: Revolutionising blogs!
- Hexxeh's Google Chrome OS builds
- Update: Buzz on Windows Mobile
- Alternatives to Internet Explorer
- Wordress 3.0 is coming!
- Skype for WM alternatives
- Browsing on a (data) budget? Opera!
- Buzz on unsupported mobiles
- Buzz on your desktop
- What's all the Buzz?
- Part II: Device not compatible - Skype on 3
- Part I - Device not compatible - Skype on 3
- Dreamscene on Windows 7
- Free Skype with 3? There's a catch..